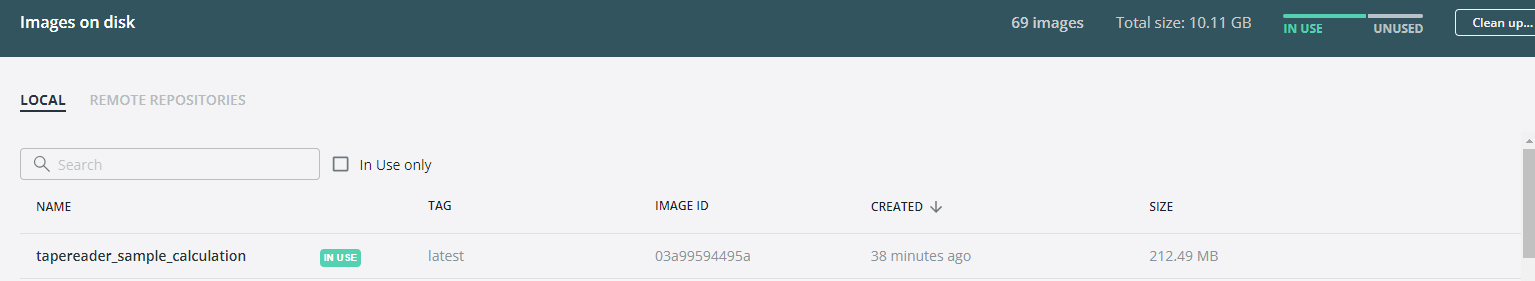
I'm trying to build a Kubernetes job on the fly by using the Kubernetes client in C# (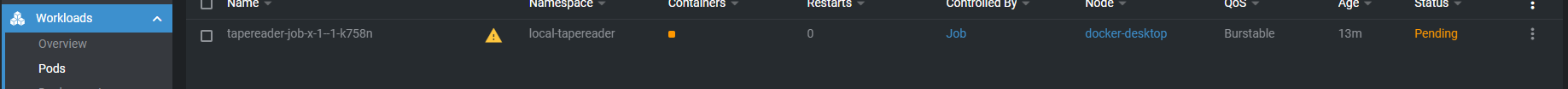
The code for building the job:
var job = new V1Job
{
ApiVersion = "batch/v1",
Kind = "Job",
Metadata = new V1ObjectMeta
{
Name = name,
Labels = new Dictionary<string, string>(),
},
Spec = new V1JobSpec
{
BackoffLimit = backoffLimit,
TtlSecondsAfterFinished = 0,
Template = new V1PodTemplateSpec
{
Spec = new V1PodSpec
{
Tolerations = new List<V1Toleration>(),
Volumes = new List<V1Volume>
{
new V1Volume
{
Name = "podinfo",
DownwardAPI = new V1DownwardAPIVolumeSource
{
Items = new V1DownwardAPIVolumeFile[]
{
new V1DownwardAPIVolumeFile { Path = "namespace", FieldRef = new V1ObjectFieldSelector("metadata.namespace") },
new V1DownwardAPIVolumeFile { Path = "name", FieldRef = new V1ObjectFieldSelector("metadata.name") },
},
},
},
},
Containers = new[]
{
new V1Container
{
Name = "tapereader-job-x-1",
Image = "tapereader_sample_calculation",
Resources = new V1ResourceRequirements
{
Limits = new Dictionary<string, ResourceQuantity>
{
{ "cpu", new ResourceQuantity("4") },
{ "memory", new ResourceQuantity("4G") },
},
Requests = new Dictionary<string, ResourceQuantity>
{
{ "cpu", new ResourceQuantity("0.5") },
{ "memory", new ResourceQuantity("2G") },
},
},
VolumeMounts = new List<V1VolumeMount>
{
new V1VolumeMount { Name = "podinfo", MountPath = "/etc/podinfo", ReadOnlyProperty = true },
},
Env = new List<V1EnvVar>(),
},
},
RestartPolicy = "Never",
},
},
},
};
await Client.CreateNamespacedJobAsync(job, "local-tapereader");
The container is ok, it is present in Docker Desktop (local repo) and I can build & run it without any problems - it also executes the way it should in Docker desktop.
The k8s client creates the pod & job successfully but I get the following error in Lens:
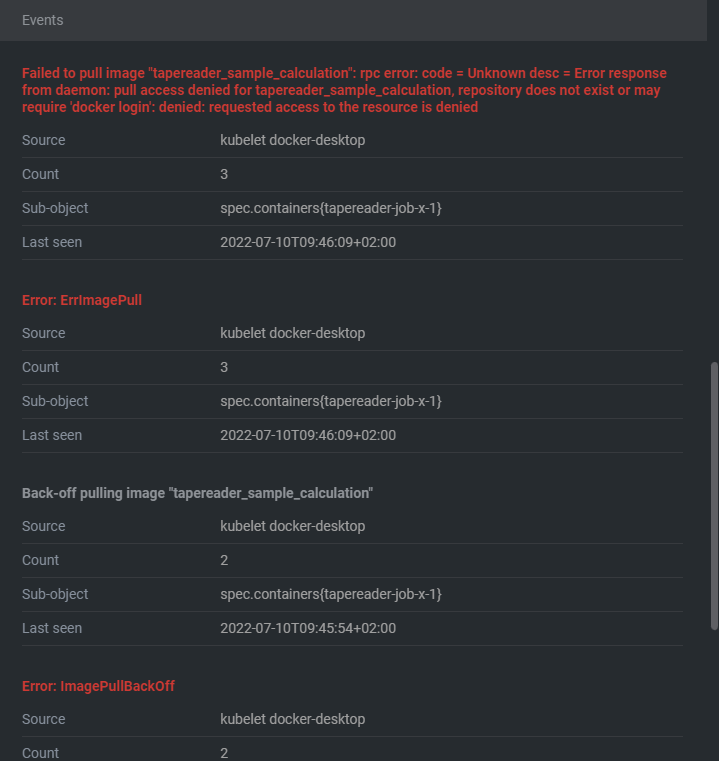
So basically, it states that access was denied? How can I overcome this issue?
I already tried to add creds but this doesn't work
kubectl create secret generic regcred --from-file=.dockerconfigjson=pathto.docker\config.json --type=kubernetes.io/dockerconfigjson
UPDATE:
I actually ran the following, like zero0 suggested:
kubectl create secret generic regcred --from-file=.dockerconfigjson=C:\Users\<USER_NAME>\.docker\config.json --type=kubernetes.io/dockerconfigjson
CodePudding user response:
Are you specifying the correct path for config.json? If you ran the command you've provided, that is not valid. You have to determine the correct path for this.
- On windows this will be
C:\Users\<USER_NAME>\.docker\config.json - On Mac this will be at
/Users/<USER_NAME>/.docker/config.json - On Linux this will be at
/home/<USER_NAME>/.docker/config.json
You will then run:
kubectl create secret generic regcred --from-file=.dockerconfigjson=<PATH_HERE> --type=kubernetes.io/dockerconfigjson
CodePudding user response:
Found the solution. The image resides in the local repo of Docker Desktop. Because of this the image doesn't have to be pulled. To avoid the image pull, the parameter ImagePullPolicy of the Container object should be equal to "Never".
new V1Container
{
ImagePullPolicy = "Never",
Name = name,
Image = image,
...
}