I am trying to create a Kubernetes secret for the IAM service account of GCP from the download file which has the following structure
secret.yaml
apiVersion: v1
kind: Secret
metadata:
name: gcp-secret
namespace: tekton-pipelines
type: kubernetes.io/opaque
stringData:
gcs-config: |
{
"type": "service_account",
"project_id": "fetebird-350310",
"private_key_id": "5566b5e81ce3cb9530659be6c70e07a36dcbd581",
"private_key": "-----BEGIN PRIVATE KEY-----\nMIIEvww2VjXHj9/7gQ8ZWs/OaQKBgQDDHqb2rG4b5wGMDeeW\nuNTofm7xfC9yAHBm4Rug6hXpYSy36LUrpe0agZqzcLpH2G4xTarQyx76sPXVCpGc\nyFAQ6Jvj1kqM2pHJlGg L1kX1mZ96jOyyZ2mxPV3r837q90w4CqT2rLKTF9VgWre\nSD6P7h2JbJ46Xzu4Mp72wSxSCg==\n-----END PRIVATE KEY-----\n",
"client_email": "[email protected]",
"client_id": "sssssssss",
"auth_uri": "https://accounts.google.com/o/oauth2/auth",
"token_uri": "https://oauth2.googleapis.com/token",
"auth_provider_x509_cert_url": "https://www.googleapis.com/oauth2/v1/certs",
"client_x509_cert_url": "https://www.googleapis.com/robot/v1/metadata/x509/[email protected]"
}
Run the below command, it does create a secret, However, the authentication is not working via the service account
kubectl apply --filename secret.yaml
service-account.yaml
apiVersion: v1
kind: ServiceAccount
metadata:
name: git-service-account
secrets:
- name: git-ssh-auth
- name: gcp-secret
Pipeline-run
apiVersion: tekton.dev/v1beta1
kind: PipelineRun
metadata:
name: run-pipeline
namespace: tekton-pipelines
