When running my TF script to create an AWS App Runner service I'm getting this error:
InvalidRequestException: Error in assuming instance role arn:aws:iam::000000000000:role/MyAppRunnerServiceRole
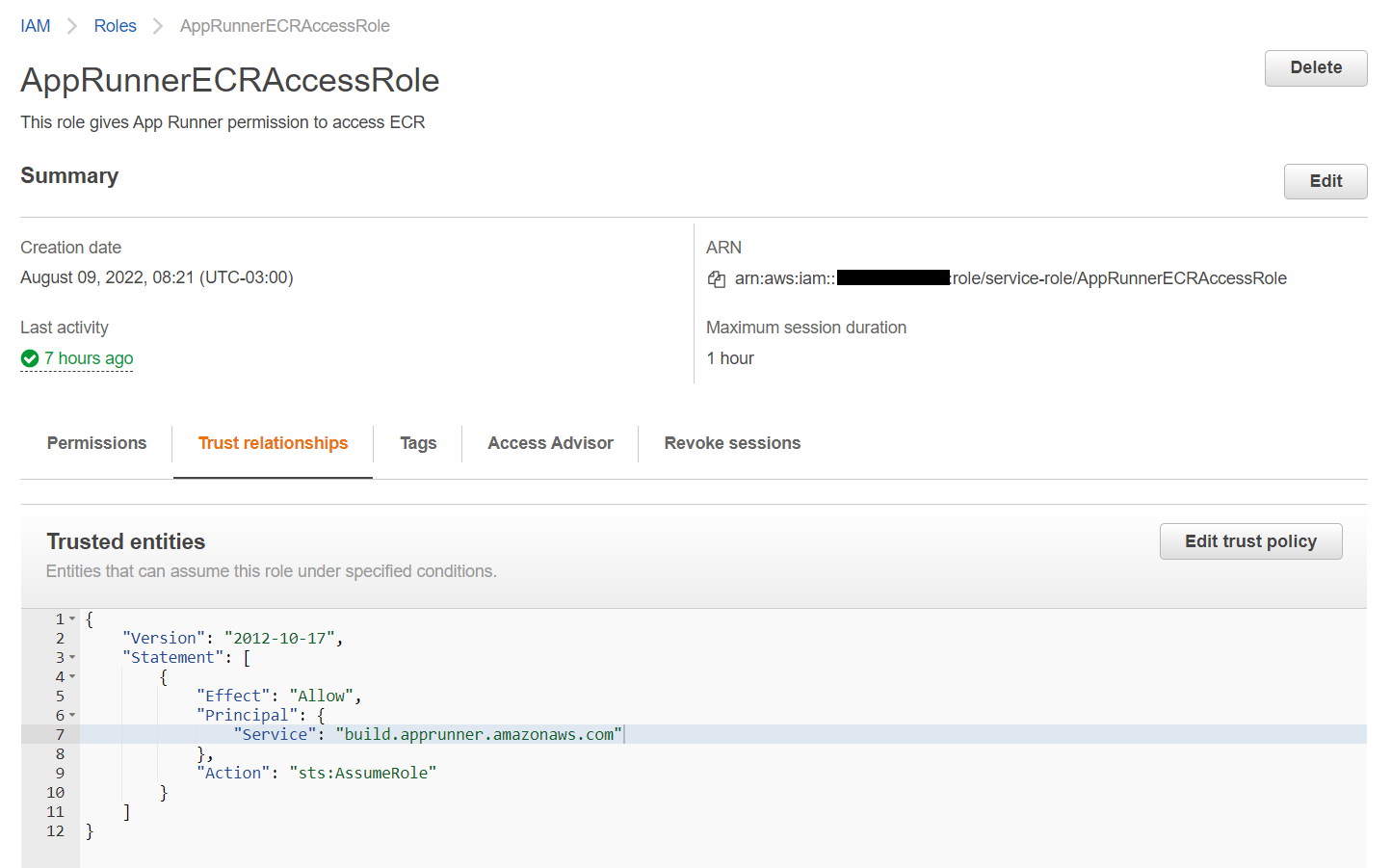
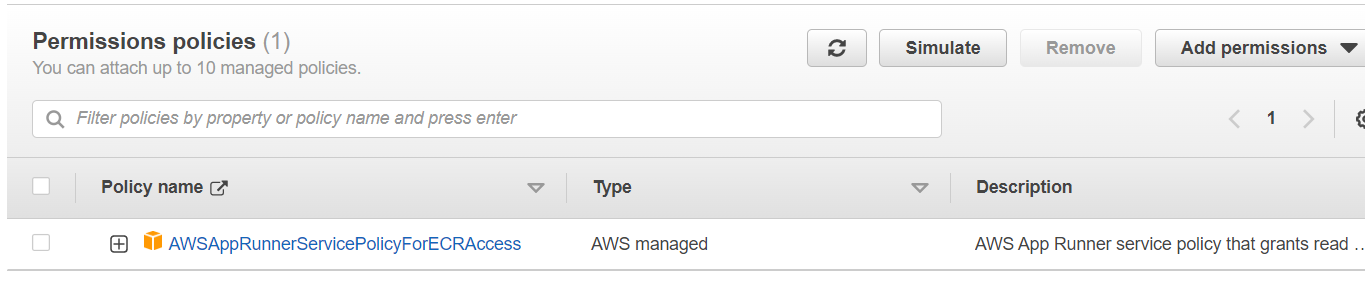
I created the role policy trust using AppRunnerECRAccessRole as reference, which is auto-generated by the console, but using either that or my own below I'm getting the same issue.
Here's my TF code:
### IAM ###
resource "aws_iam_role" "app_runner" {
name = "MyAppRunnerServiceRole"
assume_role_policy = jsonencode({
Version = "2012-10-17"
Statement = [
{
Action = "sts:AssumeRole"
Effect = "Allow"
Sid = ""
Principal = {
Service = "build.apprunner.amazonaws.com"
}
},
]
})
}
resource "aws_iam_role_policy_attachment" "app_runner" {
role = aws_iam_role.app_runner.name
policy_arn = "arn:aws:iam::aws:policy/service-role/AWSAppRunnerServicePolicyForECRAccess"
}
### App Runner ###
resource "aws_apprunner_service" "main" {
service_name = "sandbox-service"
source_configuration {
image_repository {
image_configuration {
port = "5000"
}
image_identifier = "${aws_ecr_repository.main.repository_url}:latest"
image_repository_type = "ECR"
}
}
instance_configuration {
instance_role_arn = aws_iam_role.app_runner.arn
}
}
This is the AppRunnerECRAccessRole which is auto-generated by the Console when creating a new App Runner service. I would assume this same configuration would work, but it isn't.
CodePudding user response:
It seems that the access and instance roles were mixed up in your code. Based on the AWS documentation [1], you need to change the trust policy to be:
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Principal": {
"Service": "tasks.apprunner.amazonaws.com"
},
"Action": "sts:AssumeRole"
}
]
}
The permissions policy should probably remain the same, but for the sake of the completeness of the answer, it should be something along the lines:
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": [
"ecr:GetDownloadUrlForLayer",
"ecr:BatchCheckLayerAvailability",
"ecr:BatchGetImage",
"ecr:DescribeImages",
"ecr:GetAuthorizationToken"
],
"Resource": "*"
}
]
}
You can of course limit everything except the ecr:GetAuthorizationToken to your ECR repo. The ecr:GetAuthroziationToken has to be set for "Resource": "*".
Update: Correct placement of the Access role within the source configuration section for the "build.apprunner.amazonaws.com" service
resource "aws_apprunner_service" "example" {
source_configuration {
authentication_configuration {
access_role_arn = aws_iam_role.access_role.arn
}
}
}