I am creating an API which runs off a Function App on Azure. This API communicates with a storage account (a secondary one, not the one created with the function app.) It is imperative that this storage account be as secured as possible.
I am new to Azure, but my initial thought would be to create a Virtual Network, with one subnet for the API which can take requests from any user on the internet, and a second subnet for the storage account that can only communicate with the API. The api would have a private endpoint to the storage account. I want only the API to be able to access that storage account. Or, use a service endpoint to communicate from the subnetted storage account to the API not in the VNET.
However, the Function App consumption plan does not support Virtual Network capabilities. I looked at the pricing model for B1, and that would cost at least 55 dollars a month. This is an api that most likely won't be called that much, and it's not worth the 55 a month yet. Maybe in the future I will go for it, but not now.
I was thinking just allow the function app through the firewall, but apparently the outbound IPs for the function app change sometimes, thus making it difficult to have a permanent connection between the two.
My function app works locally because I allow my home IP through the storage account firewall, and when i say the storage account is open to all IPs the function app works on the cloud, but once I put the firewall back up it stops working. Authentication is done via managed identities if that helps. The only issue I am having is the connectivity between the services, caused by the firewall.
Is it possible to connect these two services securely and persistently without a virtual network? Thanks in advance.
CodePudding user response:
You don't have many options here if cost is your primary concern.
I have some ideas to work around your situation.
- Use Logic Apps.
Suppose you can port your Function app to a Logic App. In that case, you can use the Grant access from Azure resource instances feature in the storage firewall settings, where you can specify only the Logic App (under the resource Microsoft.Logic\workflow) can access the storage account. More details here. Not sure why Function apps are not part of this setting.
- IP Address Whitelist
You've already noticed that the IP address changes for the function app. This is due to the auto-scale capability. If you really want to whitelist the IP addresses, you could use the data center outbound IP addresses. This can be downloaded every week from here. The IP addresses will be on the list one week before being used. You will probably need to find a way to automate adding the IP addresses to the whitelist.
CodePudding user response:
I do agree with @Charles Han that you can use Logic apps for this as an alternative to azure functions and follow below process to secure your connection:
Firstly, I have created a Storage account and created Containers and inserted blobs into it.
And then in Networking section I have selected Public network access Enabled from selected virtual networks and IP addresses Option and then I have saved it.
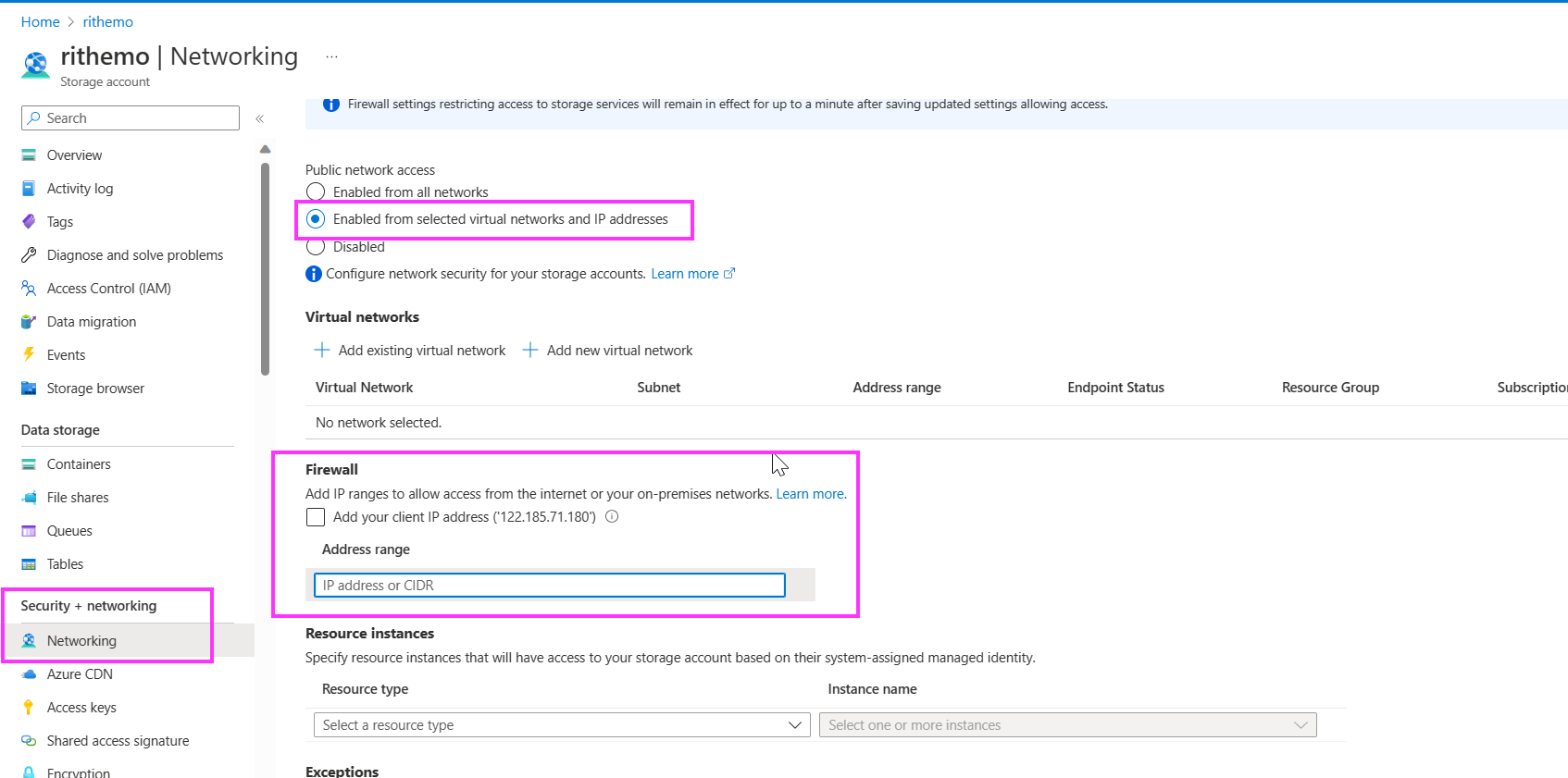
Then I have created a Logic apps as below and Created a Connection between Logic apps and Storage account as below:
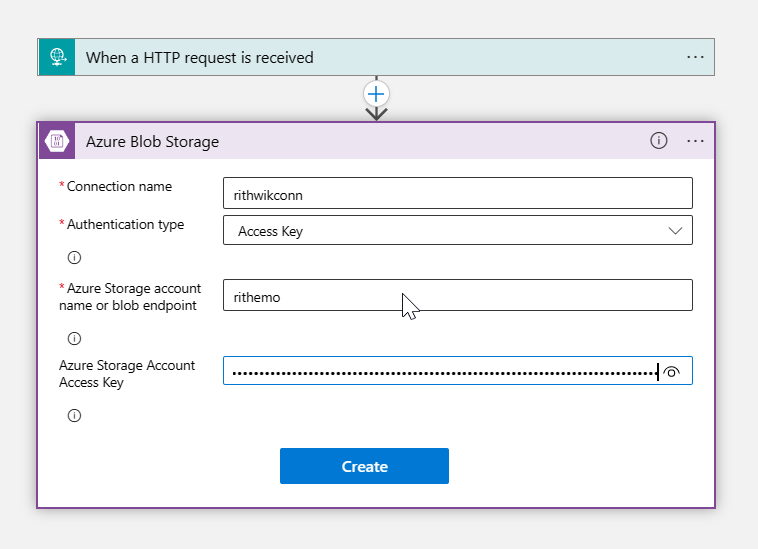
Now to secure Connection, I have copied Connector outgoing IP addresses from Properties section of Logic apps as below:
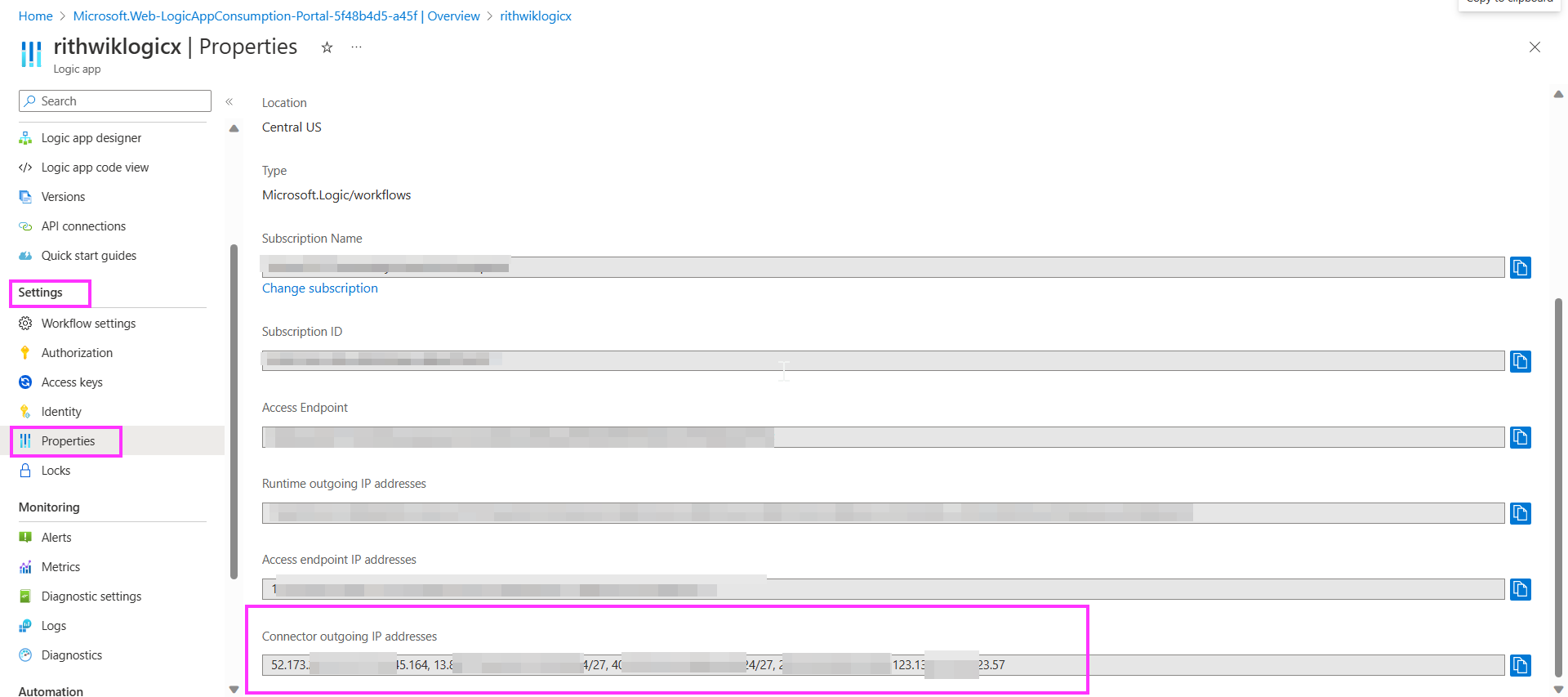
Now I opened again Networking Section of Storage account and added IP address of Connector outgoing IP addresses as below and saved it.
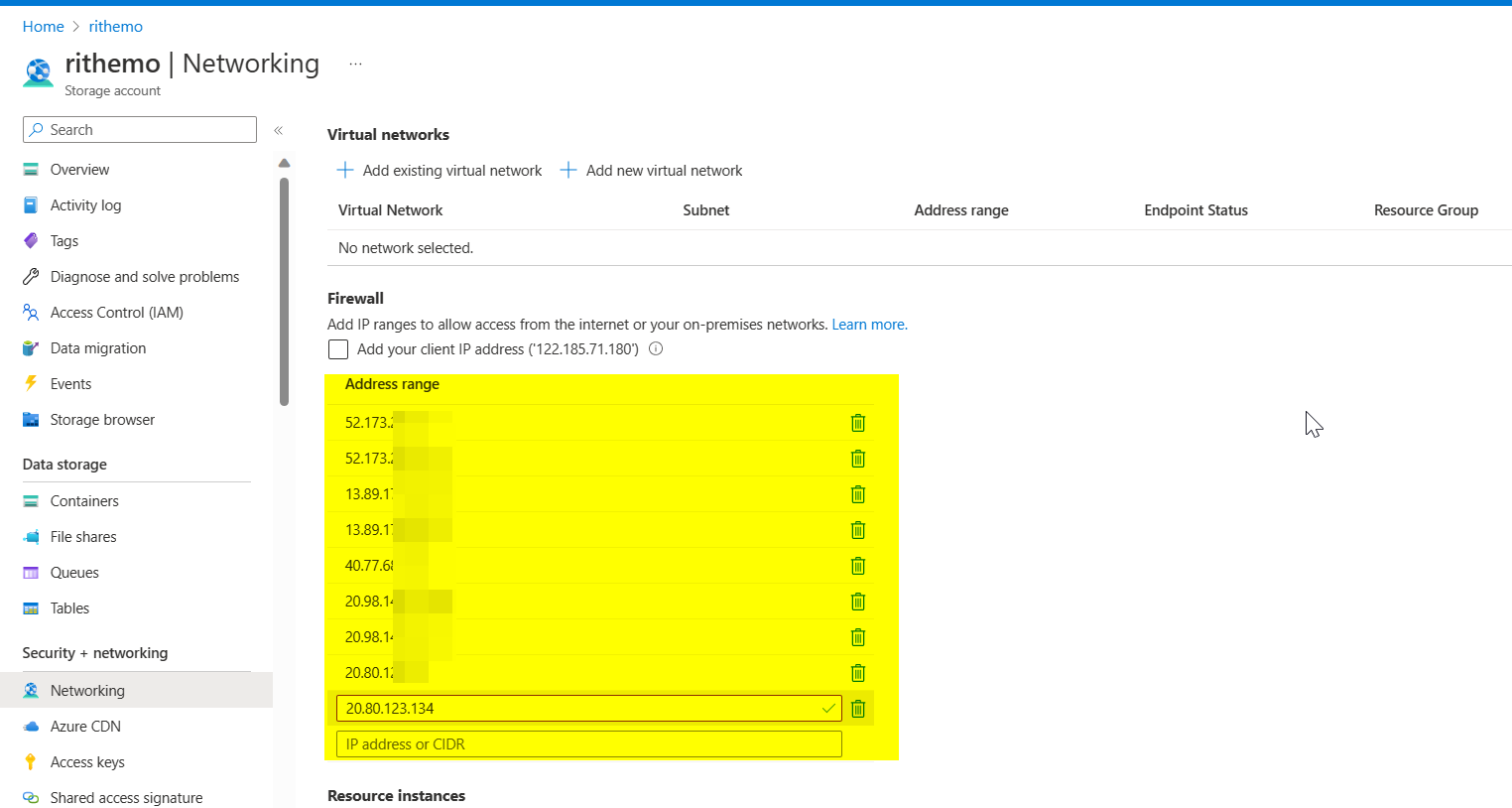
By doing above process your connection is Secured.
Output:
References:
