I’m trying to create list of Azure AD Groups along with Role using Terraform
I have followed approach in such a way it would first create the required AD groups and then later it will assign the Role
# Required Provider
terraform {
required_providers {
azurerm = {
source = "hashicorp/azurerm"
version = "~> 3.0.2"
}
}
required_version = ">= 1.1.0"
}
# Configure the Microsoft Azure Provider
provider "azurerm" {
features {}
....
....
}
data "azuread_client_config" "current" {}
# Variables
variable "ad_groups" {
description = "Azure AD groups to be added"
type = list(object({
display_name = string,
description = string,
scope = string,
role = string
}))
default = [
{
display_name = "Group1"
description = "some description",
scope = "/providers/Microsoft.Management/managementGroups/xxxxx",
role = "Owner"
},
{
display_name = "Group2"
description = "some description",
scope = "/providers/Microsoft.Management/managementGroups/xxxxx",
role = "Contributor"
}
]
}
# Create AD Groups and add the Current User
resource "azuread_group" "this"{
count = length(var.ad_groups)
display_name = var.ad_groups[count.index].display_name
description = var.ad_groups[count.index].description
security_enabled = true
# prevent_duplicate_names = true
owners = [data.azuread_client_config.current.object_id]
}
# Assign Permission to the AD Group
resource "azurerm_role_assignment" "sp-tenant-global-admin-user-access-role-assignment" {
count = length(var.ad_groups)
scope = var.ad_groups[count.index].scope
role_definition_name = var.ad_groups[count.index].role
principal_id = azuread_group.this[count.index].object_id
depends_on = [
azuread_group.this
]
}
does it look good and would it work? I don't have access to run the above code to validate.
CodePudding user response:
I tried to reproduce the same in my environment.
variable "ad_groups" {
description = "Azure AD groups to be added"
type = list(object({
display_name = string,
description = string,
scope = string,
role = string
}))
default = [
{
display_name = "Group2"
description = "some description",
scope = "/providers/Microsoft.Management/managementGroups/xxxxx",
role = "Reader"
}
]
}
# Create AD Groups and add the Current User
resource "azuread_group" "this"{
count = length(var.ad_groups)
display_name = var.ad_groups[count.index].display_name
description = var.ad_groups[count.index].description
security_enabled = true
owners = [data.azuread_client_config.current.object_id]
}
# Assign Permission to the AD Group
resource "azurerm_role_assignment" "sp-tenant-global-admin-user-access-role-assignment" {
count = length(var.ad_groups)
scope = var.ad_groups[count.index].scope
role_definition_name = var.ad_groups[count.index].role
principal_id = azuread_group.this[count.index].object_id
depends_on = [
azuread_group.this
]
}
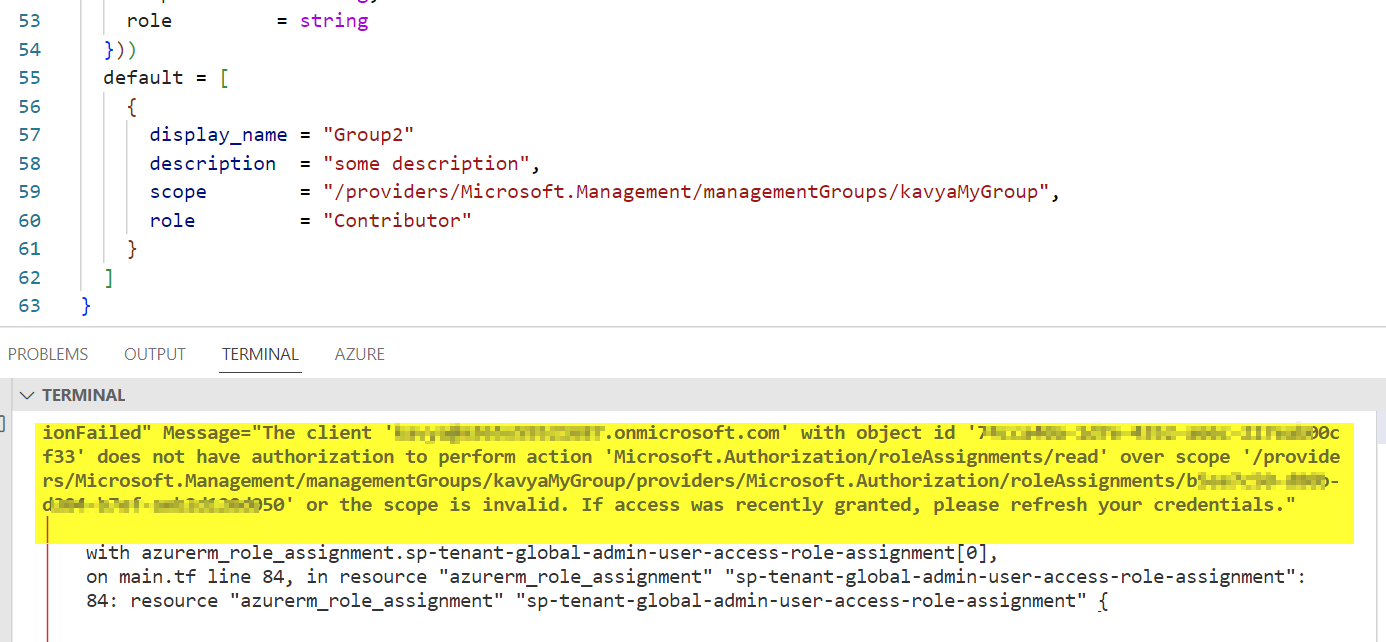
I have received error like:
- As I donot have role over the scope of the subscription, as the
/providers/Microsoft.Management/managementGroups/xxxxneed privilege to assign role over the subscription scope. - But as you are using azurerm provider to create a role to group via terraform , I tried the following code with a resource group scope as I checked it is enough for my groups
Code:
Variables.tf
variable "ad_groups" {
description = "Azure AD groups to be added"
type = list(object({
display_name = string,
description = string,
scope = string,
role = string
}))
default = [
{
display_name = "Group2"
description = "some description",
scope = "/providers/Microsoft.Management/managementGroups/kavyaMyGroup",
scope = "/subscriptions/xxxxx/resourcegroups/myrg"
role = "Reader"
}
]
}
Main.tf:
resource "azuread_user" "example" {
display_name = "kavyaJDoe"
// owners = [data.azuread_client_config.current.object_id]
password = "notSecure123"
user_principal_name = "xxx.onmicrosoft.com"
}
resource "azuread_group" "example" {
display_name = "kavyaMyGroup"
owners = [data.azuread_client_config.current.object_id]
security_enabled = true
members = [
azuread_user.example.object_id,
# more users
]
}
resource "azuread_group" "this"{
count = length(var.ad_groups)
display_name = var.ad_groups[count.index].display_name
description = var.ad_groups[count.index].description
security_enabled = true
# prevent_duplicate_names = true
owners = [data.azuread_client_config.current.object_id]
}
resource "azurerm_role_assignment" "sp-tenant-global-admin-user-access-role-assignment" {
count = length(var.ad_groups)
//scope = var.ad_groups[count.index].scope
scope ="/subscriptions/xxx/resourcegroups/myrg"
role_definition_name = var.ad_groups[count.index].role
principal_id = azuread_group.this[count.index].object_id
depends_on = [
azuread_group.this
]
}
Optional :if role is required to be assigned in order to provide roles to others:
resource "azurerm_role_definition" "role_assignment_write_delete" { name = "RBAC Owner" scope = data.azurerm_client_config.current.subscription_id description = "Management of role assignments" permissions { actions = [ "Microsoft.Authorization/roleAssignments/write", "Microsoft.Authorization/roleAssignments/delete", ] not_actions = [] } assignable_scopes = [ data.azurerm_client_config.current.subscription_id //or management group ] }
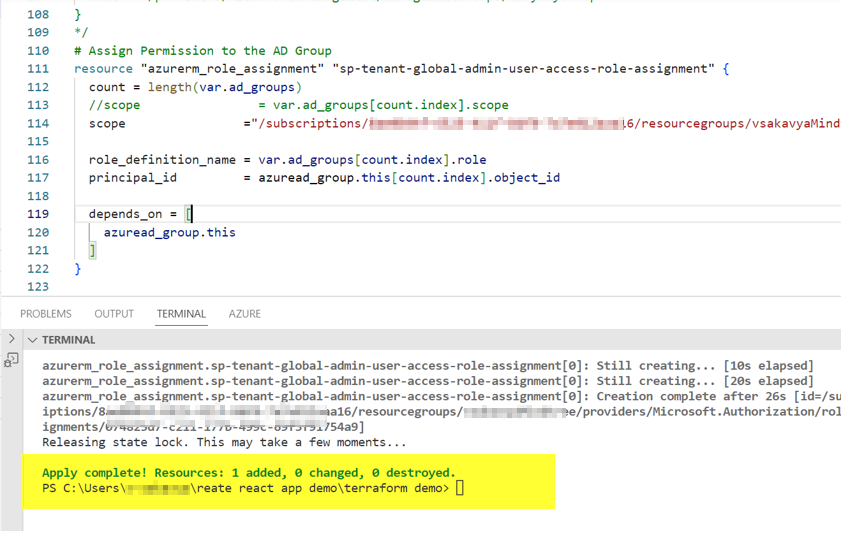
I could create the role assignment successfully:
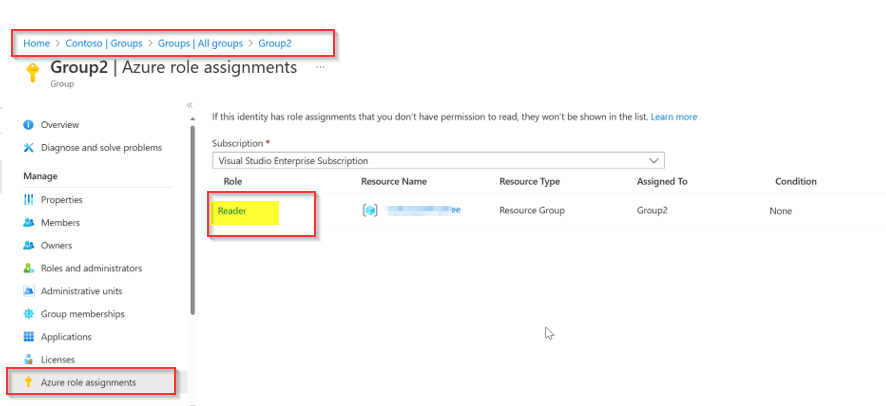
Can see the role created for the group2 that got initiated through variables:
Reference: