I'm trying to do the azure service principle password rotation using Terraform, with the latest versions of azuread they have provided this rotation feature,
resource "time_rotating" "test" {
rotation_years = 5
lifecycle {
create_before_destroy = true
}
}
resource "azuread_service_principal_password" "service_principal_password" {
service_principal_id = var.sp_internal_id
rotate_when_changed = {
rotation = time_rotating.test.id
}
lifecycle {
create_before_destroy = true
}
}
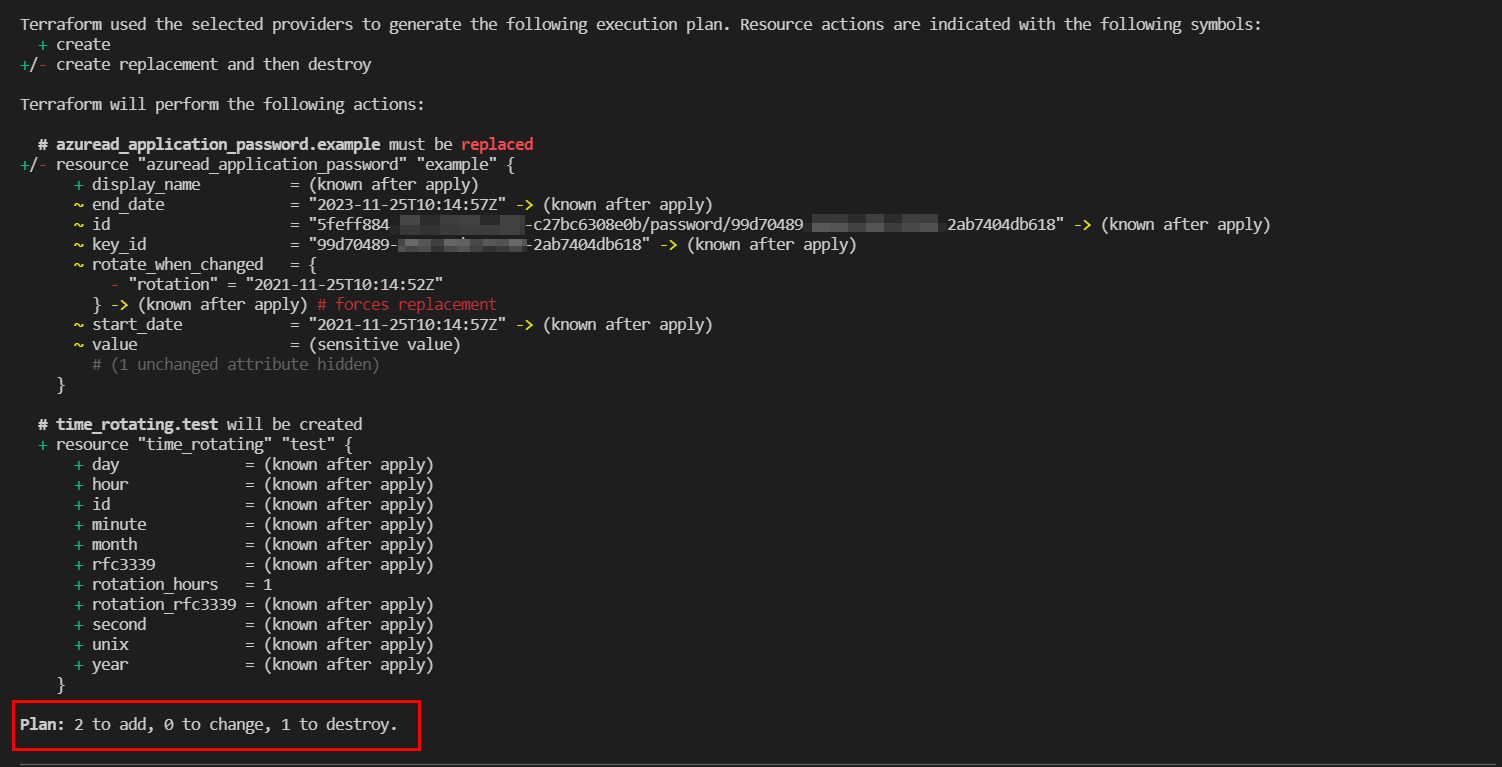
I just want to when I add the attribute rotate_when_changed it will create a new password resource according to the timestamp I set right ? and I want to know that this is a feature that Terraform only provides or this is a feature from Azure AD ? since Azure AD does not provide the key rotation feature, I'm wondering how Terraform is achieving this rotation ?
CodePudding user response:
I just want to when I add the attribute rotate_when_changed it will create a new password resource according to the timestamp I set right ? and I want to know that this is a feature that Terraform only provides or this is a feature from Azure AD ? since Azure AD does not provide the key rotation feature, I'm wondering how Terraform is achieving this rotation ?
You are correct its a terraform feature only and not a AzureAD feature. When we create a password from terraform it no longer uses value and if you are not providing any end_date_relative then it sets the expiry to a default value of 2 years. But due to security reasons if we wanted to change the value of the password as per time rotation then we can just set the rotate_when_changed and modify it.
This was suggested and enhanced in this 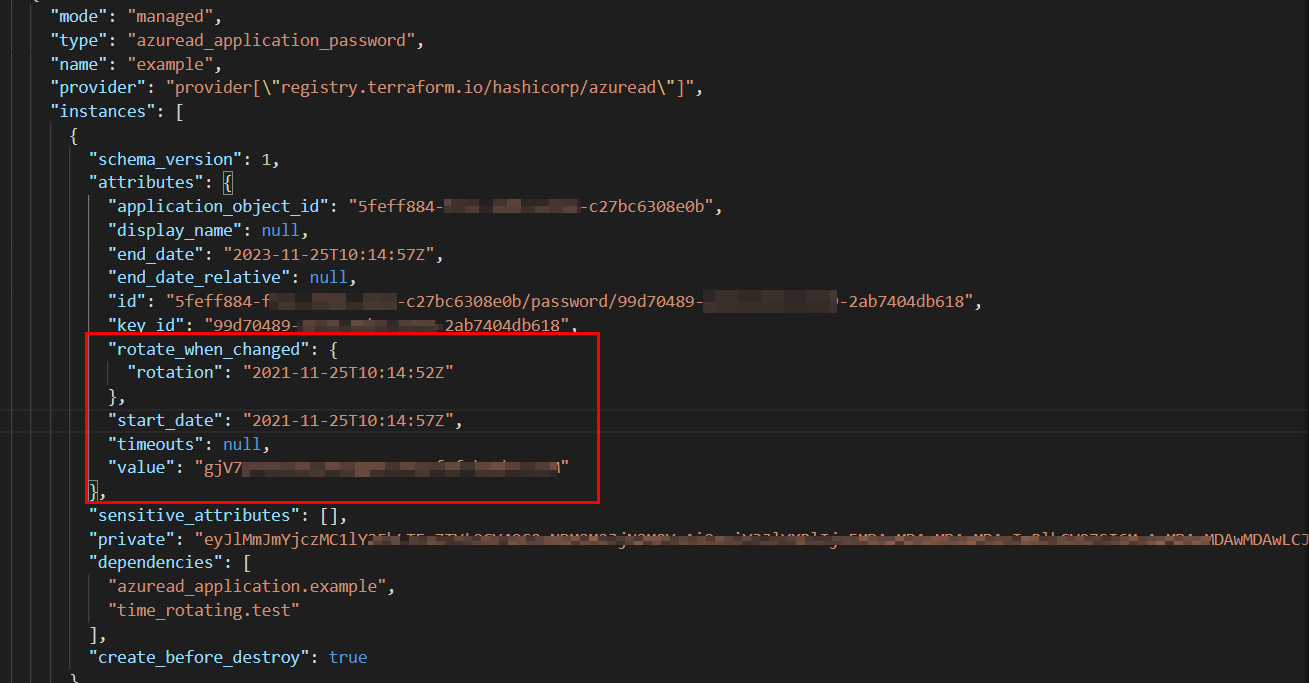
After 1 Hour if I do a terraform Plan , then it shows that the password will be replaced as below , but before 1 hour it will just show no changes detected:
Note: This is useful as you won't have to destroy the password block again and recreate it . Only when your time rotation gets completed , if you perform apply then terraform will just replace the password block and again set the time rotation as per your requirement.