I'm trying to find a strategy for authorizing a web client that makes HTTP calls to two services hosted in Azure. The web client is all client-side, and the two API Services are Azure Functions hosted in Azure.
For each of the three mentioned apps, I have setup an App Registration in Azure AD and exposed the scopes for the two Azure Functions applications to the web client to allow the client to make calls to them. I have also setup app roles for the two API applications and assigned those roles to a user.
The current setup works very well when the web client makes a single call to each API service. However, I want the web client to make a call to Service A, and then Service A makes an HTTP call to Service B using the credentials of the user of the web client. From what I see, when the web client makes a call to Service A, the token given to the web client only has the Scope and Role for Service A, and nothing for Service B.
My question is, what is the recommended strategy for allowing the user's credentials to be passed along to an internal service? Especially when the original token doesn't have the credentials for the extra service.
I also had to take 2 extra steps for setting up my applications. In the Azure Portal I went to the App Registration for my Service A and:
- Under API Permissions -> Granted it permission to the scope for Service B
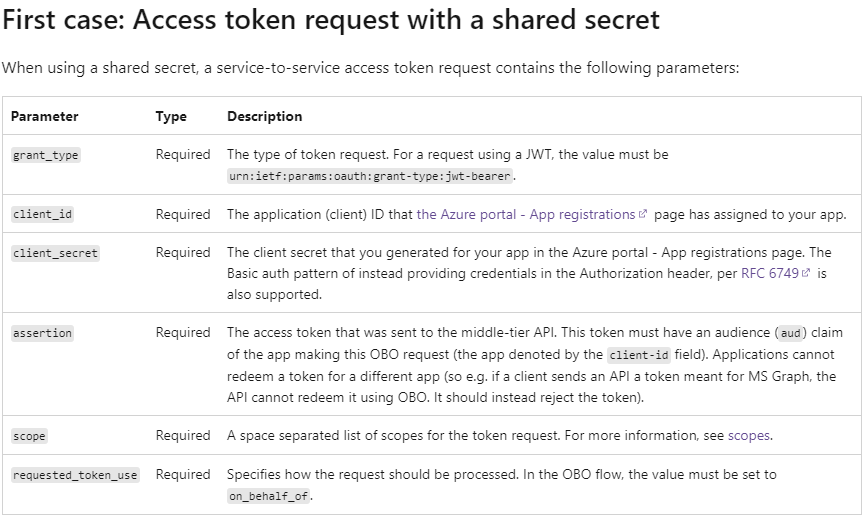
- Under Certificates & Secrets -> Added a new Client Secret. This is the
client_secretfield sent in the HTTP request.
Another answer had an example like this, but it was for ASP.NET applications, not Azure Functions.