I'm getting the following error when trying to log in to my Blazor App that is using Microsoft AAD Authentication. The account I'm using to log in is an organizational account outside my Tenant. The login works when I use my personal live.com account.
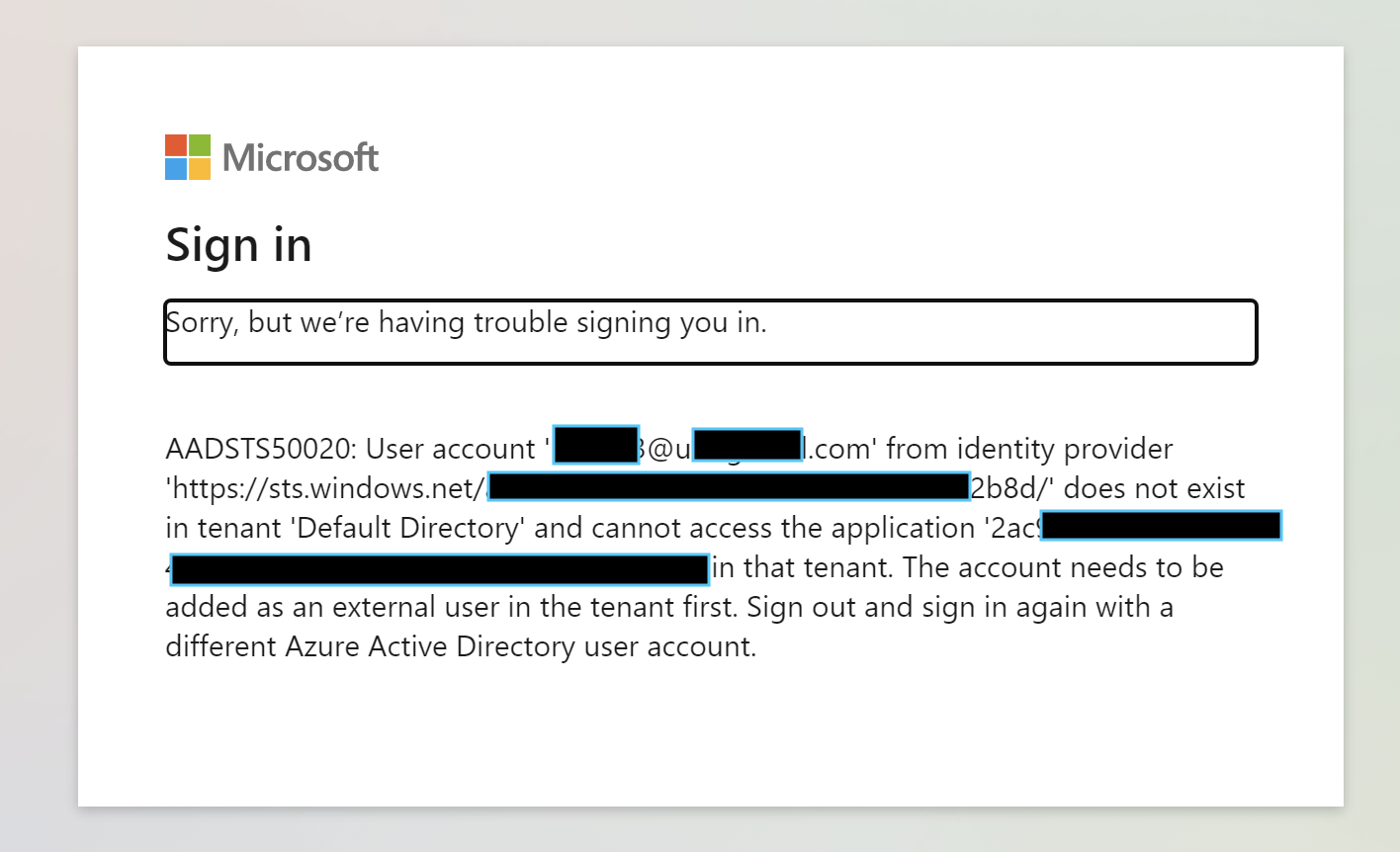
A user account from identity provider *** does not exist in the tenant.The account needs to be added as an external user in the tenant first. Sign out and sign in again with a different Azure Active Directory user account.
