I am trying to provision a simple keyvault in azure using terraform and I get the following error:
Error: retrieving
contactfor KeyVault: keyvault.BaseClient#GetCertificateContacts: Failure sending request: StatusCode=0 -- Original Error: context deadline exceeded
And here's my terraform snippet:
# data "azurerm_client_config" "current" {}
data "azuread_client_config" "current" {}
resource "azurerm_key_vault" "aks_key_vault" {
name = var.aks_kv_name
location = var.location
resource_group_name = var.rg_name
enabled_for_disk_encryption = true
tenant_id = data.azuread_client_config.current.tenant_id
# soft_delete_retention_days = var.aks_kv_soft_delete_retention_days
# purge_protection_enabled = false
sku_name = var.aks_kv_sku
access_policy {
tenant_id = data.azuread_client_config.current.tenant_id
object_id = data.azuread_client_config.current.object_id
key_permissions = var.aks_kv_key_permissions
secret_permissions = var.aks_kv_secret_permissions
storage_permissions = var.aks_kv_storage_permissions
}
tags = merge(var.common_tags)
}
and here's the variables.tf
# Key Vault related variables
aks_kv_name = "jana-azure-csi-kv"
aks_kv_soft_delete_retention_days = 7
aks_kv_sku = "standard"
aks_kv_key_permissions = ["Get"]
aks_kv_secret_permissions = ["Get"]
aks_kv_storage_permissions = ["Get"]
Can someone help me understand what is the issue and how to fix it?
terraform version:
Terraform v1.3.6
on darwin_amd64
azurerm version:
version = "=3.0.0"
CodePudding user response:
'context deadline exceeded' means the respected action won't be done with in timeframe. Mostly it was caused because of network connection issue.
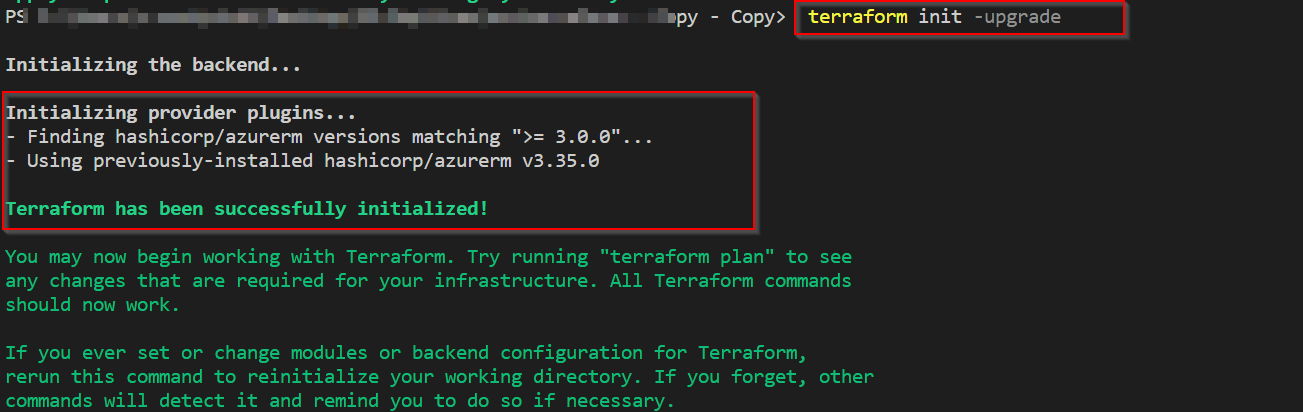
Here the issue was caused because of terraform version, as part of solution please upgrade or keep > on provider From: version = "3.0.0" To version = ">=3.0.0"
after that please run below command
terraform init -upgrade
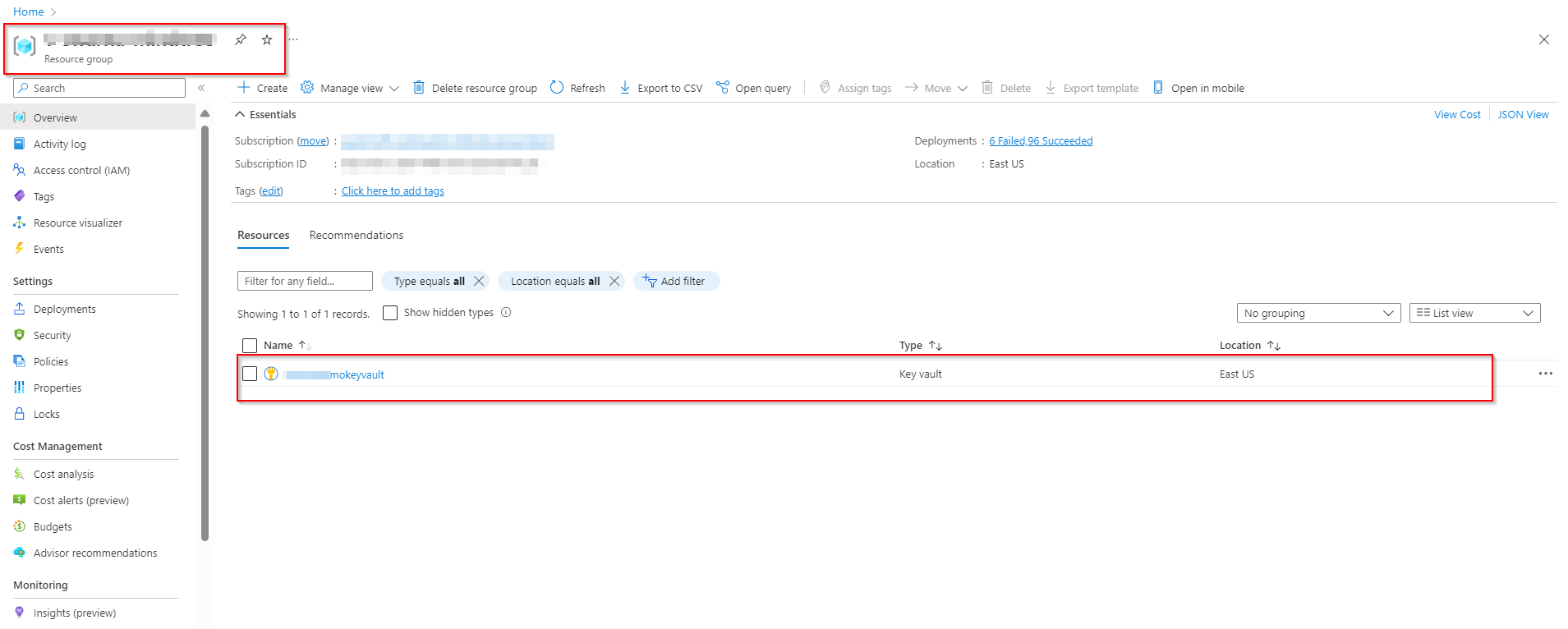
Replicate the same issue via below code. Here is the code snippet used to create keyvault
Main tf file as follows:
data "azurerm_resource_group" "example" {
name = "**********"
}
provider "azurerm" {
features {
key_vault {
purge_soft_delete_on_destroy = true
recover_soft_deleted_key_vaults = true
}
}
}
data "azurerm_client_config" "current" {}
resource "azurerm_key_vault" "example" {
name = "swarnademokeyvault"
location = data.azurerm_resource_group.example.location
resource_group_name = data.azurerm_resource_group.example.name
enabled_for_disk_encryption = true
tenant_id = data.azurerm_client_config.current.tenant_id
soft_delete_retention_days = 7
purge_protection_enabled = false
sku_name = "standard"
access_policy {
tenant_id = data.azurerm_client_config.current.tenant_id
object_id = data.azurerm_client_config.current.object_id
key_permissions = [
"Get",
]
secret_permissions = [
"Get",
]
storage_permissions = [
"Get",
]
}
}
Provider tf file as follows:
terraform {
required_version = "~>1.3.3"
required_providers {
azurerm = {
source = "hashicorp/azurerm"
version = ">=3.0.0"
}
}
}
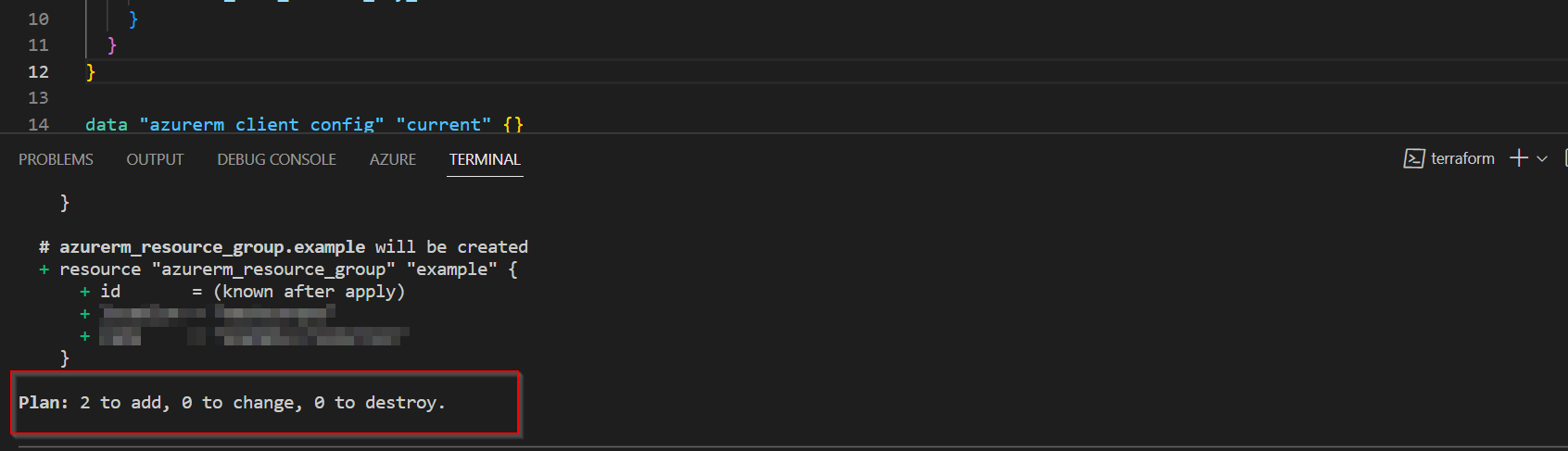
When we ran below command
terraform plan
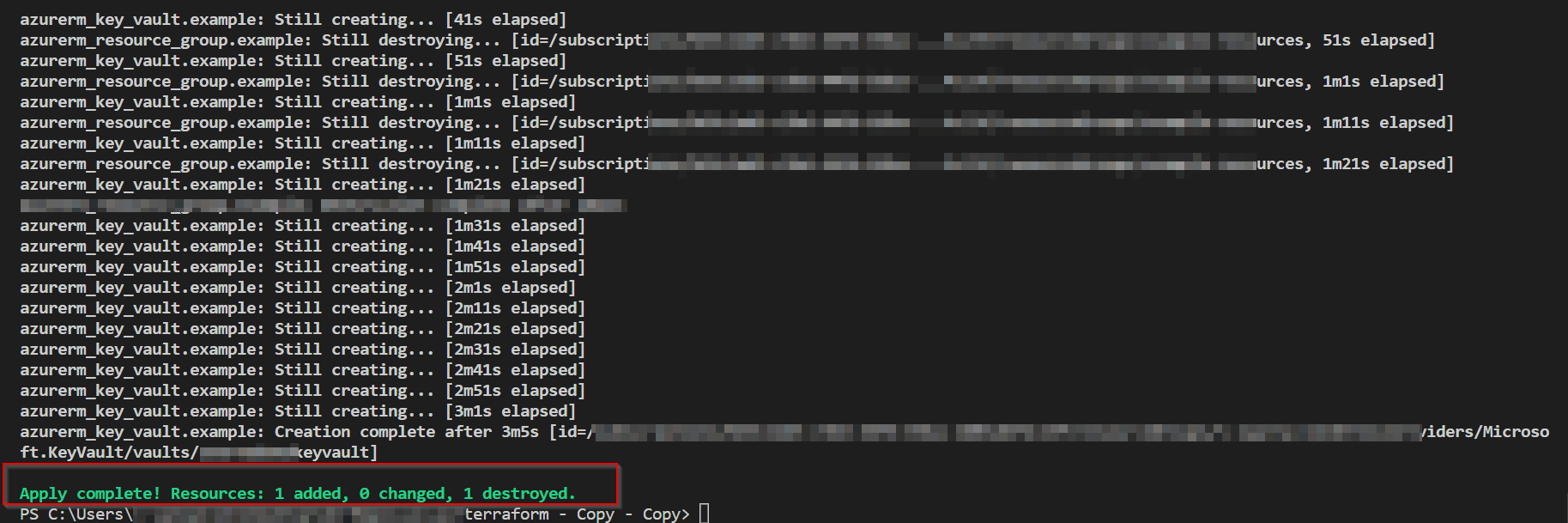
While run apply
terraform apply -auto-approve
Verification: