I'm going to build a server infrastructure through AWS.
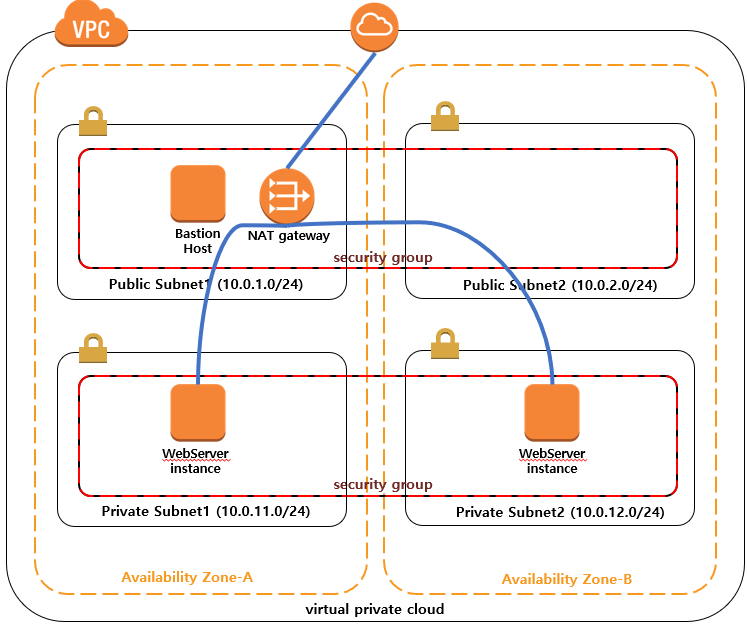
Among them, in order to strengthen the security aspect, we will put all web servers in the private subnet and manage them through the bastion host.
The rough structural map is attached as first photo file. (The ip address is just an example)
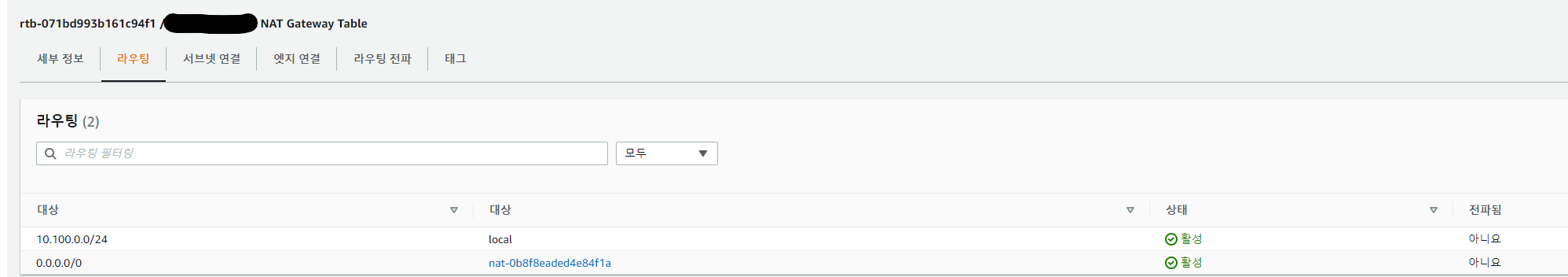
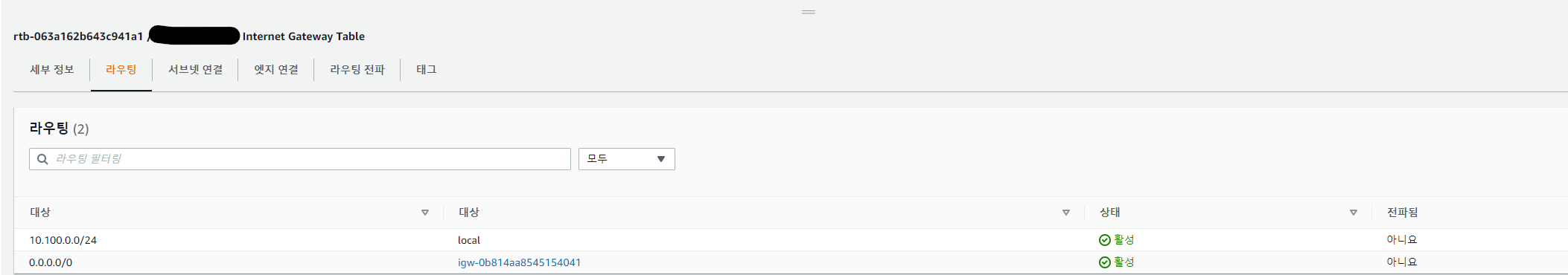
To complete this structure, a VPC with one public subnet and one private subnet was created, the public subnet connected to the routing table of the Internet gateway, and the private subnet connected to the routing table of the NAT gateway. The structure is attached as second and third.
In this situation, we created an ec2 on the private subnet and put up a simple Express server for testing purposes, and left port 3000 open. In this situation, I searched for nat gateway's EIP in the Internet address window to access the express server, but it was not accessible.
I allowed 3000 port from anywhere IPv2 addresses.
There are two main questions here.
- I wonder why you can't access the express server.
- NAT Gateway is used to access Private Subnet from outside, and if multiple servers are running on that Private Subnet from different instances (with different Private IP addresses), I wonder if there is any way to access a specific server.
CodePudding user response:
These days, a common way of accessing instances in both private and public subnets is through SSM Session Manager. The manager has many benefits over traditional ssh approach. Some of the are:
- no need for a bastion host,
- manage and log SSM Session Manager permissions and activities using IAM and
- works through a browser.
To use SSM Session Manager, the three things are needed:
- SSM Agent on the instance - its preinstalled and running on all popular AMI images (Amazon Linux 2, Ubuntu, ...)
- IAM role with permissions for the agent to allow for SSM access.
- Connectivity to SSM service. Since you have NAT this is not a problem in a case. Other-way would be through VPC interface endpoint, which does not require NAT.