1. Preface
In 14 or 15 planning, artificial intelligence and brain science is listed as a national strategy of science and technology strength, neural engineering, and the rapid development of brain-computer interface technology for the human health and strengthening are of great value and future of imaginary space,
As information security professionals, we also see this technology brought about by the information security hidden danger, as early as in 2013, famous hackers barnaby Joyce, jack realized within 15 meters remote invasion of cardiac pacemaker release 830 v voltage, which can kill instantly and cardiac pacemaker is a common human only implantable therapeutic apparatus, while including a wider range of neural engineering equipment for the brain, nerve, computer, prosthesis, extended equipment testing, control, and interaction of many devices, if they pose a safety hazard, malicious use of hackers, will bring a great deal of human and social harm,
We look forward to the neural engineering and the high-speed development of brain-computer interface technology, health and safety, at the same time also hope that they can not because the information security problem is blocked, so the zero zero laboratory (00 SEC) began to work in the field of information security research, we are the traditional defense experts in the field of information security, but in the study of neural engineering, information security, found that both at home and abroad, have no a relatively complete research panorama, this has brought some trouble to us, we will try to classify the field according to the information security concerns, will now share classification maps, in order to offer more white hat they can more quickly cut into the research topic,
Neural engineering and undiscovered talent brain-computer interface technology, this article is just standing in the perspective of information security, at the same time, we are very humble, said we are just entered in this field, the purpose is to do everything we can to avoid the areas threatened by hackers, any mistakes and wrong in this article, please feel free to correct me, contact email: [email protected], will reply you for your letter
2. The overview
We will neural engineering from the point of scene of three categories: nerve detection, signal acquisition and feedback technology; Neural control areas; Neural prosthesis field, this is not the subject in the field of academic classification, but we thought it would be more efficient in information security threats, and defense research,
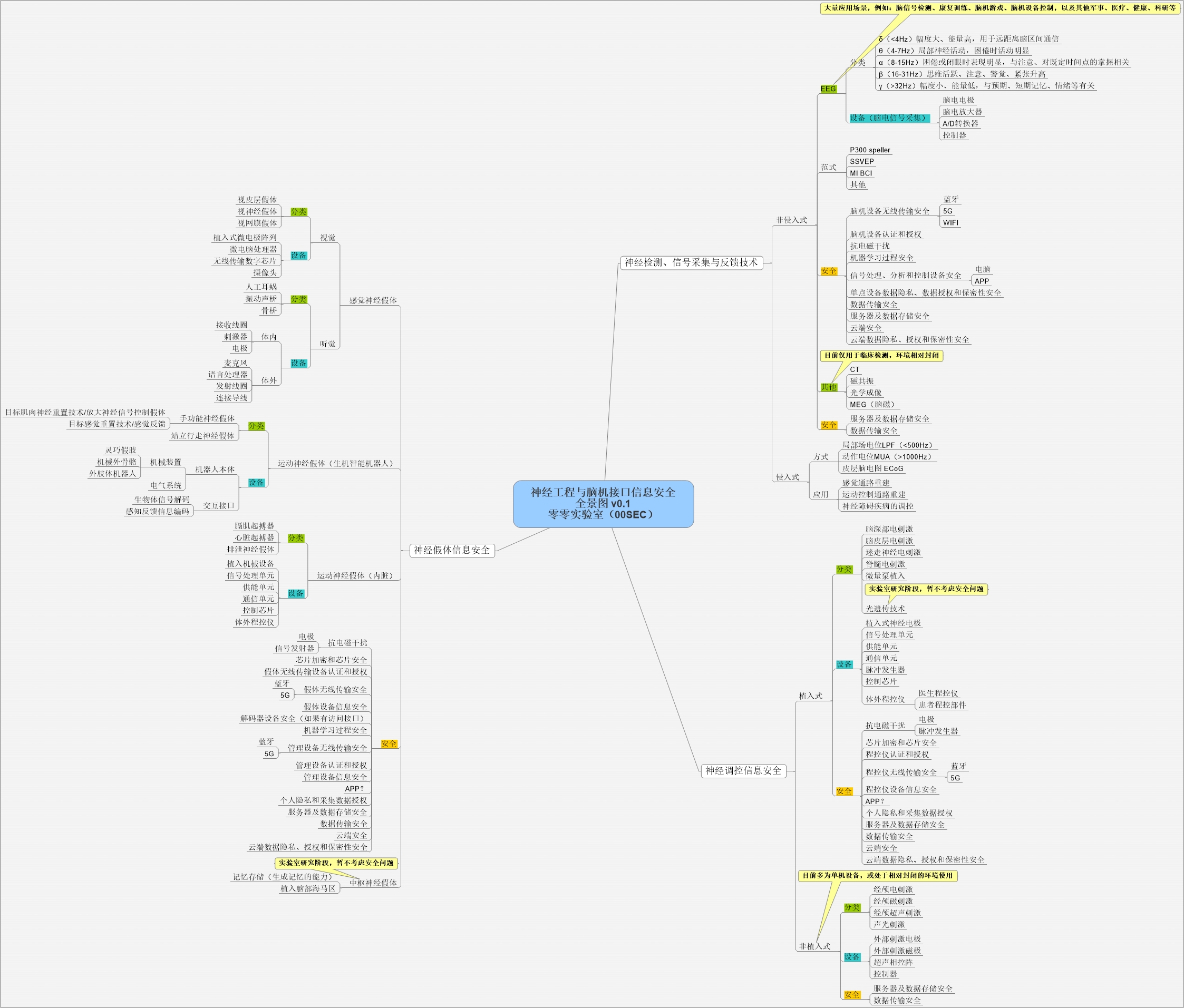
3. Detection of nerve, signal acquisition and feedback technology
Separate out of the part, because this part is the most mature, also is the most widely used, especially based on the idea of EEG in typing, the mind mechanical equipment control, mind games, the body function recovery, even in the military, scientific research and other fields are widely research and application,
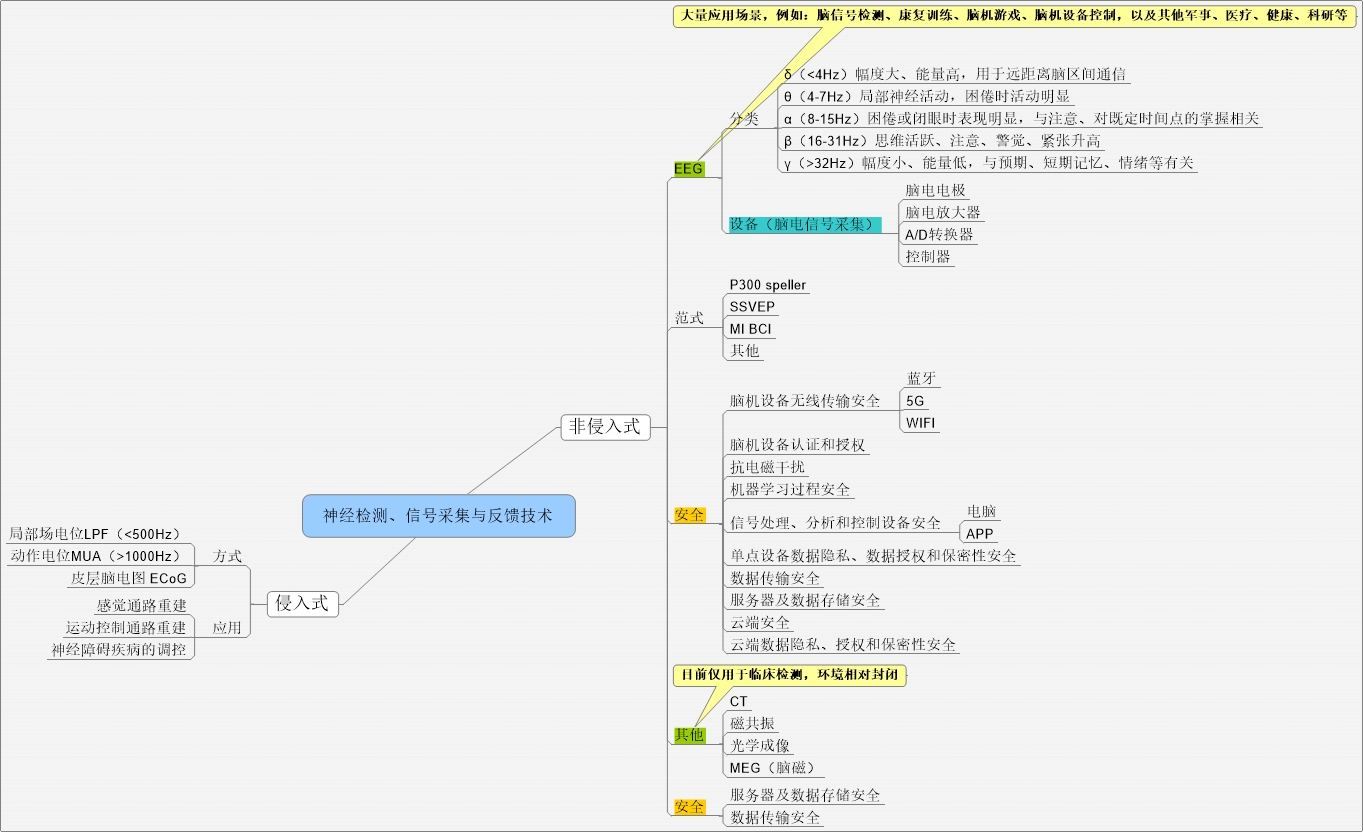
Various forms of eeg cap, especially in the future more portable and portable devices, has been gradually adopted the way of the wireless link (bluetooth, 5 g or WIFI), so the wireless transmission, authentication, authorization, security problem such as resistance to electromagnetic interference should be taken into consideration,
Acquisition of EEG in decoding, analysis and man-machine interactive training, often using machine learning, the possible antagonistic interference, data security issues such as pollution, the aspect of huazhong university of science and technology professor WuDongRui team has been in P300 and SSVEP based on EEG BCI spelling against published their results, by adding a small amount of pollution in the training sample samples to create "back door",
At present most of the signal processing, analysis and control equipment are using the computer, in recent years have also been some using the APP, and there have been some products with the networks and cloud data transmission and storage, noninvasive brain-machine interface for data is biological information (the joys and sorrows of the people, and even deeper thought data), data privacy and authorize, and in a cloud of tube end data storage, transmission, encryption security, the safety of the load data of IT equipment, are potential safety hazard, these aspects should be carried out in accordance with the national level to protect the security requirements of 2.0 points of safety research and safety control,
Computed tomography (CT), magnetic resonance, optical imaging, MEG, etc., due to the currently used only for clinical detection, the environment is closed, and security are relatively easy to control, mainly in terms of servers and data storage and transmission, closer traditional information security field,
Invasive brain-computer interface aspects in the application of the scene and neural control associated with neural prosthesis is deeper, detailed classification, and discuss in the following chapters to do,
4. The neural regulation of information security
In the field of information security scenario consists of implantable neural regulation and non-invasive,

Current non-invasive devices are almost all the use of single equipment or in a relatively closed environment, that part of the security is relatively easy to control, don't do more description,
Implantable devices on the one hand, a single scene is more, on the other hand device to interact with the brain or nerve may have a direct (that is, "write" operation on the brain of some equipment), information security needs more and more in-depth consideration,
, elon musk, Neuralink company released in this year of the size of a coin and implanted brain-computer interface equipment, minimally invasive robot for invasive brain-computer interface technology and practical one step further,
Implanted in the body part can be a whole, may also be divided into direct connection electrodes and other integration equipment two parts, they are no matter what form, generally including electrode, signal processor, power unit, communication unit, such as pulse generator (according to the different types of equipment, including the function of the unit will increase or decrease),
In vitro part generally includes programmable device, the controller is used to monitor and simple operation, may also be decoded according to actual needs, analysis and execution of more complex instructions and operation of the computer, has not been heard of the part using the APP, but with the development of science and technology and mature, perhaps APP will be a trend in the future (a joke, if in the root of electrodes in the brain, can control the discharge to stimulate your brain on his mobile phone was "cool", perhaps the future super soldiers really need never know),
According to the above scenario, the first is to solve the electromagnetic interference resistance and security chip, then implanted part and the part of the certification, authorization, data transmission security problems, is to consider, non-invasive brain machine equipment, compared with non-invasive brain machine equipment can be more accurate access to biological information, even to "write" operation of organisms, so to privacy, the equipment authorization is even more important,
In addition, every single point of implantable devices, including implants, programmed control equipment, computer, etc., can be accessed through the information means to the entity, with the development of the 5 g technology, the communication interface of each single point are likely to become the target of hackers, traditional security certification in the field of information security, security agreement, and even remote overflow problems are likely to arise,
The information and data processing and the IT level of safe operation, this figure has been marked, and section have been mentioned in the last chapter, there is no longer tired,
5. Neural prosthesis information security
Neural prosthesis at present more mature in the field of application in the visual, auditory nerve prosthesis, and artificial organs prosthesis, dexterous prosthetic limbs, mechanical exoskeleton, outside the body aspect has not yet entered the mature markets of the robot, memory storage prosthesis is still at the laboratory research stage,

Visual and auditory prosthetic external equipment mainly includes image, sound pickup equipment, decoding equipment, communications equipment with implants, such as main parts of the implants received signal and the corresponding nerve electrical stimulation,
Implanted part mainly includes the mechanical part of artificial organs, communication unit, power supply, such as control chip, and programmable instrument in vitro, and in particular, in 2013, hackers jack barnaby Joyce, of the implementation is not only the attack of this kind of equipment,
Dexterous prosthetic limbs, mechanical exoskeleton, outer body robot, there are high-tech robots at home and abroad companies, biotechnology companies, brain machine company for design and development, has been part of the experiment and demonstration product release, believe in the near future they will help the disabled recover some damaged limb function, after the mature technology, believe in "iron man", "fighting angel rita o" the scene was no longer a fantasy,
Neural prosthesis is more involved in the field of cranial nerves, speaking, reading and writing and operation, for memory storage, delete, and rewrite, would provide a huge leap in human evolution, the Peking University Dr Hao-jie sun team has achieved to accurately delete memory of rats,
In the field of security still needs from implants, external control equipment, IT equipment, considering such aspects as listed in the figure, and for similar content in the above two chapters are described, in this no longer tired,
It is important to note that neural prosthesis field more involved in mechanical and electrical components, mechanical and electrical parts are made up of many individual units, and even may contain embedded or external complex calculation control unit, because each unit may be accessed through information means to the entities that are likely to become a hacker attacking, so according to the different scenarios and equipment, also need to consider more security threats brought by the communication unit and interface,
6. Conclusion
This article only from the direction of the global information security research summary and scene classification,
00 zero zero laboratory (SEC), affiliated with Beijing zero zero letter Ann technology co., LTD., our goal is to do what we can to technical force against hacker attacks, we love neural engineering and brain machine interface technology, we hope to our growth and development of offensive and defensive technology ability to protect it, expecting that it can also bring mankind a better future,
We are looking forward to have more insight to join in, create a better future for information security,
