I am new to azure and I am trying a simple thing but not able to figure out how to set the correct scopes for a service principal. I want to start and stop a ML compute using rest API. In order to do so, I would need the right token.
below are the steps I have taken :
- create a service principal
- created a Oauth query to get the access token
but I get error that
{
"error": {
"code": "InvalidAuthenticationTokenAudience",
"message": "The access token has been obtained for wrong audience or resource 'api://{<!-- -->{id}}'. It should exactly match with one of the allowed audiences 'https://management.core.windows.net/','https://management.core.windows.net','https://management.azure.com/','https://management.azure.com'."
}
}
Now, I am not able to figure out this concept. I have 2 doubts :
- how to set this scope at the service principal end (in the portal), I dont see any such option and also I am not able to find the documentation.
- how this access works? even if I give some resource level owner access to a service principal, then do I still have to provide access at scope option of app registration?
Please help in coming out of this issue.
CodePudding user response:
I figured it out. I selected the option under API permission of a service principal -> https://management.azure.com/user_impersonation
After selecting this, I was able to get the token which was needed to work with management.azure.com but I was not able to figure it out how to find this for a service principal.
I must say that I find azure very confusing. I am not able to find the documents and even if I find it, they seem difficult to me.
Probably, after some months of struggle I will find it easy.
CodePudding user response:
Note that: To start/stop a ML compute instance https://management.azure.com/ scope is required not
api://ClientId.
I tried to reproduce the same in my environment and got the results like below:
I created an Azure AD Application and added API permission:
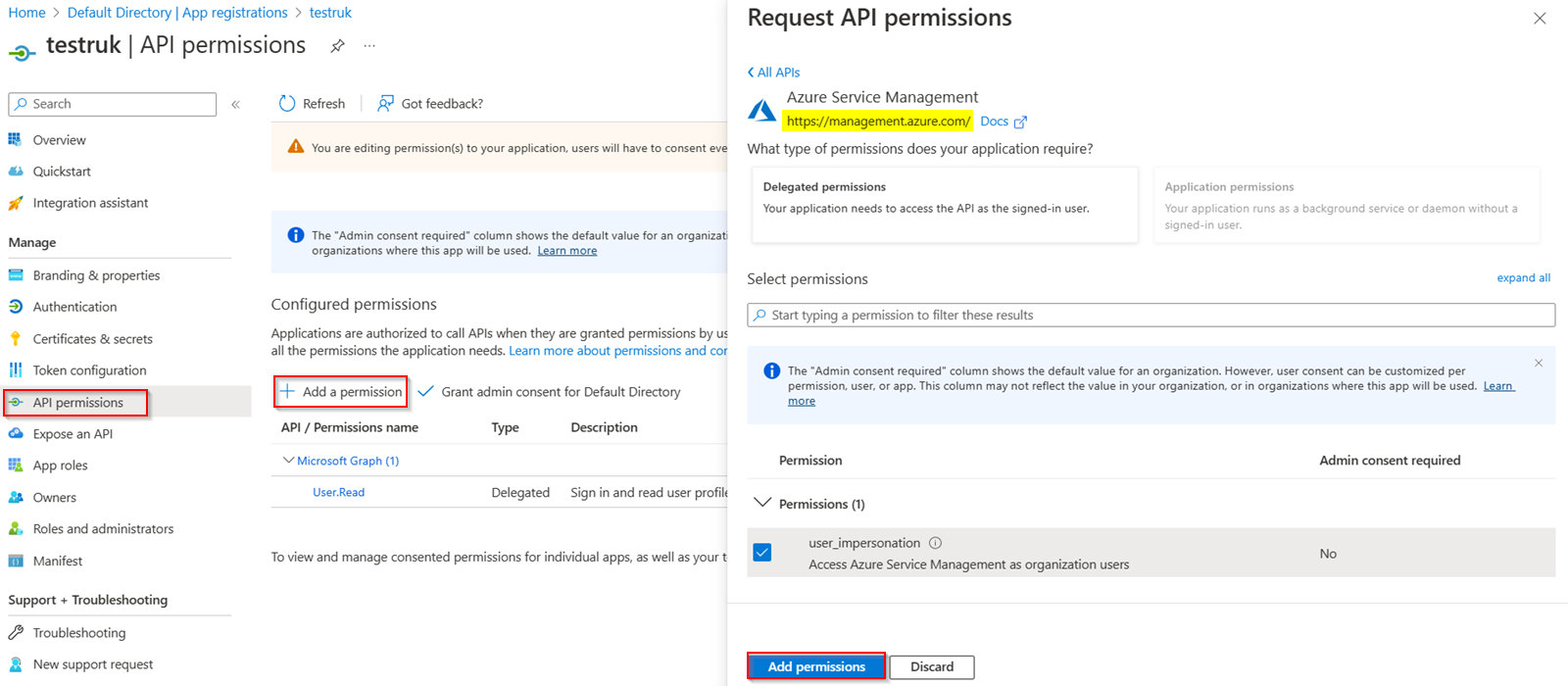
Make sure to grant Admin consent to the Api Permission. As user_impersonation is a delegated permission, you should make use of Authorization Grant Flow or Implicit Flow to generate the token.
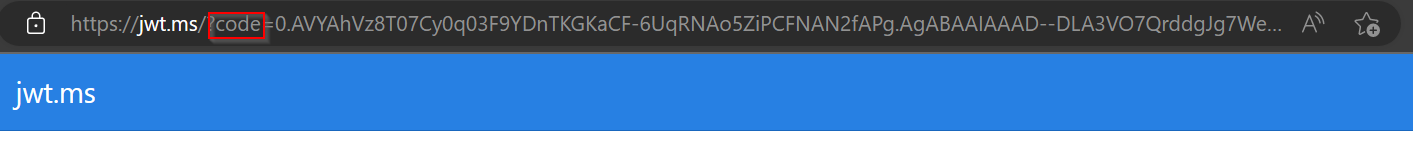
I generated the Authorization code by using below parameters:
https://login.microsoftonline.com/TenantID/oauth2/v2.0/authorize?
&client_id=ClientID
&response_type=code
&redirect_uri=RedirectUri
&response_mode=query
&scope=https://management.azure.com/user_impersonation
&state=12345
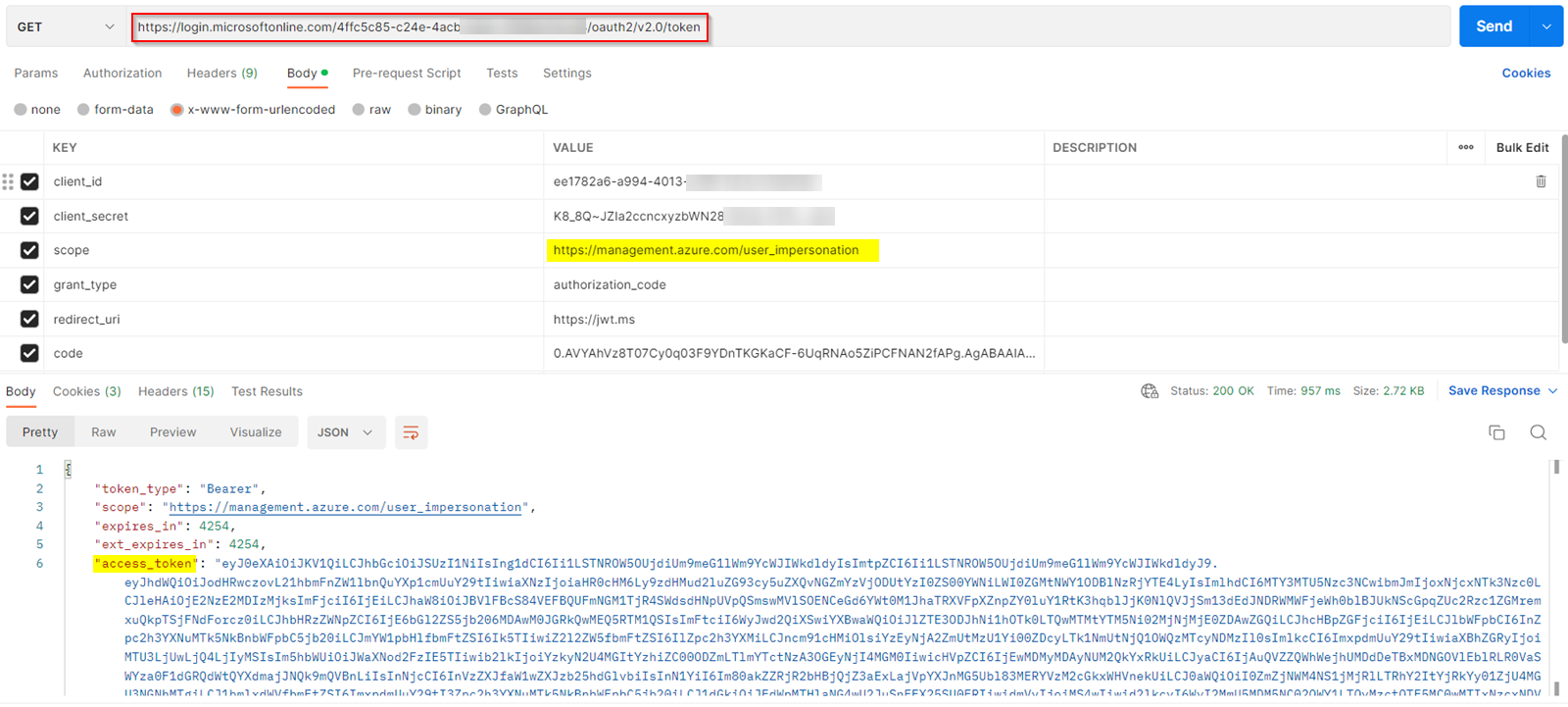
I generated the access token by using below parameters:
https://login.microsoftonline.com/TenantID/oauth2/v2.0/token
client_id:ClientID
client_secret:ClientSecret
scope:https://management.azure.com/user_impersonation
grant_type:authorization_code
redirect_uri:RedirectUri
code:code
Otherwise, you can also make use of Implicit Grant Flow by running the query like below:
https://login.microsoftonline.com/TenantID/oauth2/v2.0/authorize?client_id=ClientID&response_type=token&redirect_uri=RedirectUri&scope=https://management.azure.com/user_impersonation&response_mode=fragment&state=12345&nonce=678910
Access token will be generated redirecting to your redirect Uri like below:
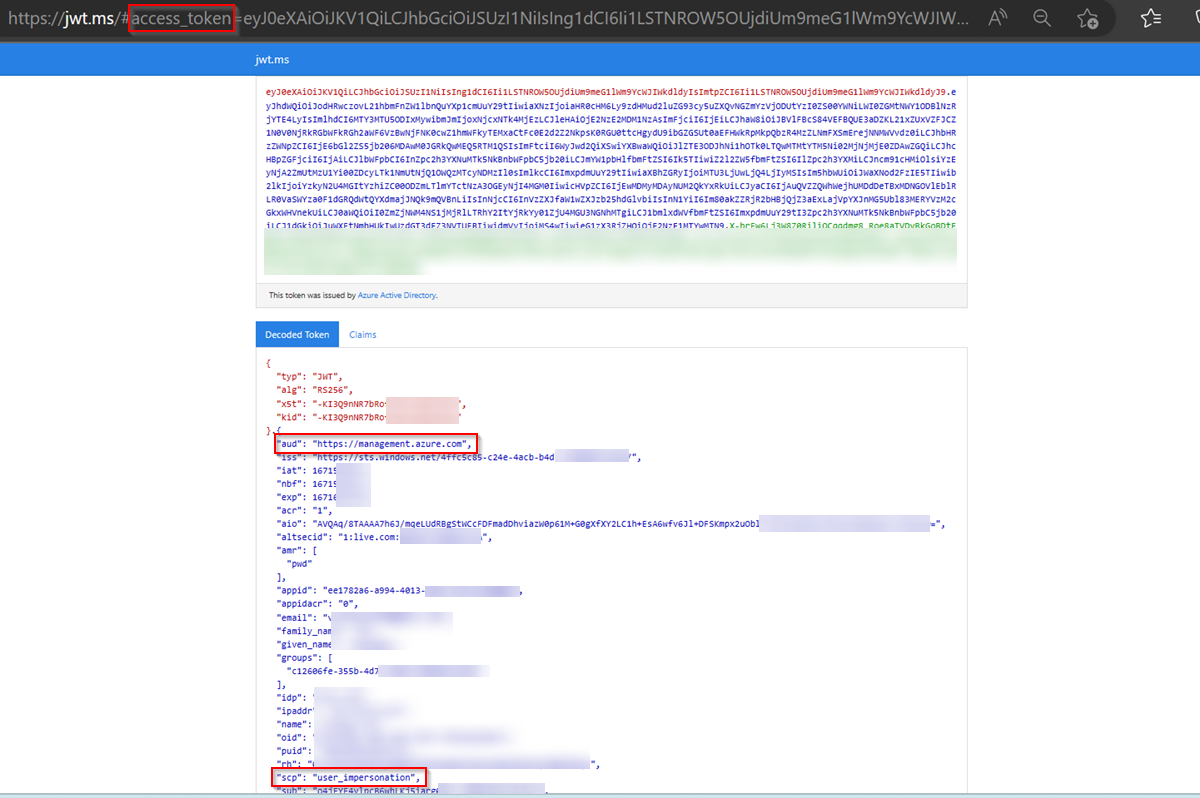
Any of the above ways will generate the access token with the aud https://management.azure.com which will allow to start/stop the ML compute instance.
References:
