I have created an EC2 instance with terraform aws provider. The Instance is an Ubuntu server of free tier t2.micro.
Even though I have followed every Amazon guide about Network ACLs, Security Groups, Route tables, Internet gateways, I still cannot execute a simple command such as
sudo apt-get update
When I log in to my instance from ssh port (22) and execute the sudo command above, I receive back this message:
0% [Connecting to us-east-2.ec2.archive.ubuntu.com (52.15.159.198)]
Resources I have followed:
-
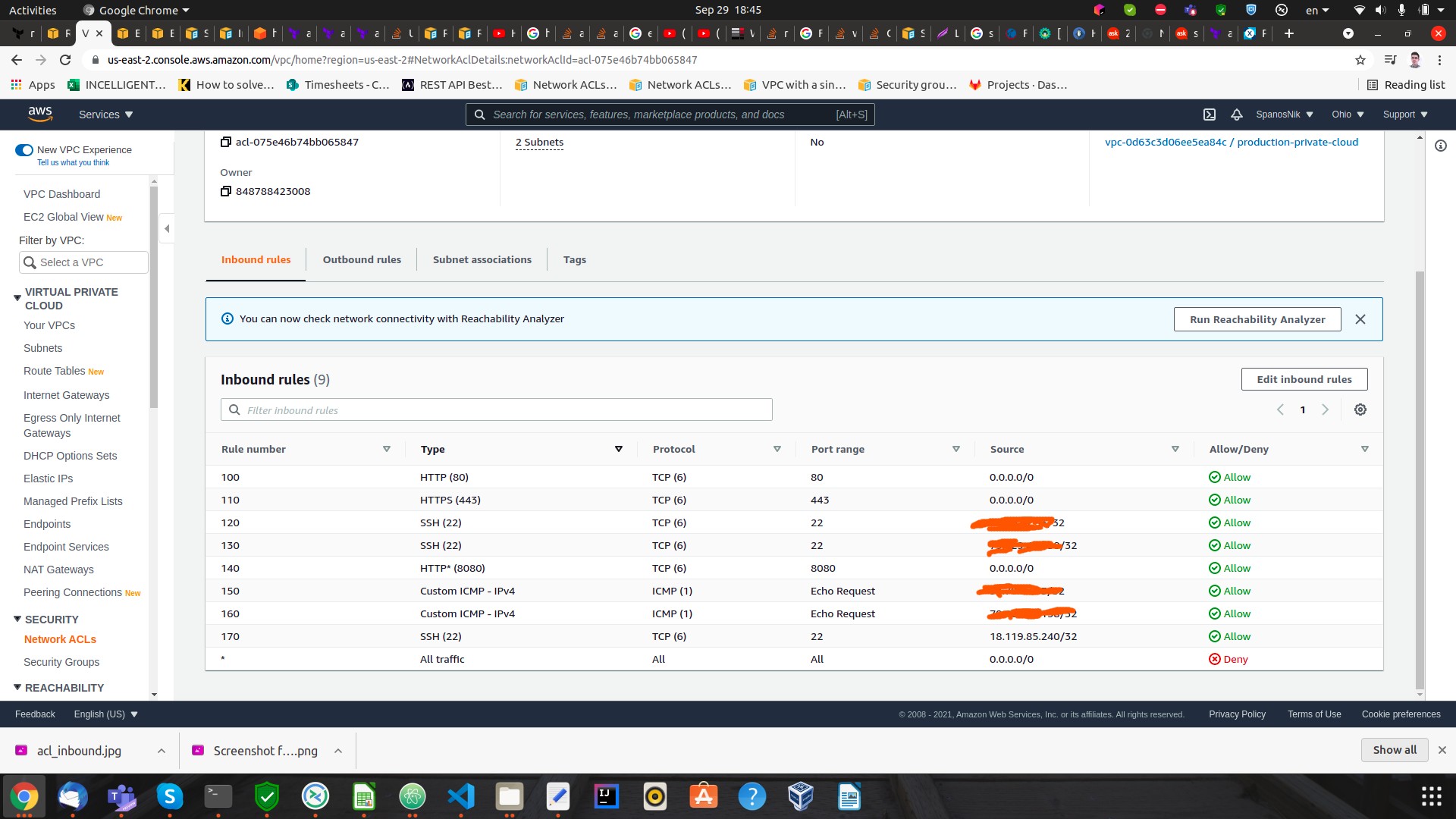
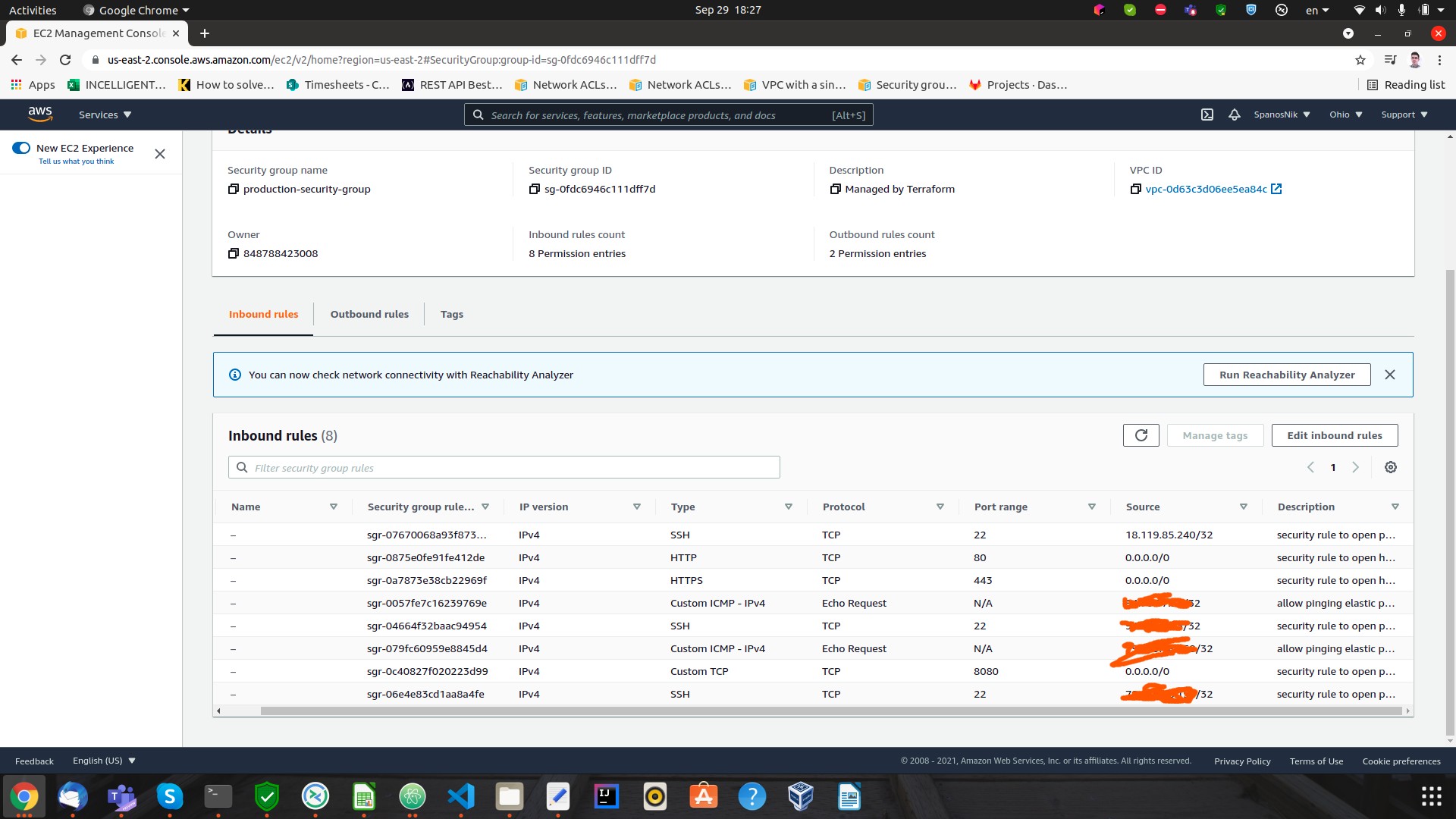
Security group rules:
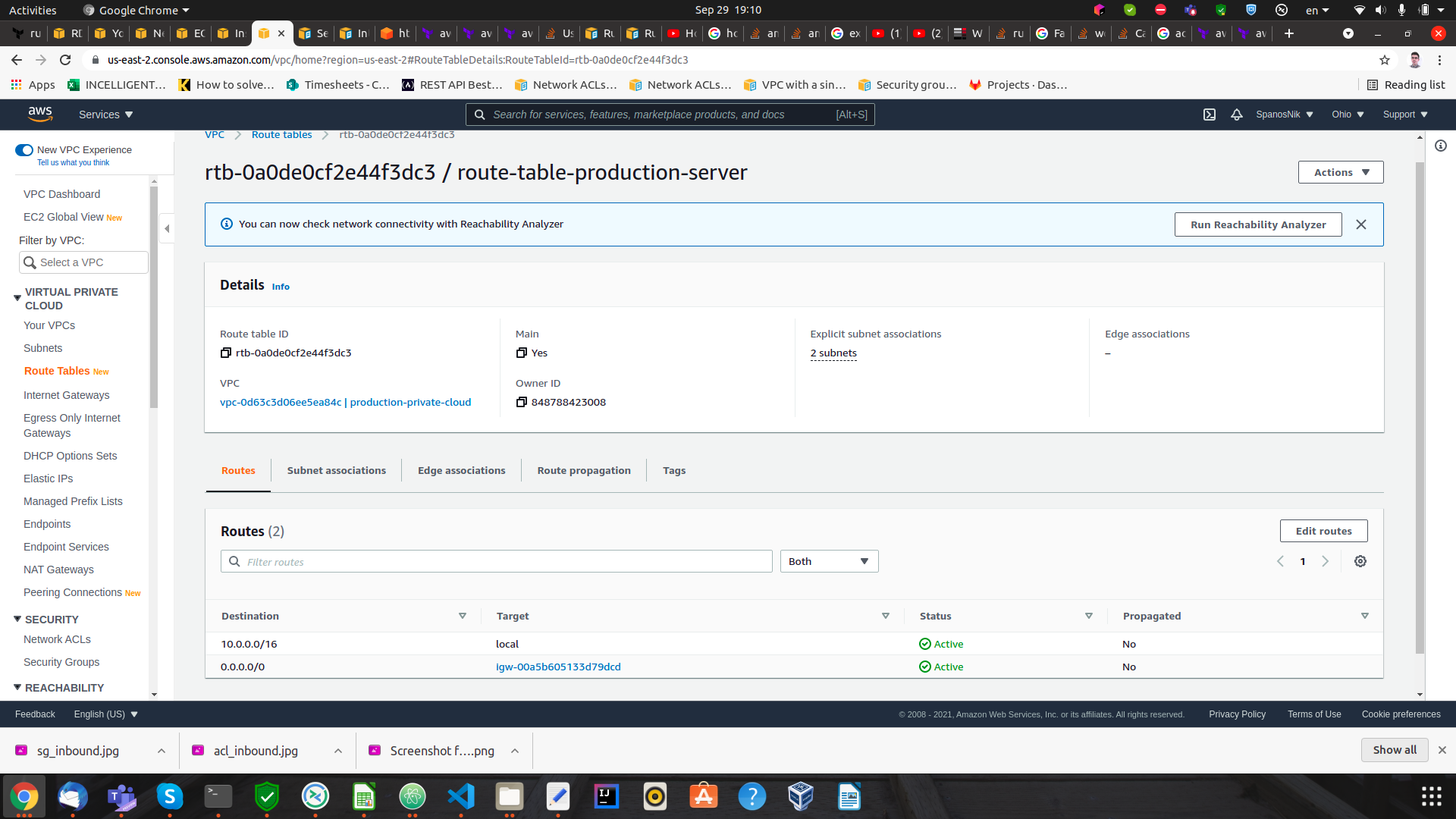
Route table attached to my instance
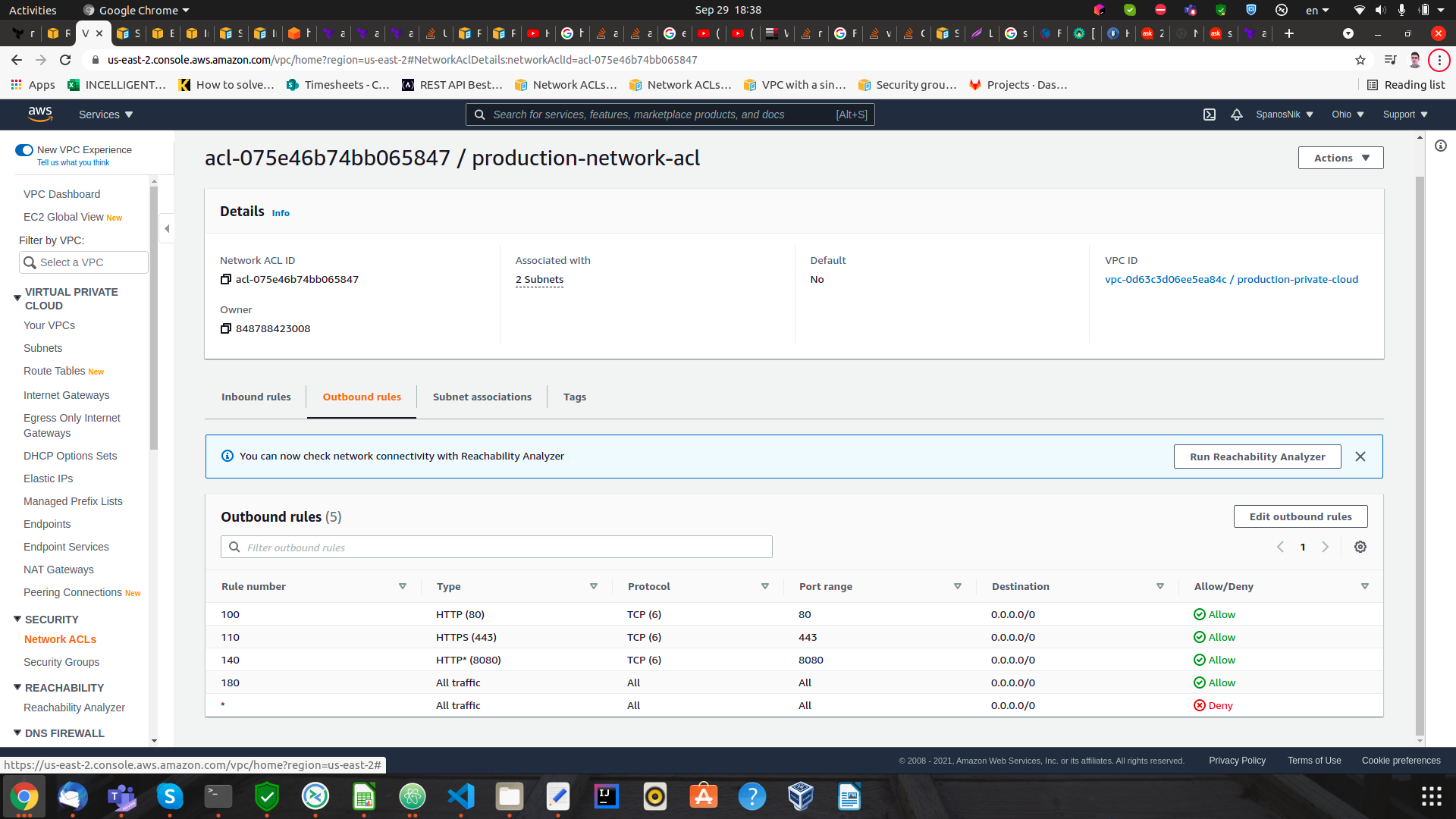
My only concern is that the vpc I use has a main acl network (like a default) which is not the one I use (the one with the many rules in the screenshot above). However, the main route table guides to the correct subnet that is also attached to the correct acl network. I guess this is happening because in terraform I use the aws_network_acl resource and not the aws_default_network_acl.
Thus, my only concern might be that I have a wrong acl network attached to my vpc, however even that acl network has allowed all inbound - outbound traffic. So accessing http shouldn't impose a problem. Since I can't download anything from my ec2 instance, I believe that something else is the root of my problem.
Appreciate any help in advance.
CodePudding user response:
Security Groups are stateful. This means that if traffic is permitted in one direction, then a return response is allowed to come back in. For example, you could open port 80 to Inbound traffic and the web server could respond to the request even if there was no Outbound rule in the Security Group.
In contrast, Network Access Control Lists (NACLs) are stateless. This means that sending a request in one direction does not automatically permit a response in the other direction.
When a web request is made to the Internet to a web server, it goes to port 80 on the remote server. However, the return traffic does not come on port 80. Rather, your request to the remote port 80 comes from a random port on your own computer. Therefore, the NACL must permit return traffic to that random port. This is probably what blocked the response to your web request to download the software.
I used to find this concept very hard to understand. I always thought that requests going to port 80 must come from my port 80. But that's not how it works. Web requests to the Internet will never come from port 80 because that port is associated with the web server on that computer. It actually makes sense because, for example, let's say that Computer A opens two tabs in a web browser and sends a request to
google.com:80andfacebook.com:80. The return traffic from each server needs to come back to a different port so that the browser knows which response to display in each tab.Yes, it is safe to open all NACL ports. In traditional networks, security was only enforced in routers between subnets. This security is mirrored in NACLs. However, the Cloud provides an additional layer of security by using Security Groups that act as firewalls on each resource individually. This is more powerful than traditional network security. Thus, it is quite normal to permit all traffic at the NACL level unless you have a very specific security need, such as creating a DMZ or blocking a particular type of traffic entering the network.