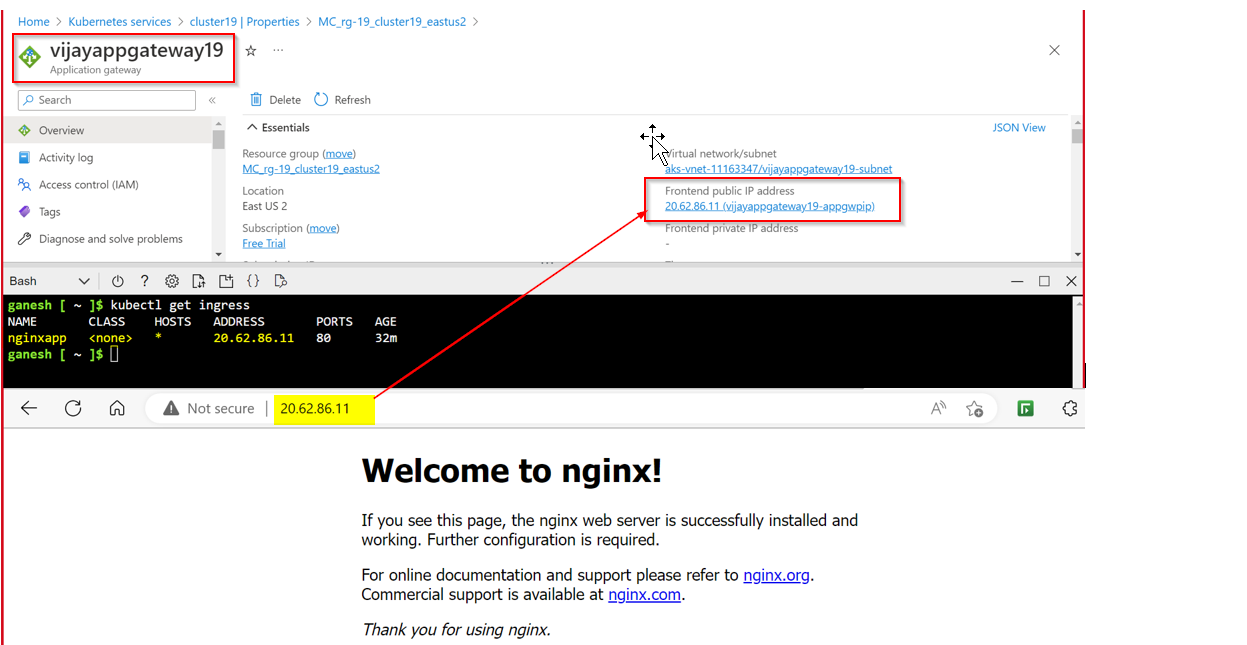
I've created a Kubernetes cluster in Azure using the following Terraform. As you see clearly, I have passed the AppGateway ID to ingress_application_gateway.
# Create the Azure Kubernetes Service (AKS) Cluster
resource "azurerm_kubernetes_cluster" "kubernetes_cluster" {
count = var.enable_kubernetes == true ? 1 : 0
name = "aks-prjx-${var.subscription_type}-${var.environment}-${var.location}-${var.instance_number}"
location = var.location
resource_group_name = module.resource_group_kubernetes_cluster[0].name # "rg-aks-spoke-dev-westus3-001"
dns_prefix = "dns-aks-prjx-${var.subscription_type}-${var.environment}-${var.location}-${var.instance_number}" #"dns-prjxcluster"
private_cluster_enabled = false
local_account_disabled = true
default_node_pool {
name = "npprjx${var.subscription_type}" #"prjxsyspool" # NOTE: "name must start with a lowercase letter, have max length of 12, and only have characters a-z0-9."
vm_size = "Standard_B8ms"
vnet_subnet_id = data.azurerm_subnet.aks-subnet.id
# zones = ["1", "2", "3"]
enable_auto_scaling = true
max_count = 3
min_count = 1
# node_count = 3
os_disk_size_gb = 50
type = "VirtualMachineScaleSets"
enable_node_public_ip = false
enable_host_encryption = false
node_labels = {
"node_pool_type" = "npprjx${var.subscription_type}"
"node_pool_os" = "linux"
"environment" = "${var.environment}"
"app" = "prjx_${var.subscription_type}_app"
}
tags = var.tags
}
ingress_application_gateway {
gateway_id = azurerm_application_gateway.network.id
}
# Enabled the cluster configuration to the Azure kubernets with RBAC
azure_active_directory_role_based_access_control {
managed = true
admin_group_object_ids = var.active_directory_role_based_access_control_admin_group_object_ids
azure_rbac_enabled = true #false
}
network_profile {
network_plugin = "azure"
network_policy = "azure"
outbound_type = "userDefinedRouting"
}
identity {
type = "SystemAssigned"
}
oms_agent {
log_analytics_workspace_id = module.log_analytics_workspace[0].id
}
timeouts {
create = "20m"
delete = "20m"
}
depends_on = [
azurerm_application_gateway.network
]
}
I was thinking that AppGateway will be used as the Ingress Gateway. However, AKS creates the Azure Load Balancer while trying to deploy the Service like mentioned below
apiVersion: v1
kind: Service
metadata:
name: aks-helloworld
spec:
type: LoadBalancer
ports:
- port: 80
selector:
app: aks-helloworld-two
Is there a reason for this Load Balancer and AppGateway not being used? I would assume that Load balancer is used for type LoadBalancer and App Gateway is used for Ingress
CodePudding user response:
I tried to reproduce the same in my environment to create a Service with Application Gateway Ingress Controller:
Since you mentioned service type: Load balancer in your yaml file, it is creating load balancing service, Inorder to create service with Application Gateway Ingress Controller without an associated Load Balancer, kindly follow the below steps.
1.First, you need to create a deployment for your application with the desired replicas and the desired image.
apiVersion: apps/v1
kind: Deployment
metadata:
name: test-app
spec:
replicas: 2
selector:
matchLabels:
app: nginx
template:
metadata:
name: test-app
labels:
app: nginx
spec:
containers:
- name: nginx
image: "nginx:latest"
ports:
- containerPort: 80
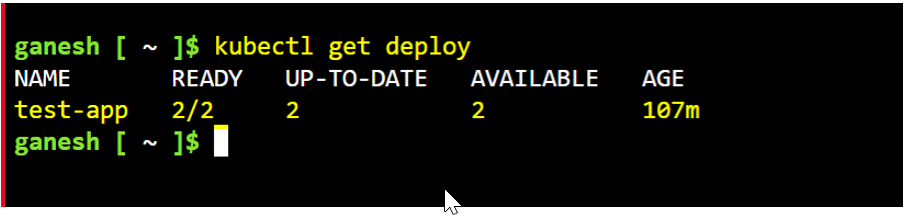
cmd to check the deployed app kubectl get deploy
2 Next, you can create a service for your application with type:ClusterIP.
Note: if you create a service type:LoadBalancer for your application. This service will create with Load Balancer.
apiVersion: v1
kind: Service
metadata:
name: nginx-service
labels:
app: nginx
spec:
selector:
app: nginx
ports:
- port: 80
targetPort: 80
protocol: TCP
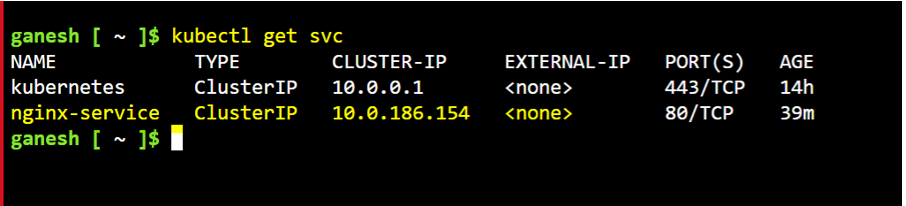
Service created with type: ClusterIP.
cmd to check the service: kubectl get svc
- Create an ingress resource for your application to route the traffic to the service
.
apiVersion: networking.k8s.io/v1
kind: Ingress
metadata:
name: nginxapp
annotations:
kubernetes.io/ingress.class: azure/application-gateway
spec:
rules:
- http:
paths:
- pathType: Exact
path: /
backend:
service:
name: nginx-service
port:
number: 80
Ingress created successfully.
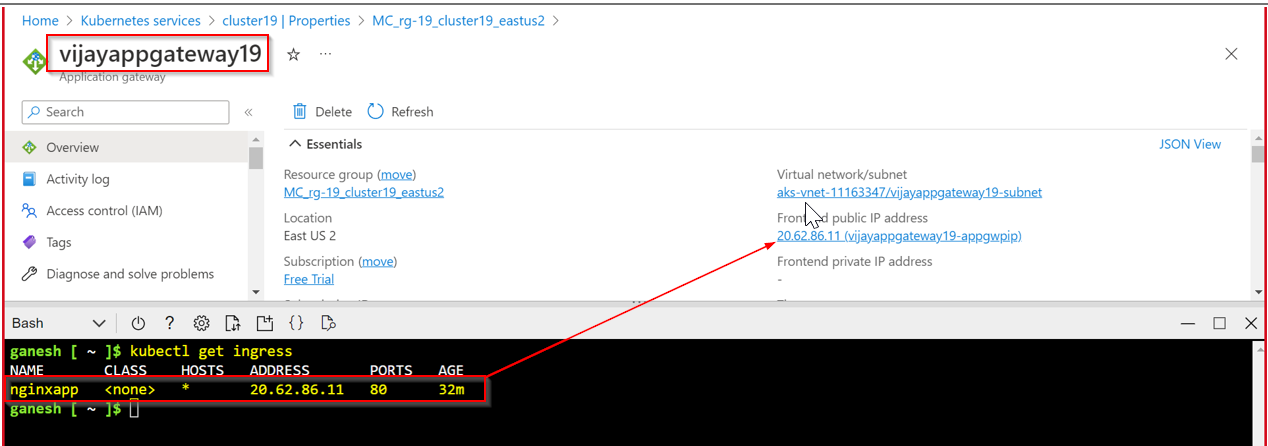
- Once all resources are created Application Gateway Ingress Controller will route the traffic to the service without creating an associated load balancer.
Application is running successfully with application gateway public IP.