I am creating a DevOps pipeline for a NodeJs app which i am containerizing as a Docker Image in ACR and deploying it as a ContainerApp in Azure.
I have the following permissions in subscription : > User Access Administrator ( cannot be given more elevated permissions other than this)
I have already created a App Registration -> AppReg1- which i will patch the containerapp url in the pipleline
For deploying from ACR, I am writing a pipeline job as a bash script:
variables:
# Container registry service connection established during pipeline creation
armDeploymentServiceConnection: 'appdeploy1' //passing the service connection name here
- stage: DeployContainerApp
displayName: Deploy the Image as a Container app
jobs:
- job: DeployContainerApp
displayName: Deploy Container App Job
steps:
- task: AzureCLI@2
inputs:
azureSubscription: $(armDeploymentServiceConnection) //passing service connection name
scriptType: 'bash'
scriptLocation: 'inlineScript'
inlineScript: |
az --version
az account show
echo "containerapp will be created"
az ad app show --id $(AppReg1ClientId) --query id | jq -r . //error line throwing insufficient privileges
in the inputs: I have created a ARM type service connection with manual Service principal defined
inputs: azureSubscription:**armDeploymentServiceConnection**: //Here I am passing the ServiceConnection which i have created in manual mode:
The SP i used for this Service connection appdeploy1 is created with the role contributor before hand
az ad sp create-for-rbac --scopes /subscriptions/xxxx --role Contributor --name **appSP**
This SP leads to a additional AppRegistration ex->appSP. I am using this SP only for the inline script
When i run the pipeline, this line throws this error where i m trying to get the object id of the registration AppReg1 where i am going to register my containerApp:
az ad app show --id $(AppReg1ClientId) --query id | jq -r .
ERROR: Insufficient privileges to complete the operation.
Since i created the service principal with the role contributor and created the ServiceConnection with that principal appSP i thought this step will succeed:
- task: AzureCLI@2
inputs:
azureSubscription: $(armDeploymentServiceConnection)
but this line throws error
inlineScript: | az ad app show --id $(APP_REG_CLIENT_ID) --query id | jq -r . //error line
I am not sure, what is missing here? Can anyone please help?
CodePudding user response:
Service connections are created under subscription/resource group, as the contributor, it owns Grants full access to manage all resources in the subscription. However, App exists in Azure AD so you need enough permission in AAD to list it. Since they are in different scope, you need to sign in as the AAD identity then run the 'az ad app show --id' command.
Please kindly try to use things like this to have a try:
- task: AzureKeyVault@1
inputs:
ConnectedServiceName: **
KeyVaultName: **
SecretsFilter: 'secretUser,secretPassword'
RunAsPreJob: true
- pwsh:
az login -u $(secretUser) -p $(secretPassword)
az --version
az account show
echo "containerapp will be created"
az ad app show --id *** --query id | jq -r
You could also try to add the secrets 'secretUser and secretPassword' in libarary-variable group and use it in your yaml for singing in as a user.
Hope this could help.
CodePudding user response:
Insufficient privileges to complete the operation:
This error means that the service principal has no access to AAD application when running the commnad: az ad app show
When you grant the Contributor Role to your service principal, it is at Azure Subscription Level instead AAD.
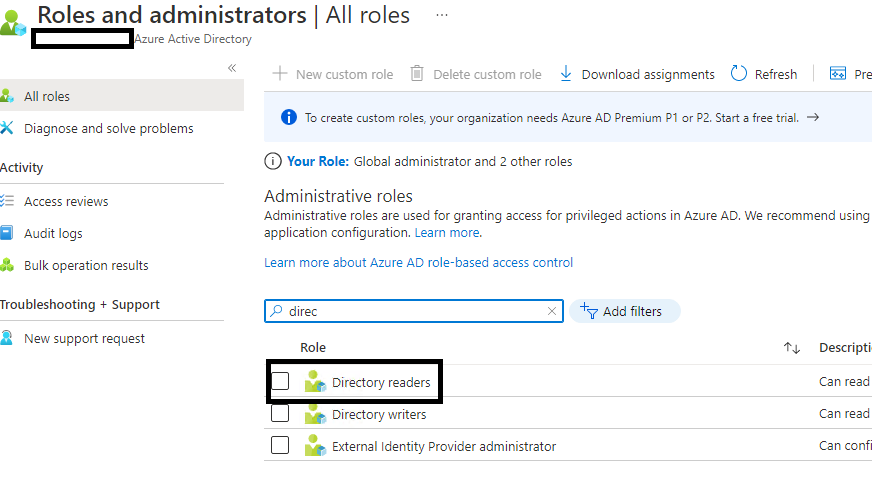
To solve this issue, you need to grant the Service Principal Directory readers Role or higher permissions in Azure Portal -> Azure Active Directory -> Roles and administrators -> Select the target role and add the user.
For example:
Then you can run the azure cli command:az ad app show successfully.
Update:
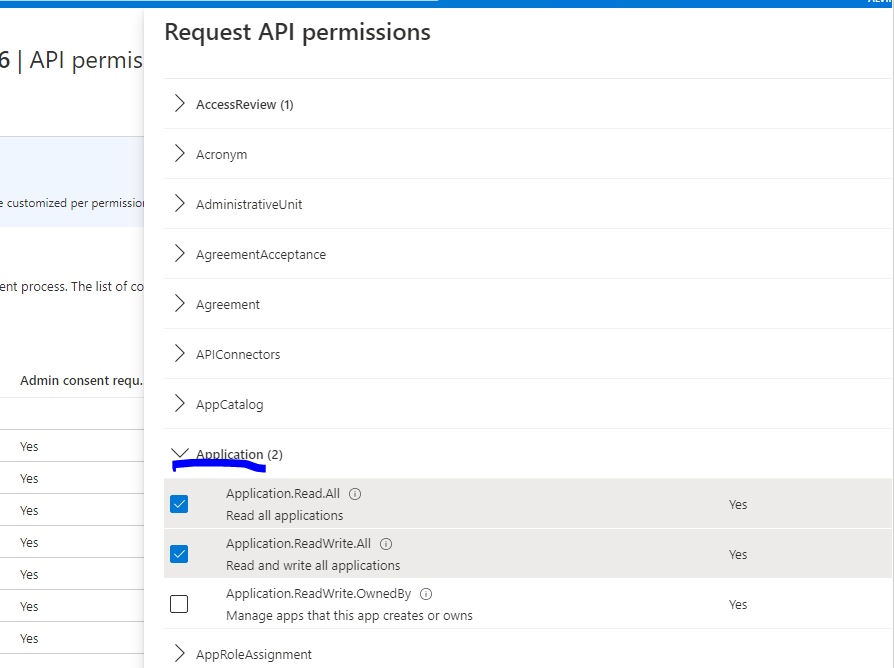
Another method is that you can set the Application.Read.All or Application.ReadWrite.All scope for the Service Principal in AAD -> Target Service Principal -> API Permission -> Search Microsoft Graph -> Application.
Here is an example:
Then you need to click the option:Grant Admin consent for xxx Directory to apply the API permission.