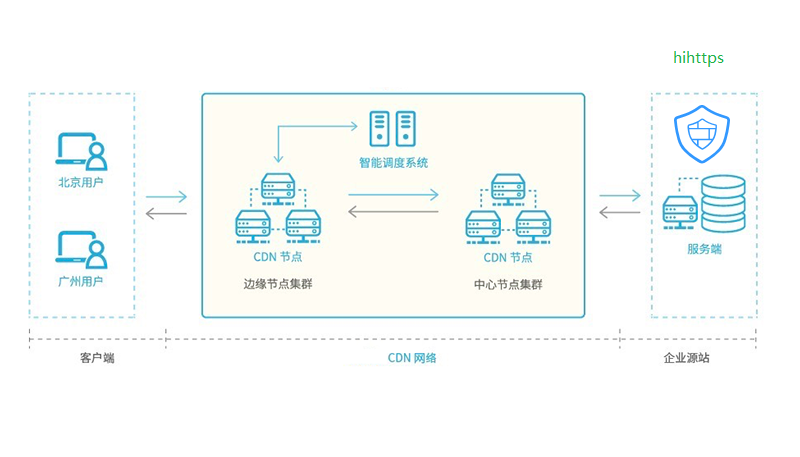
CDN content distribution to the source is the closest to the user's node, and can enhance the response speed of the user to access, solve the source of enterprise website server pressure, CDN industry will still be rapid growth over the next five years, more than 50% of Internet traffic through the CDN to accelerate,
But is still very important network security problem, while ali cloud Web application firewall (WAF) support all kinds of CDN (such as network, accelerate, seven cows, and shoot, ali cloud CDN, etc.), but the price is very expensive, many small and medium-sized enterprises can't afford to have hackers won't get away with the in the mind at the same time, is there a free WAF functionality and performance are good, the answer is yes,
Hihttps is a free web application firewall, supports both traditional WAF detection such as SQL injection, XSS, malicious vulnerability scanning, password cracking, CC, DDOS, etc.), and support the unsupervised machine learning, independent, redefining the web security, the principle of concrete can be baidu search "hihttps generated against rules of machine learning", today the CentOS, for example, step by step, introduce how to use hihttps station to protect the CDN free environment of enterprise source,
a, install
Hihttps source can be in WEB station installed directly on the server, can also be as independent as hardware WAF in front of the deployment server, using the principle of reverse proxy to protect the source station,
First on the http://www.hihttps.com/website to download hihttp. Tar. Gz installation package, tar - ZXVF hihttps. Tar. Gz decompression to any directory, there are three core file and three directory:
1, hihttps is executable, support centos 64 - bit systems,
2, hihttps CFG is a configuration file, such as port/reverse proxy server IP,
3 ml. CFG configuration file, machine learning,
4, the rules directory is against the rules, including OWASP SQL injection, XSS, CC, DDOS, password cracking, malicious scanning, and machine learning autonomy against the rules,
5, "train" directory is unsupervised machine learning samples directory,
6, the log directory is attack alarm log,
Hihttps default configuration front binding port 443 (HTTPS) and port 81 (HTTP), reverse connection port 80:
https://serverip/& lt;==> http://127.0.0.1/
http://serverip:81/& lt;==> http://127.0.0.1/
Annotation: serverip is your server's IP address or domain name, actual, the purpose of this article is no longer under the
If you are within vmware virtual machine to do the test, or not a web server on the server, please install nginx or apache, such as:
Yum yum install nginx or install HTTPD, open a browser, http://serverip/, and confirm the access port 80 was successful,
2, hihttps configuration
1, port configuration
For the convenience of testing, hihttps opened two web ports 81 and 443, note 443 certificate, in need of binding PEM format provides a call server by default. PEM digital certificate, if yes, please change the source station server certificate of the real, the configuration is as follows:
HTTPS. CFG:
Frontend web
Mode HTTP
The bind: 81
Default_backend s_default
Frontend web_ssl
Mode HTTP
Bind: 443 SSL CRT for server pem # pem certificate suggested use absolute paths such as/home/XXX/server. The pem
Default_backend s_default
Errorloc302 400 http://www.hihttps.com/# attack a redirect page, just DROP blocking mode effective
# real backend WEB server port
Backend s_default
Mode HTTP
Server server_default 127.0.0.1:80
2, OWASP rules set up
Hihttps compatible with most ModSecurity rules, the best is the famous security community OWASP, develop and maintain a set of free applications to protect rules, this is the core of the so-called OWASP ModSecurity rule set (CRS), almost covered such as SQL injection, XSS cross-site scripting attack, malicious scanning, password cracking, such as DOS dozens of common WEB attack methods,
Hihttps default configuration of the few, to satisfy common attack protection:
REQUEST - 913 - SCANNER - DETECTION. The conf
REQUEST - 941 - APPLICATION - ATTACK - XSS conf
REQUEST - 942 - APPLICATION - ATTACK - SQLI conf
REQUEST - 20 - APPLICATION - CC - DDOS conf
REQUEST - 20 - APPLICATION - Brute - PASS the conf
White_url. Data
Black_url. Data
.
More rules, can go to https://github.com/SpiderLabs/ModSecurity official website to download, storing files in a directory rule can,
3, configuration of machine learning
Generally speaking, the machine learning is done automatically, without configuration, of course, can be set for the machine precision website file directory, which corresponds to learn such learning is more rapid, accurate:
Ml. CFG:
# www_dir/usr/share/nginx/HTML/
# default is alarm mode ruleAction alert, to be set to block model, please open ruleAction drop
# ruleAction drop
4, machine learning against rules
The Rules directory gan. The rule is automatically generated by the machine learning against Rules file, for the convenience of testing, default an https://serverip/hihttps.html? interface Rules Id=XXX
three, run the test
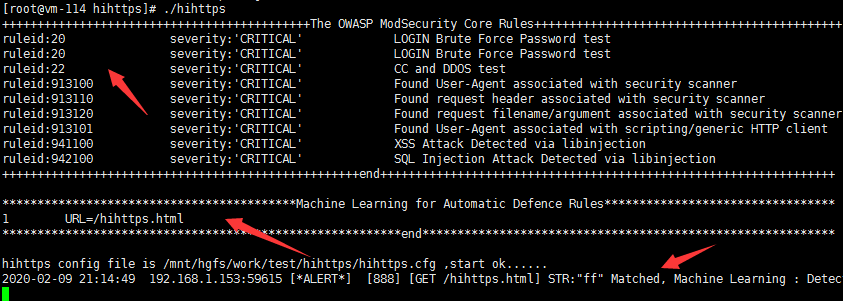
Run./hihttps, if interface to print out the OWASP rules, Mache Learning (machine Learning rules), and shows the start ok... Is normal,
1, the rules of the OWASP test
Can use the Kali Linux, integrates many web vulnerability scanning tools, very convenient testing, such as nkito,
Run the nikto 192.168.0.1 - h - 80, - C p
Or the nikto - host www.baidu.com - 443 - C port SSL
Hihttps main interface will print out, a lot of alarm log,
2, the machine learning test
Machine learning is the core of hihttps, but to collect tens of thousands of samples need some time, in order to facilitate the test, the default an hihttps. HTML machine learning sample,
https://serverip/hihttps.html? Id=123, collected samples of more than 99% are this kind of form, enter the following url, the browser will be regarded as attack:
Attack test sample:
https://serverip/hihttps.html? Id=123 'or 1=1
https://serverip/hihttps.html? Id=& lt; script> Alert (1); </script>
https://serverip/hihttps.html? Id=1234567890 & amp; T=123
https://serverip/hihttps.html? Id=ABC
If the above interface, print out the attack logs, so congratulations you, system running normally, successful hihttps protection,
Alarm log generated in the log directory, according to the days of storage, format is such,,
The 2020-02-09 21:14:49 192.168.1.153:59615 ALERT [* *] [888] [the GET/hihttps. HTML] STR: "ff" Matched, the Machine Learning: Detect an attack, the value is not a number...
... .
4, the official deployment
As a free version, here will be over, the actual deployment, the hihttps and nginx (apache) change the port, hihttps binding 80 and 443, nginx (apache) binding 127.0.0.1:81,
Modify hihttps. CFG file related configuration:
http://serverip/& lt;==> http://127.0.0.1:81/
https://serverip/& lt;==> http://127.0.0.1:81/
Using machine learning a few days later, if artificial verify the alarm accuracy is more than 99.9%, in does not affect the production situation, can modify the ml. The CFG file, open ruleAction drop blocking mode,
Hihttps enterprise pay this is open source, and have a special WEB management interface, and core protection functions are all the same, there is no need to buy expensive WAF, small business
5, summary
1, the traditional waf rules are hard to deal with unknown vulnerabilities and unknown attacks, let the machine learn like a human, have certain intelligent automatic against APT attack may be the only effective way, but the hacker attack and defense technology itself is top human intelligence, WEB security is still a long way to go,
2, fortunately hihttps this kind of free application firewall in machine learning, independent against opened a head is very good, the future of WEB security is likely to be characteristic of engineering + machine learning to complete together, is necessarily AI,
