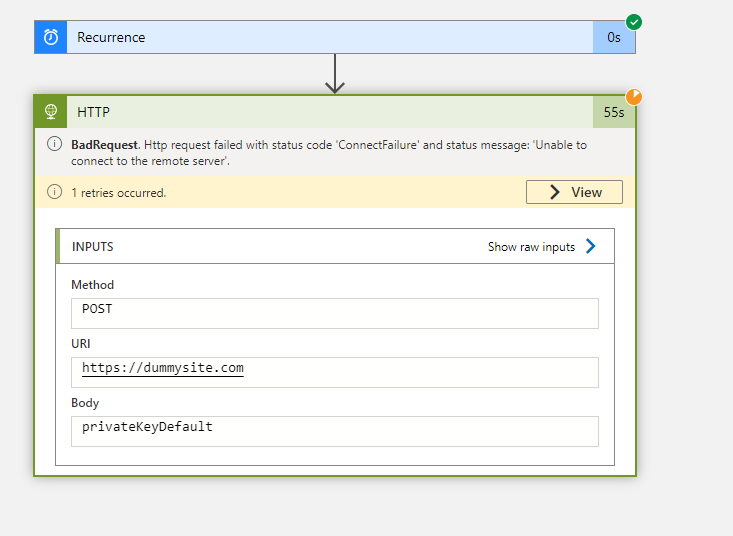
I've set up the problem in the these two files. The template is simply POSTing the parameter with a fake url to check the value.
read_secret_params.json
{
"$schema": "https://schema.management.azure.com/schemas/2019-04-01/deploymentParameters.json#",
"contentVersion": "1.0.0.0",
"parameters": {
"ftpPrivateKey": {
"reference": {
"keyVault": {
"id": "/subscriptions/dummyid/resourceGroups/dummyrg/providers/Microsoft.KeyVault/vaults/myvault"
},
"secretName": "mysecret"
}
}
}
}
read_secret_template.json
{
"$schema": "https://schema.management.azure.com/schemas/2019-04-01/deploymentTemplate.json#",
"contentVersion": "1.0.0.0",
"parameters": {
"ftpPrivateKey": {
"type": "securestring"
}
},
"resources": [
{
"type": "Microsoft.Logic/workflows",
"apiVersion": "2019-05-01",
"name": "read-secret",
"location": "East US",
"properties": {
"definition": {
"$schema": "https://schema.management.azure.com/providers/Microsoft.Logic/schemas/2016-06-01/workflowdefinition.json#",
"contentVersion": "1.0.0.0",
"triggers": {
"Recurrence": {
"recurrence": {
"frequency": "Week",
"interval": 1
},
"type": "Recurrence"
}
},
"actions": {
"HTTP": {
"inputs": {
"body": "[parameters('ftpPrivateKey')]",
"method": "POST",
"uri": "https://dummysite.com"
},
"runAfter": {},
"type": "Http"
}
},
"outputs": {}
},
"parameters": {}
}
}
]
}
The first issue is, when I try to deploy via the portal, no value comes thru for the parameter so it can't create it due to the validation error "Validation failed. Required information is missing or not valid.". Is this because it's not able to read the secret, permissions thing? NOTE: the key vault is also created by myself so I am the owner.
I can get around the validation error and successfully deploy by adding a default value as follows:-
"parameters": {
"ftpPrivateKey": {
"type": "securestring",
"defaultValue": "privateKeyDefault"
}
},
But when I run the logic app, it's using the default value in the POST command so it seems like it's not pulling the secret out of the key vault.
So in summary I have 2 questions:-
- Has this test proved that the logic app is not reading the secret OR might it have successfully read the secret but is for some reason displaying the default value in the POST command?
- If it is not reading the secret, can anyone suggest a cause fix?
CodePudding user response:
If I deploy using the Azure CLI then it works i.e. gets the secret from Azure Key Vault. If deployed in the portal then it always uses the default value.