I have a Blazor application with Client/Server/Shared projects. On creating locally used Azure Active Directory to connect our O365 accounts for logging in/authentication.
Used the default code provided when selecting to use these accounts during the new project setup in Visual Studio, added the relevant App Registrations, redirect URIs, API Access permissions and updated projects with relevant Tenant/Client Ids etc. On debugging locally, all the authentication both on client and server works as expected.
However, when publishing the project to a server for live test, whilst the client side correctly logs and displays the authenticated user, any calls to Server Web API controllers now fail where the [Authorize] is used with the message:
Bearer error="invalid_token", error_description="The audience 'api://xxxetc' is invalid"
I have checked the token both local and live and issuer, audience etc is all the same. The manifest for the server app registration does not state accessTokenAcceptedVersion, and I have tried both adding and removing api:// from appsettings and other places as a test but with no luck.
I am unusure at this point what else I can check or where to go so any help is much appreciated. I have supplied examples of all code/settings used below but removed the actual values.
Client AppSettings:
"AzureAd": {
"Authority": "https://login.microsoftonline.com/xxxxx",
"ClientId": "971f156e-xxxetc",
"ValidateAuthority": true
}
Client Program.cs (Relevant parts only):
builder.Services.AddHttpClient("ProjectName.ServerAPI", client => client.BaseAddress = new Uri(builder.HostEnvironment.BaseAddress))
.AddHttpMessageHandler<BaseAddressAuthorizationMessageHandler>();
builder.Services.AddScoped(sp => sp.GetRequiredService<IHttpClientFactory>().CreateClient("ProjectName.ServerAPI"));
builder.Services.AddMsalAuthentication(options =>
{
builder.Configuration.Bind("AzureAd", options.ProviderOptions.Authentication);
options.ProviderOptions.LoginMode = "Redirect";
options.ProviderOptions.DefaultAccessTokenScopes.Add("api://4f7ef7bbxxxetc/API.Access");
});
Server AppSettings:
"AzureAd": {
"Instance": "https://login.microsoftonline.com/",
"Domain": "companyname.com",
"TenantId": "273a37a4-etc",
"ClientId": "4f7ef7bb-etc",
"Scopes": "API.Access",
"CallbackPath": "/signin-oidc"
}
Server Program.cs (Relevant part only)
builder.Services.AddAuthentication(JwtBearerDefaults.AuthenticationScheme)
.AddMicrosoftIdentityWebApi(builder.Configuration.GetSection("AzureAd"));
The Server app registration client ID/App id is indeed the correct api://4fetc. All other IDs appear to match as required and API Permissions given to both using same scope so should all be correct as per local version working.
CodePudding user response:
To resolve the error, please try including audience parameter in App settings like below:
"audience":"api://{clientId}"
Make sure to grant Api permissions for the scope like below:
Go to Azure Portal -> Azure Active Directory -> App registrations -> Api permissions -> Add permissions -> My APIs
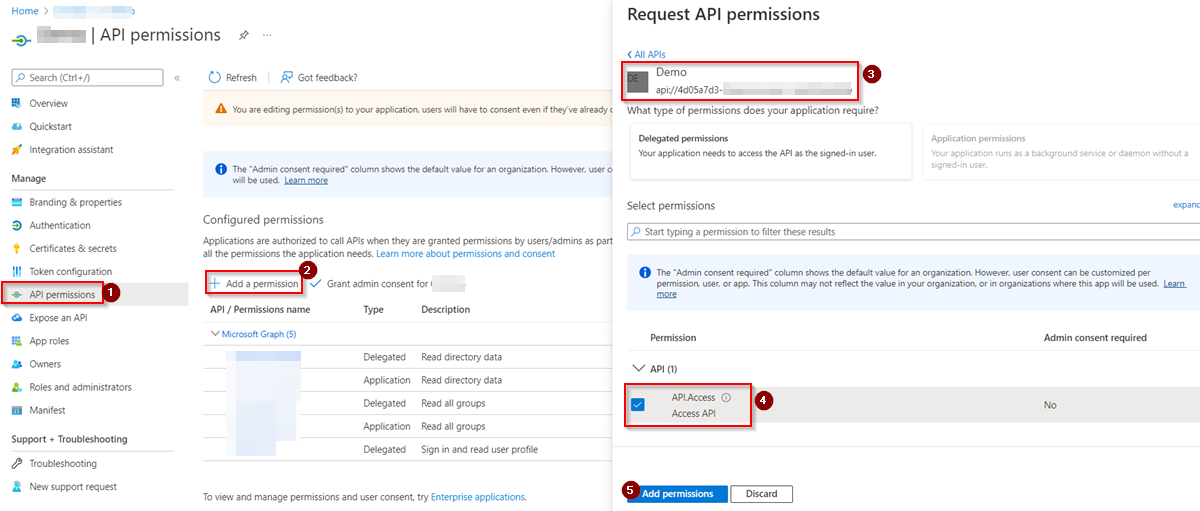
Based on the type of token endpoint you are using, try to add accessTokenAcceptedVersion in the Manifest accordingly as mentioned in this MsDoc.
After generating the token, try decoding it via JSON Web Tokens - jwt.io and verify the aud and scp claims.
References:
