The most voted answer in this question (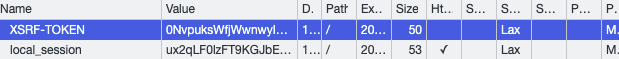
I am not sure whether I am doing some settings wrong or misunderstood about CSRF, but storing an extra CSRF cookie in addition to the session cookie really does not seem to be able to give any extra protection.
Any help would be appreciated.
CodePudding user response:
Not always.
cookie with SameSite value of None will be always sent.
XSRF-TOKEN cookie has SameSite=Lax so it will be only sent at the same website.
https://developer.mozilla.org/en-US/docs/Web/HTTP/Headers/Set-Cookie/SameSite#none
SameSite=NoneCookies will be sent in all contexts, i.e. in responses to both first-party and cross-site requests. If SameSite=None is set, the cookie Secure attribute must also be set (or the cookie will be blocked).
https://developer.mozilla.org/en-US/docs/Web/HTTP/Headers/Set-Cookie/SameSite#lax
SameSite=LaxCookies are not sent on normal cross-site subrequests (for example to load images or frames into a third party site), but are sent when a user is navigating to the origin site (i.e., when following a link).
