I have two service accounts svc-a and svc-b created in the same domain under same OU. Recently I upgraded my Windwos Web server with latest security patch, where these two service accounts are used to run two different IIS websites.
Post patching, svc-a fails to fetch AD group members for any group. While svc-b can still do that.
The error I get with svc-a is,
get-adgroupmember : Either the target name is incorrect or the server has rejected the client credentials. At line:1 char:1
- get-adgroupmember acifeesadmin -server au.amp.local
CategoryInfo : SecurityError: (acifeesadmin:ADGroup) [Get-ADGroupMember], AuthenticationException FullyQualifiedErrorId : ActiveDirectoryCmdlet:System.Security.Authentication.AuthenticationException,Microsoft.ActiveDirectory.Management.Commands.GetADGroupMember
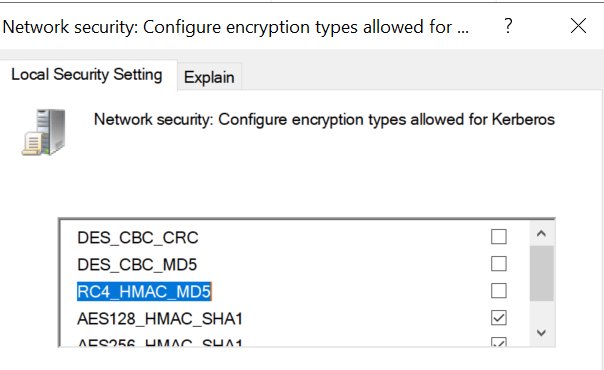
One of the suggested fix I found on Google was to enable RC4_HMAC_MD5 encryption method, which when done, svc-a account can fetch AD group members successfully.
Enabling RC4_HMAC_MD5 encryption type is not a feasible solution for us as our Group policy wipes out this change and also it being an older encryption type, is more vulnerable to attacks.
Based on the suggestion from this excellent blog on Kerberos encryption types
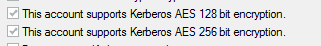
The service account svc-a still cannot fetch AD group members and fails with the same error.
The only way it can fetch AD group members, is when I enable RC4_HMAC encryption type on the Web server(which I don't want to)
In summary,
- Two similar service accounts in a domain used in a window web server to run IIS websites
- Post security patch installation on the Web server, one of the service account fails to fetch AD group members.
- Enabling RC4_HMAC encryption type on the Web server fixes the problem but this is not a feasible solution as our group policy wipes out the change.
- Making changes to the service account on AD, to allow AES 128 and AES 256 encryption types does not help
- I have tried resetting password for svc-a, that too did not help.
Does anyone know what else should I be trying or has insights on why this doesn't work?
CodePudding user response:
This has been fixed. The service account's password was reset before the RODC was created and hence DC kept issuing service tickets with older encryption method. Resetting the password twice after a gap of 10 hours fixed the issue.