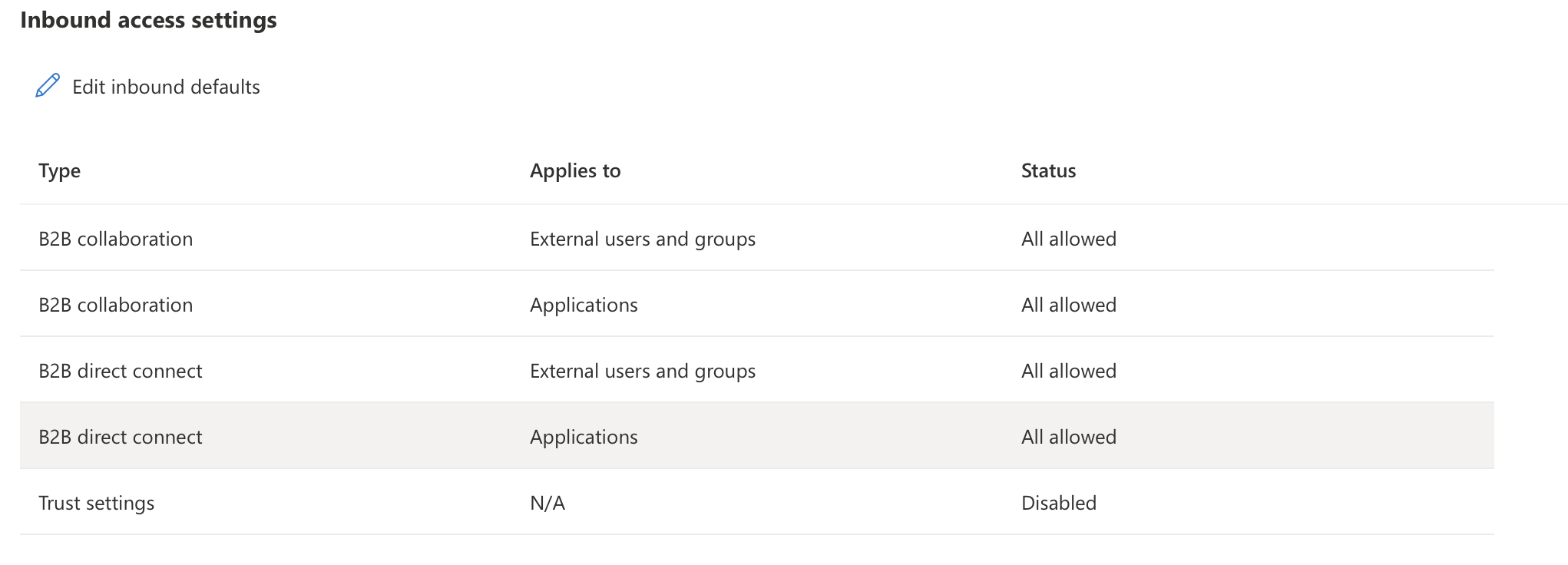
I have allowed Cross Tenant access to the application using the following settings
and also allowed External tenant access in the app registration
CodePudding user response:
I tried to reproduce the same in my environment and got the same error as below:
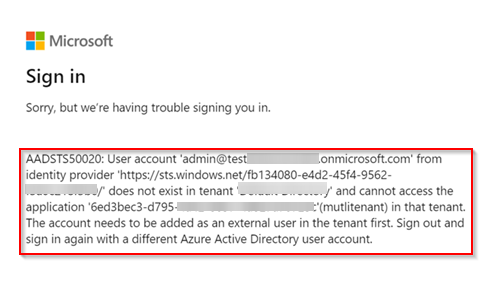
As you are making using of https://login.microsoftonline.com/TenantId/oauth2/v2.0/ endpoint the users from other organizations can't access the application.
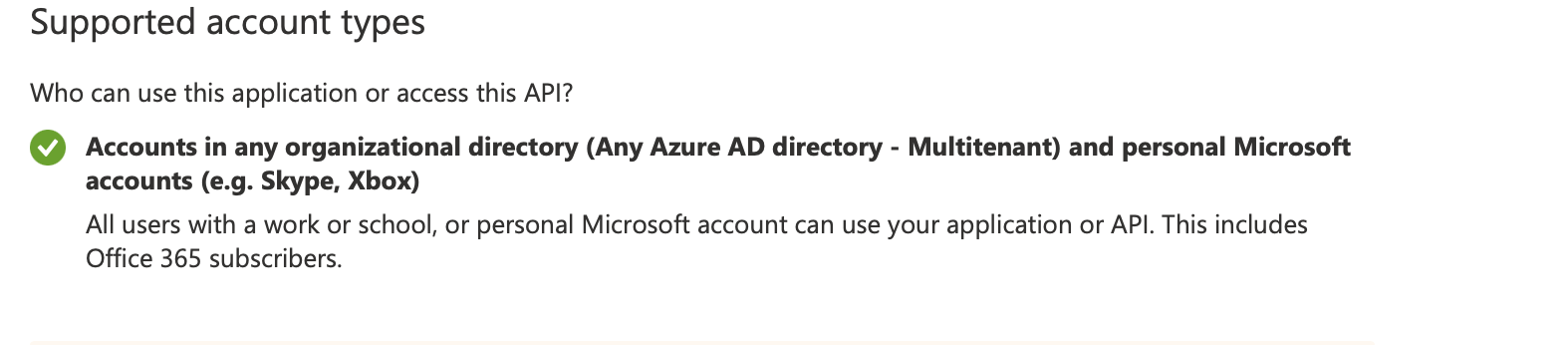
To resolve the error, make sure to use common endpoint as the application is configured as (Any Azure AD directory - Multitenant) and personal Microsoft accounts:
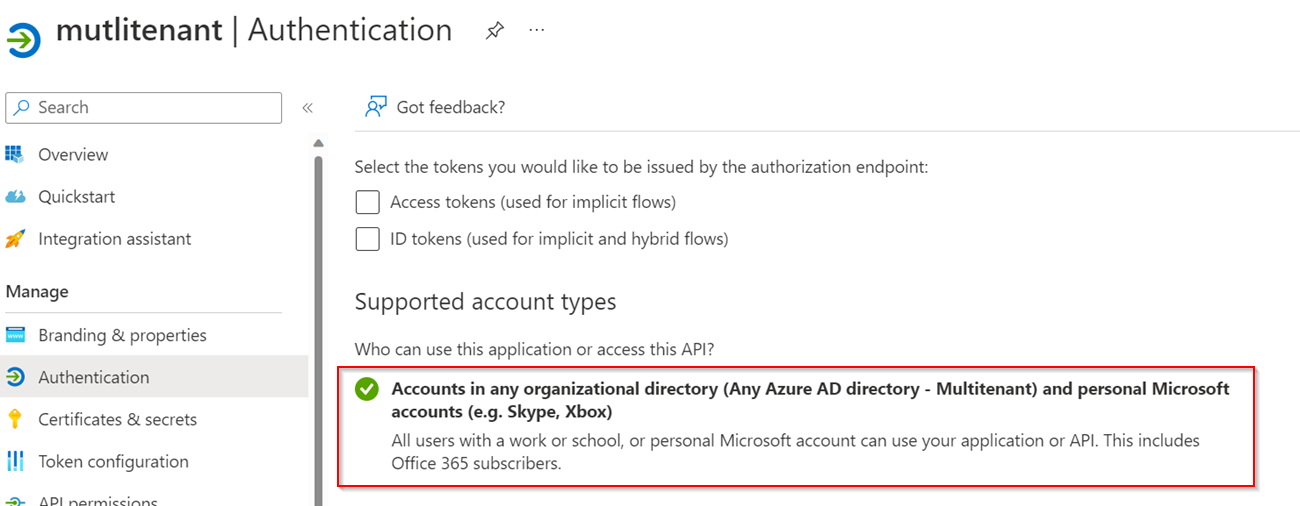
I used the below endpoint to authorize to the Application:
https://login.microsoftonline.com/common/oauth2/v2.0/authorize
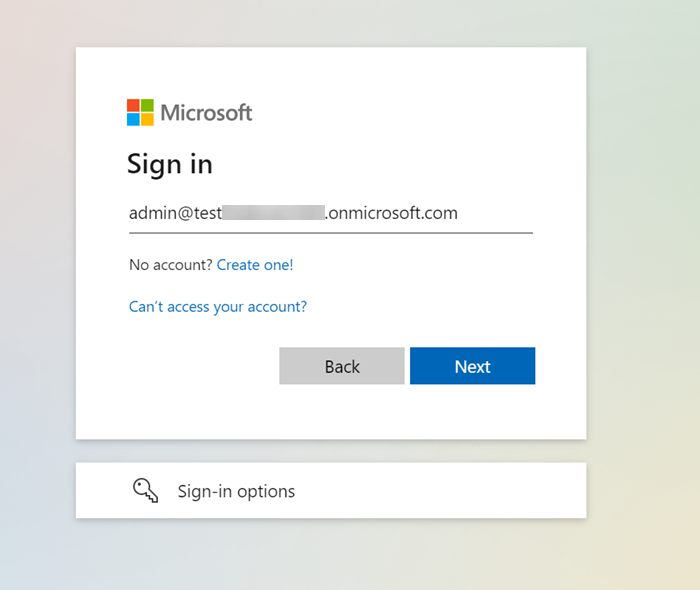
I tried to sing-in with other organizational account outside my Tenant:
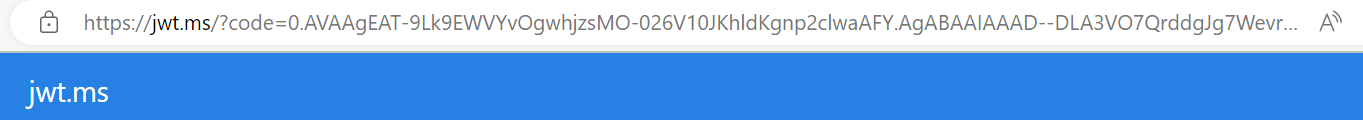
I am able to successfully login to the Application like below:
In the appsettings.json file, update the parameters like below:
"AzureAd": {