spec:
serviceAccountNames:
- taskName: clone-repository
serviceAccountName: git-service-account
- taskName: build
serviceAccountName: gcp-service-account
pipelineRef:
name: fetebird-discount
workspaces:
- name: shared-workspace
persistentVolumeClaim:
claimName: fetebird-discount-pvc
params:
- name: repo-url
value: [email protected]:anandjaisy/discount.git
The way I am creating secret from secret.yaml is correct?
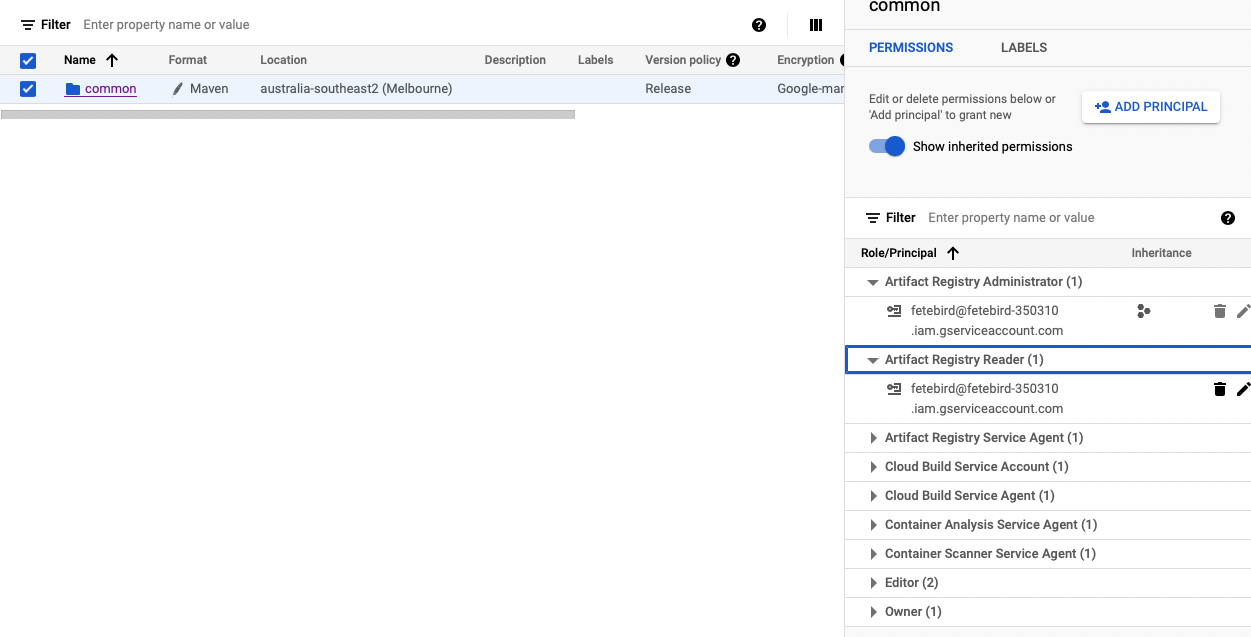
That service account has these permissions
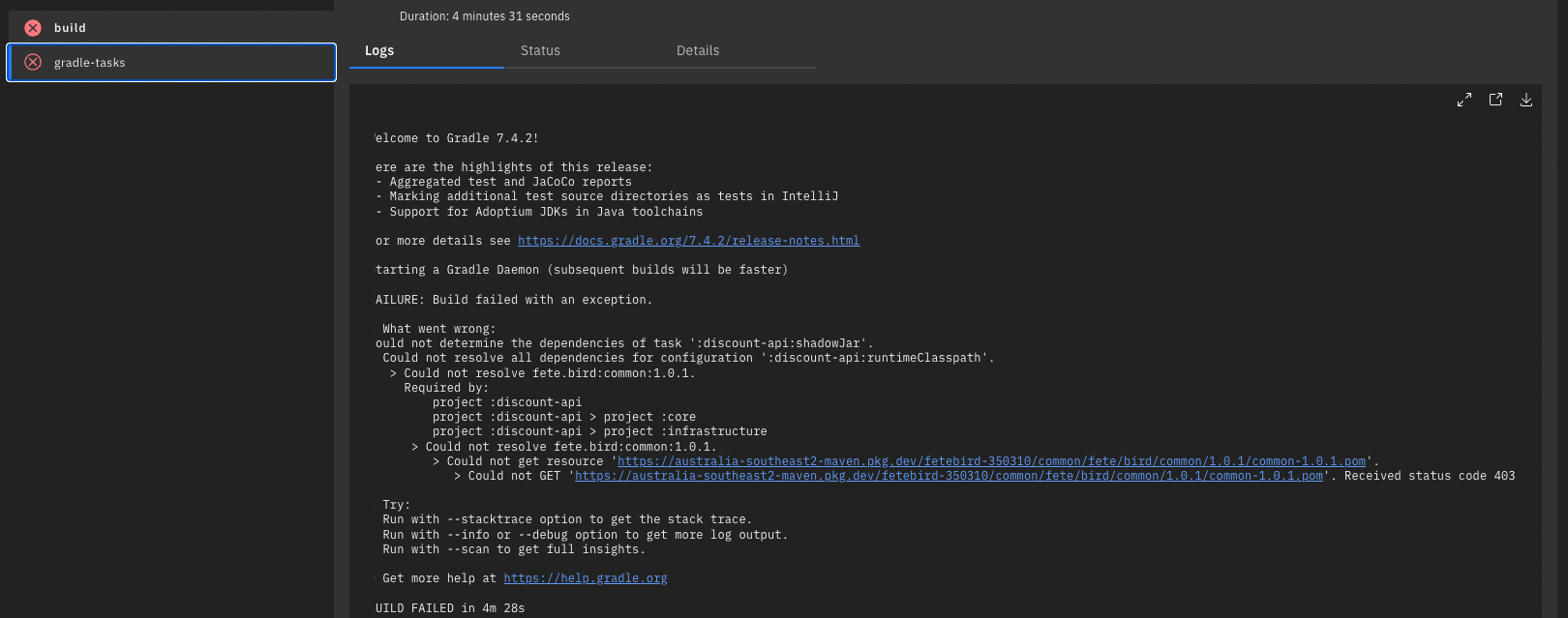
Getting error on tekton pipeline as
If I provide public access to the artifact registry, it works. Somehow the permission are not working for me, not sure how to resolve this
CodePudding user response:
You may try this:
apiVersion: v1
kind: ServiceAccount
metadata:
name: git-service-account
secrets:
- name: git-ssh-auth
- name: pubsub-key
- name: gcp-secret
You did not add the secret to the list of secrets in the serviceaccount.
CodePudding user response:
Can you try the following? And please try to merge all the secrets in the single service account.
apiVersion: tekton.dev/v1beta1
kind: PipelineRun
metadata:
name: run-pipeline
namespace: tekton-pipelines
spec:
serviceAccountName: git-service-account
pipelineRef:
name: fetebird-discount
workspaces:
- name: shared-workspace
persistentVolumeClaim:
claimName: fetebird-discount-pvc
params:
- name: repo-url
value: [email protected]:anandjaisy/discount.git