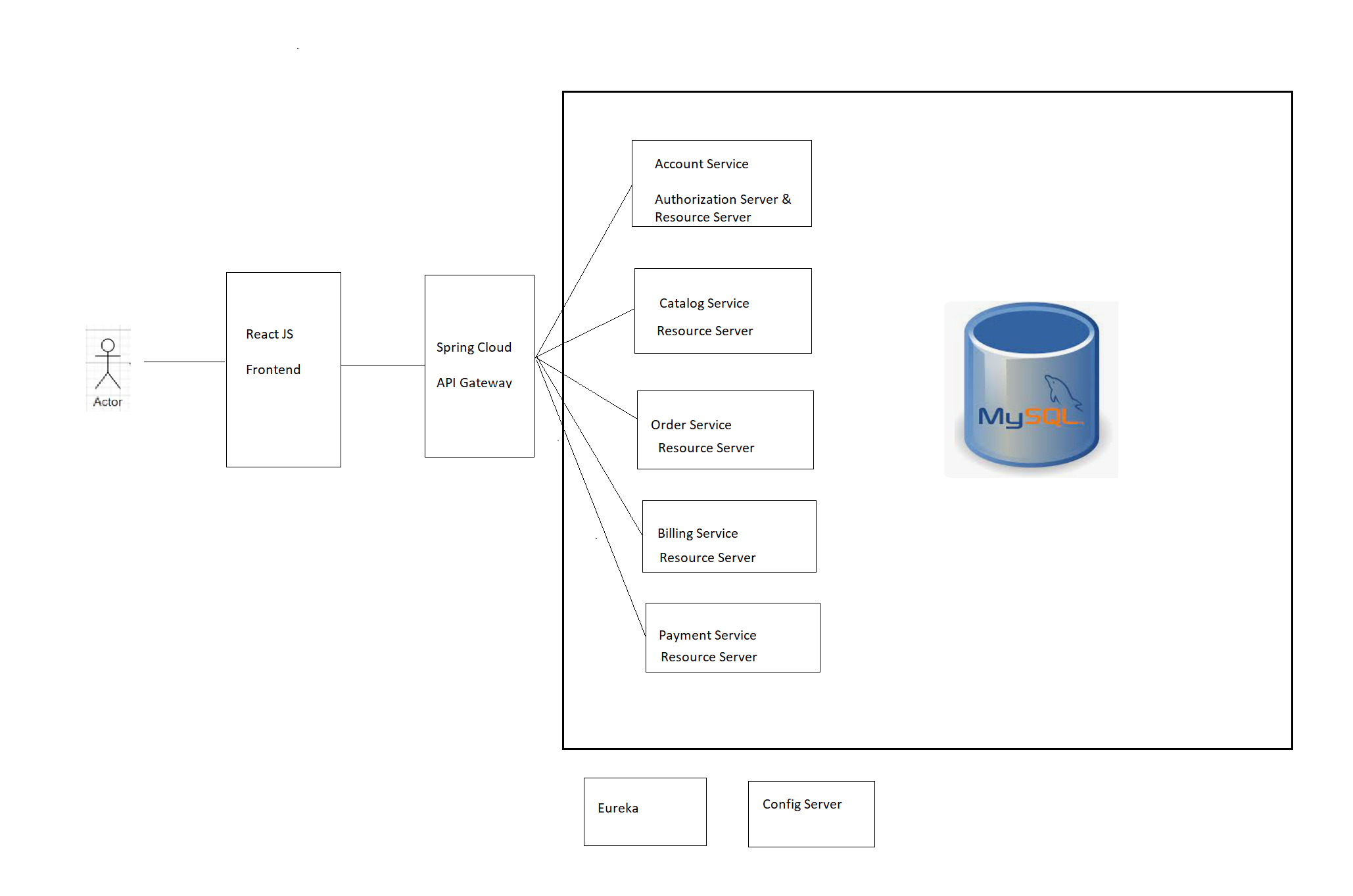
My application is mainly based on spring boot micro services. Currently it uses OAuth with password grant_type which is deprecated in the latest spring security authorization server release. For receiving JWT token, it stores client id and client secret in React JS frontend which is not secure and not recommended. Users need to register to access certain resources and application maintains login credentials in mysql DB
I am trying to upgrade spring security and want 'account service' to act as authorization server to issue JWT tokens.
- Am I correct in my understanding that I need to use authorization_code grand type with PKCE?
- If I use PKCE then I do not need users to provide passwords while registering, is that correct? Storing only username/email should suffice because users just need to pass client ID and code_challenge to get authorization code?
CodePudding user response:
- Am I correct in my understanding that I need to use authorization_code grand type with PKCE?
The newest version of Spring Security mode introduces a new project for the Authorization server in the scope of Spring Security:
<dependency>
<groupId>org.springframework.security</groupId>
<artifactId>spring-security-oauth2-authorization-server</artifactId>
<version>0.3.1</version>
</dependency>
The authorization server from spring implements OAuth2.1 where as you mentioned, both PASSWORD and IMPLICIT grant types were removed comparing it to OAuth 2.0. Gran types supported in OAuth 2.1: 1
- Authorization code PKCE
- client credentials
- device grant type
OAuth 2.1 provide authorization code PKCE grant type but it's a little bit different from the previous.
"The key difference between the PKCE flow and the standard Authorization Code flow is users aren’t required to provide a client_secret. (...) In place of the client_secret, the client app creates a unique string value, code_verifier, which it hashes and encodes as a code_challenge. When the client app initiates the first part of the Authorization Code flow, it sends a hashed code_challenge."
That type of grant type is recommended for SPA application so if you want to use the newest version of spring security you need to use it, because e.g. client credentials are reserved for machine-to-machine communication when one service needs to communicate with another service without of user's knowledge.
- If I use PKCE then I do not need users to provide passwords while registering, is that correct? Users need to authenticate themselves and that's a part of this grant-type flow.
Storing only username/email should suffice because users just need to pass client ID and code_challenge to get an authorization code? ClientID and generated code_challenge (should be generated by the client) is something that identifies the client not the resource owner, so user while authorized shouldn't provide this type of info.
CodePudding user response:
Yes, use authorization code to authenticate users (from public or confidential clients, it doesn't matter).
Any OAuth2 authorization-server will support it. You can use Spring authorization-server framework to build your own, but could also prefer to pick one "off the shelf": there are plenty out there with a lot of features implemented
- connect to LDAP and "social" identity providers (Google, Facebook, Github, etc.)
- enhance security with multi-factor authentication
- provide with admin UI for stuff like user roles or tokens content
- ...
And this either on premise (Keycloak is a quite popular sample) or SaaS (like Auth0 and many others: almost any cloud provider has its own solution).
Also, use an OAuth2 client library in your React app. It will help you to:
- redirect users to authorization-server
- handle redirection back from authorisation-server with authorization code
- exchange authorization code for tokens (access, refresh and ID)
Some libs even handle:
- access token silent refresh before it expires
- request Authorization to configured routes (add access token as header)
- automatically trigger login when a user tries to access protected parts of the app.
I have not enough experience with React to recommend a specific lib, but you can search with "OpenID", "OIDC" or even "OAuth2" keywords