"Instance" : "https://login.microsoftonline.com/"
"Domain": "DomainName",
"ClientId": "ClientID",
"TenantId": "common" ,
"callbackpath": "redirecturi"
}
Note:
For Single-Tenant account type, value should be "
TenantId"
For Multitenant account type, value should be "organizations" For Multitenant and personal Microsoft accounts type, value should be "common"
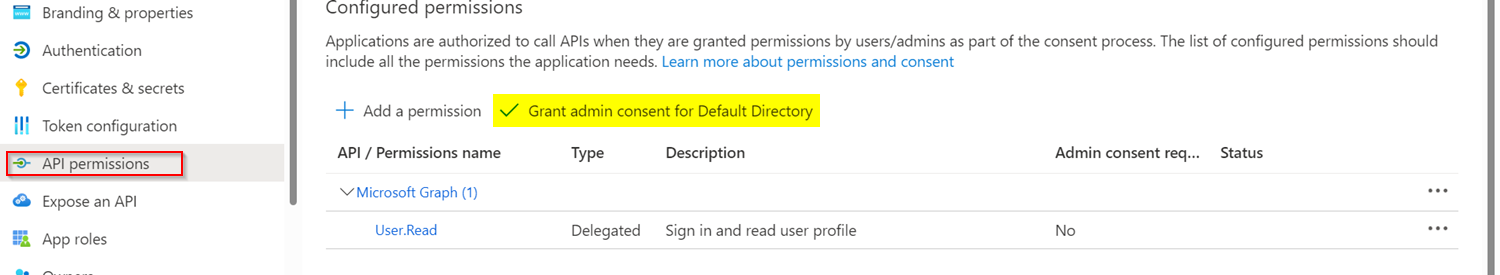
The error "Organisational admin needs to grant consent to access this application" usually occurs if the Admin Consent as not be granted to the Azure AD Application.
To resolve the error, Grant Admin Consent to the API Permissions as logging into the Portal as Global Admin like below: