Data signature and authentication process of cryptography in the chain of blocks is a very important application, this article is based on block chain locations for data signature and verification,
This article USES intelligent contract to complete the signature verification, use chain3. Js to complete for the signature of the data and intelligence interactions,
Environment:
Version: scholars nuwa1.0.6. Win. Zip (mainnet) is presented in this paper;
Operating system: 64 - bit Windows 10 home edition,
1. The signature
Implement signature need to two parts: to be signed account data + implementation of the signature, the signature process can use chain3. MC. The sign (), specific code is:
Var Chain3=the require (' Chain3 ');
Var chain3=new chain3 (new chain3. Will. HttpProvider (' http://localhost:8545 '));
Chain3. Personal. UnlockAccount (chain3. MC. Accounts [0], "XXXXXXXXXXXX", 1000);//implementation of signature request unlock account
Var account=chain3. MC. Accounts [0].
Var sha3Msg=chain3. Sha3 (" HELLO MOAC!" );
Var signedData=https://bbs.csdn.net/topics/chain3.mc.sign (account, sha3Msg);
The console. The log + account (" account: ");
The console. The log (" sha3Msg: "+ sha3Msg);
The console. The log (" Signed data: "+ signedData);
In the code above, will first signed data "HELLO MOAC!" To generate the hash strings, use chain3. Sha3 (" HELLO MOAC!" ), then we use the current connection node of the first default account to sign, this time need chain3. Personal. UnlockAccount (chain3. MC. Accounts [0], "XXXXXXXXXXXX", 1000) to open the account data signature used, it is important to note that when you open your account, there may be a security risk, because other programs can access nodes for similar signs and this means that they can forge your data, including launched in the name of your trading, turn away your money,
Running results:
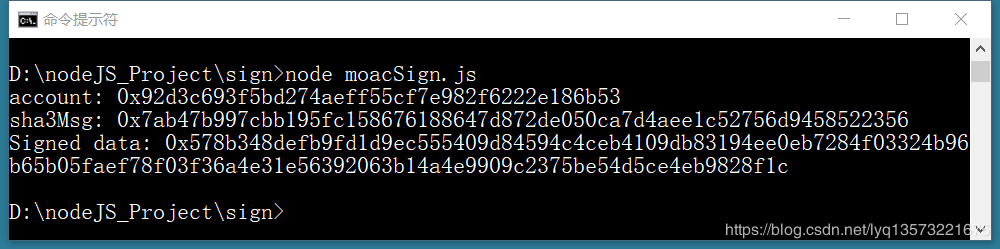
Return value Signed data, a total of 132 bytes (get rid of the '0 x' in front of the word is 130 bytes), in ECDSA (EC is short for "elliptic curve", DSA is short for "digital signature algorithm") signature algorithms, the return value can be divided into three parts: r, s, v, among them former 0 ~ 66 bytes for r, 66 ~ 130 bytes for s, between 130 ~ 132 bytes for v,
Then we can print it out, in the next part is used, verify the signature, the part of the complete code is as follows:
Var Chain3=the require (' Chain3 ');
Var chain3=new chain3 (new chain3. Will. HttpProvider (' http://localhost:8545 '));
Chain3. Personal. UnlockAccount (chain3. MC. Accounts [0], "XXXXXXXXXXXX", 1000);//implementation of signature request unlock account
Var account=chain3. MC. Accounts [0].
Var sha3Msg=chain3. Sha3 (" HELLO MOAC!" );
Var signedData=https://bbs.csdn.net/topics/chain3.mc.sign (account, sha3Msg);
The console. The log + account (" account: ");
The console. The log (" sha3Msg: "+ sha3Msg);
The console. The log (" Signed data: "+ signedData);
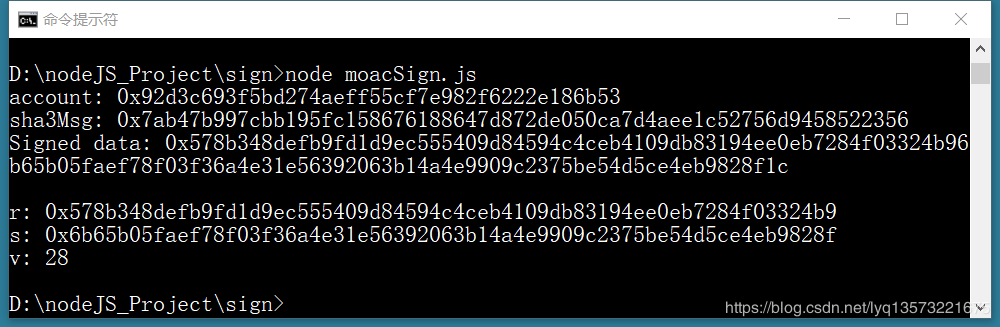
Let r=signedData. Slice (0, 66);
Let s='0 x + signedData. Slice (66, 130);
Let v='0 x + signedData. Slice (130, 132);
V=chain3. ToDecimal (v);
The console. The log ();
The console. The log (' r: ', r);
The console. The log (' s: 's);
The console. The log (' v: ', v);
Running results:
2. Verify
Signature finished, how can we verify some data which account of the signature is signed?
In this case, verify the signature by ecrecover function to realize intelligent contracts,
Ecrecover receives the original data of hash value (that is, the output above sha3Msg) and r/s/v as input parameters, such as, return to implement the signature account address,
Implementation through contracts, so we just need to get the signature of the address, and comparing the real address, if the address is consistent, means verification passed,
Intelligent contract code is as follows:
Pragma solidity ^ 0.4.15;
Contract Auth {
The function verify (bytes32 hash, uint8 v, bytes32 r, bytes32 s) constant returns (address retAddr) {
Bytes memory prefix="\ x19MoacNode Signed Message: \ n32 by mechanical blending".
Bytes32 prefixedHash=sha3 (prefix, hash);
Return ecrecover (prefixedHash, v, r, s);
}
}
Contract will be Signed Message to add "\ x19MoacNode Signed Message: \ n32 by mechanical blending" prefix, so actually being Signed data is not the Message hash value, but the Message of the hash value plus prefix, hash value, again to very attention to this, otherwise later will verify the signature is not successful,
Ecrecover thought is, can be calculated corresponding to the public key for creating ECDSA signature private key, the two extra bytes are usually provided by the signature, the signature itself is elliptic curve points of R and S two (code), and two additional V is to restore the public key needed,
It also explains why the return type is the address: it returns corresponding to restore the public key (i.e., its sha3/keccak hash) address, that means the actual verification signature, check the return address is equal to the corresponding private key has signed the hash address,
Will be deployed to the intelligent contract chain mainnet stone blocks, get the address of the contract and abiString, for the next interact and contract code,
Const contract=chain3. MC. Contract (abiString) at (contractAddr);
The console. The log (contract. Verify (sha3Msg, v, r, s));
The console. The log (account);
Running results:
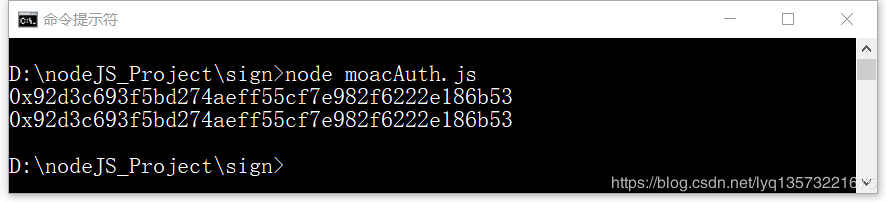
Can see the implementation after signature address and the return address, signature by verifying,
Will contract abiString save to file./Auth - abi. Json;
This part of the complete code moacAuth. Js:
Var Chain3=the require (' Chain3 ');
Var chain3=new chain3 (new chain3. Will. HttpProvider (' http://localhost:8545 '));
Var contractAddr="0 x273c467c9404e6867d873203805aaffad20aac93";
Const account=chain3. MC. Accounts [0].
Const abiString=the require ("../Auth - abi. Json ");
Chain3. Personal. UnlockAccount (chain3. MC. Accounts [0], "XXXXXXXXXXX", 1000);
Let sha3Msg=chain3. Sha3 (" HELLO MOAC!" );
Let signedData=https://bbs.csdn.net/topics/chain3.mc.sign (account, sha3Msg);
Let r=signedData. Slice (0, 66);
Let s='0 x + signedData. Slice (66, 130);
Let v='0 x + signedData. Slice (130, 132);
V=chain3. ToDecimal (v);
Const contract=chain3. MC. Contract (abiString) at (contractAddr);
The console. The log (contract. Verify (sha3Msg, v, r, s));
The console. The log (account);
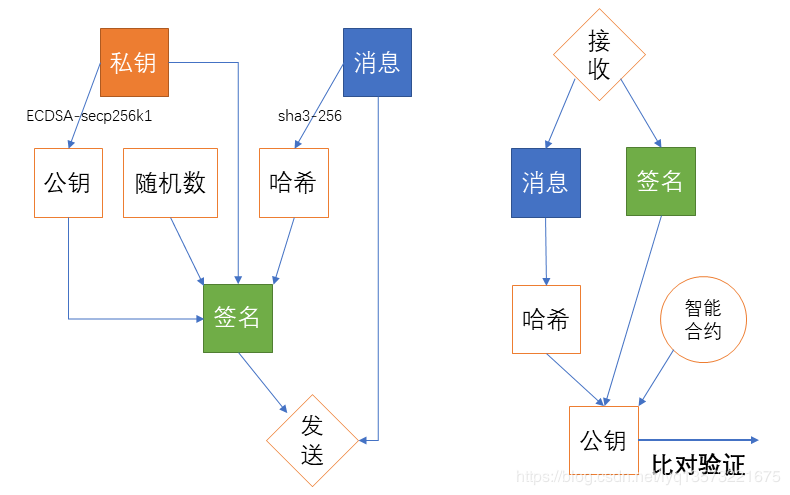
As you can see, in the chain of blocks used in the intelligent the signature of the contract to complete the data and validation is relatively simple, logic diagram is as follows:
3. Direct signature and verification
Step 1 and step 2, by deploying intelligent contract verification,
Also can directly use the private key signature, then the public key is obtained by analytical signature information or address, so you don't need to deploy intelligent contracts,
//run 'NPM install eth - crypto - save'
Const EthCrypto=the require (' eth - crypto ');
nullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnull
