I'm hitting an API that requires my public key, then that API will return a response that contains a vector and a token but they are in an encrypted form (I think they used my public key to do that). In order to decrypt it, I need to use my private key. Both private and public keys are in DER encoding.
I basically want to implement something like this 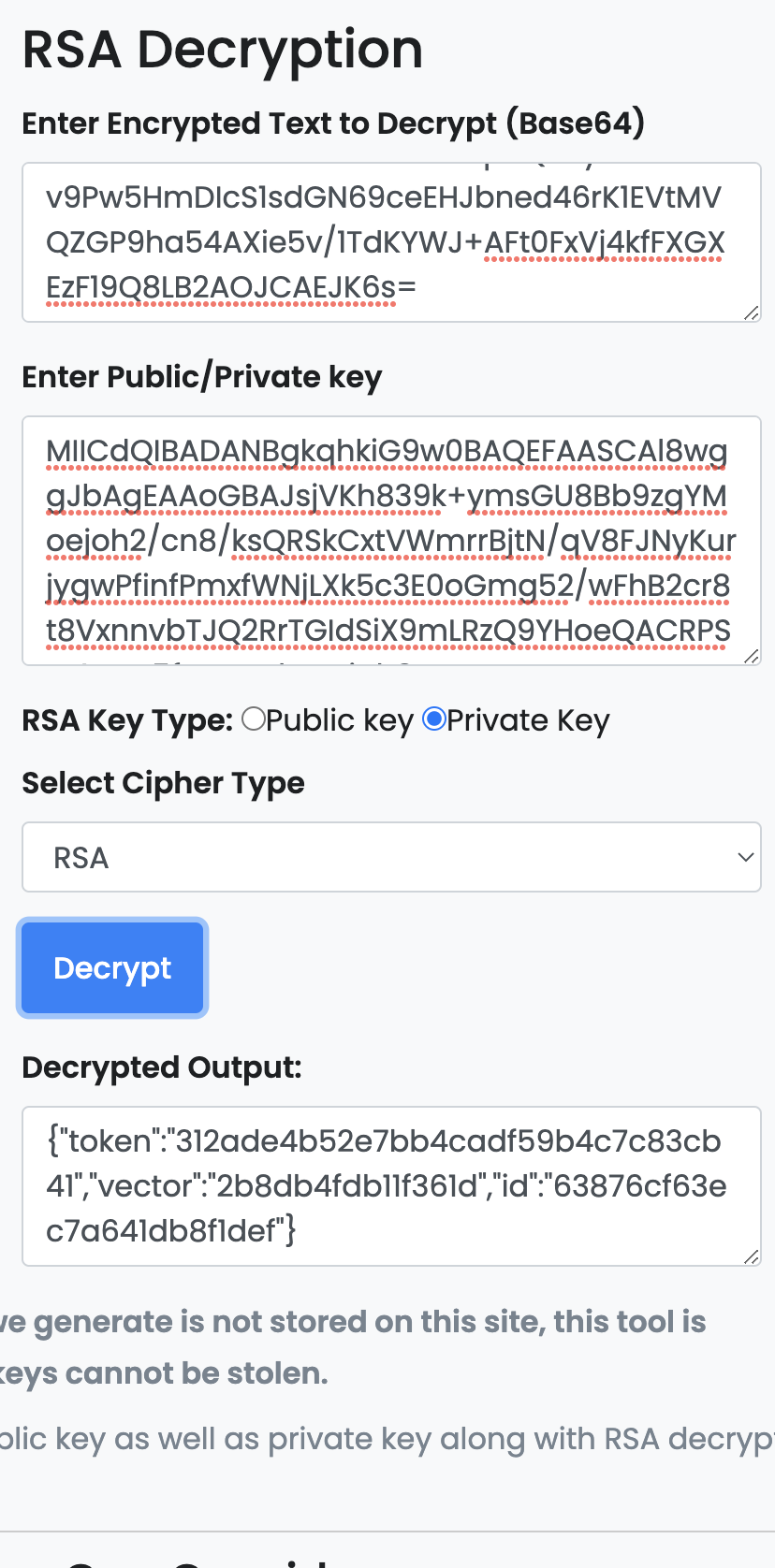
Keys that Im using (again they are dummy!)
Public: MIGfMA0GCSqGSIb3DQEBAQUAA4GNADCBiQKBgQCbI1SofN/ZPsprBlPAW/c4GDKHo6Idv3J/P5LEEUpAsbVVpq6wY7Tf6lfBSTcirq48oMD34p3z5sX1jYy15OXNxNKBpoOdv8BYQdnK/LfFcZ5720yUNka0xiHUol/Zi0c0PWB6HkAAkT0sbeGLbCuX6yr6SbJBFaI2ofIKk/mGswIDAQAB
Private: MIICdQIBADANBgkqhkiG9w0BAQEFAASCAl8wggJbAgEAAoGBAJsjVKh839k ymsGU8Bb9zgYMoejoh2/cn8/ksQRSkCxtVWmrrBjtN/qV8FJNyKurjygwPfinfPmxfWNjLXk5c3E0oGmg52/wFhB2cr8t8VxnnvbTJQ2RrTGIdSiX9mLRzQ9YHoeQACRPSxt4YtsK5frKvpJskEVojah8gqT YazAgMBAAECgYA5KaeD/Z8tmSlUjhxGAJzzGldkCzMs6uHxaSdW/1fwxooeaTBs5hA7gUmcerHKIbsps8HmlKXGvP2sIN/8Fb9mo1yHaAN2g52 cvpr2QmeeUOwfuZTM/gllT4rUIB7sMC5Uxl7sW55bGhRxqdfHJskow4rPga irjuYSy5GIZSwQJBANDtfF VWPKrR8MHYvaGoLLkrA1cFn8g9x1eGA3mgWPNYoH5nMJfe0IBaXo69jlrnBAjK oxnPSyh/AZzsEehasCQQC F15dVSjH8tJSXz8RCDpMdp P9J/eoi7 V0IgwKAaSJCZfYWXeckAAIpvwit7fkj3n83nj0PPm9Xwh22CYGsZAkAAvIWOtLEOken71v/TTKAuYT32AhgWNKCKWvWMvv4/ws6RFLcnvDxr/CNKCgEqLKXtLKKP/cLG3gY6o2ymI5xnAkA8l4JSycRYB8SW0RlvOmoq2Vz/LACRnKzSEcpYWk4uUpcU9ffRUtaJE6MNAJ2Pna9wjxW5C eXk5rcMq7rcgRxAkAjizE3JbwUu3MX5TDmHfGCvIZ38jnfSUjFrYBLKaNJegOD4zcxRZXfO7iKDa PtFMRe7ZtnU7WuCM0yUT2Qa0j
Encrypted message: BUy5nR/PuJNCFXeUxQd4oxkCvMo2JiLwH5VkzLz1UdM4M0VXDv4Ba1OaNHbttqETQENy1VfW2V4v9Pw5HmDIcS1sdGN69ceEHJbned46rK1EVtMVQZGP9ha54AXie5v/1TdKYWJ AFt0FxVj4kfFXGXEzF19Q8LB2AOJCAEJK6s=
Lets go to the coding part:
I'm retrieving my private and public keys from the env file:
public := goDotEnvVariable("publicKey")
private := goDotEnvVariable("privateKey")
Now after hitting the API and getting the result, I tried to decrypt the message by using rsa.DecryptOAEPfunction but it keeps giving me [] crypto/rsa: decryption error. After debugging inside the package itself, Im getting the error right here:
k := priv.Size() // private key size
if len(ciphertext) > k || //ciphertext is the encrypted text and hash.Size()*2 2 is the hash size that Im using
k < hash.Size()*2 2 {
return nil, ErrDecryption
}
Results of the if statement: k = 128 hash.Size()*2 2=66 cipher = 172 At first I had a problem of converting the private key (string in my case, because its from the env file) to rsa private key. Heres what I did to solve the issue:
sEnc, err := b64.StdEncoding.DecodeString(private) //using this package "encoding/base64"
Then I converted it like this:
block := &pem.Block{
Type: "RSA PRIVATE KEY",
Bytes: sEnc,
}
parseResult, err := x509.ParsePKCS8PrivateKey(block.Bytes)
What am I doing wrong?
CodePudding user response:
If RSA is selected in the Select Cipher Type field, the devglan website applies PKCS#1 v1.5 as padding, so rsa.DecryptPKCS1v15() must be used. The private key is a Base64 encoded PKCS#8 DER key which can be imported with x509.ParsePKCS8PrivateKey().
All together:
import (
"crypto/rand"
"crypto/rsa"
"crypto/x509"
b64 "encoding/base64"
"fmt"
)
func main() {
// Base64 decode ciphertext
ciphertext, _ := b64.StdEncoding.DecodeString("BUy5nR/PuJNCFXeUxQd4oxkCvMo2JiLwH5VkzLz1UdM4M0VXDv4Ba1OaNHbttqETQENy1VfW2V4v9Pw5HmDIcS1sdGN69ceEHJbned46rK1EVtMVQZGP9ha54AXie5v/1TdKYWJ AFt0FxVj4kfFXGXEzF19Q8LB2AOJCAEJK6s=")
// Import PKCS#8 key
pkcs8DerKey, _ := b64.StdEncoding.DecodeString("MIICdQIBADANBgkqhkiG9w0BAQEFAASCAl8wggJbAgEAAoGBAJsjVKh839k ymsGU8Bb9zgYMoejoh2/cn8/ksQRSkCxtVWmrrBjtN/qV8FJNyKurjygwPfinfPmxfWNjLXk5c3E0oGmg52/wFhB2cr8t8VxnnvbTJQ2RrTGIdSiX9mLRzQ9YHoeQACRPSxt4YtsK5frKvpJskEVojah8gqT YazAgMBAAECgYA5KaeD/Z8tmSlUjhxGAJzzGldkCzMs6uHxaSdW/1fwxooeaTBs5hA7gUmcerHKIbsps8HmlKXGvP2sIN/8Fb9mo1yHaAN2g52 cvpr2QmeeUOwfuZTM/gllT4rUIB7sMC5Uxl7sW55bGhRxqdfHJskow4rPga irjuYSy5GIZSwQJBANDtfF VWPKrR8MHYvaGoLLkrA1cFn8g9x1eGA3mgWPNYoH5nMJfe0IBaXo69jlrnBAjK oxnPSyh/AZzsEehasCQQC F15dVSjH8tJSXz8RCDpMdp P9J/eoi7 V0IgwKAaSJCZfYWXeckAAIpvwit7fkj3n83nj0PPm9Xwh22CYGsZAkAAvIWOtLEOken71v/TTKAuYT32AhgWNKCKWvWMvv4/ws6RFLcnvDxr/CNKCgEqLKXtLKKP/cLG3gY6o2ymI5xnAkA8l4JSycRYB8SW0RlvOmoq2Vz/LACRnKzSEcpYWk4uUpcU9ffRUtaJE6MNAJ2Pna9wjxW5C eXk5rcMq7rcgRxAkAjizE3JbwUu3MX5TDmHfGCvIZ38jnfSUjFrYBLKaNJegOD4zcxRZXfO7iKDa PtFMRe7ZtnU7WuCM0yUT2Qa0j")
key, _ := x509.ParsePKCS8PrivateKey(pkcs8DerKey)
var privateKey *rsa.PrivateKey
privateKey, _ = key.(*rsa.PrivateKey)
// Decrypt (using RSA with PKCS#1 v1.5 padding)
rng := rand.Reader
plaintext, _ := rsa.DecryptPKCS1v15(rng, privateKey, ciphertext)
fmt.Println(string(plaintext)) // {"token":"312ade4b52e7bb4cadf59b4c7c83cb41","vector":"2b8db4fdb11f361d","id":"63876cf63ec7a641db8f1def"}
}
