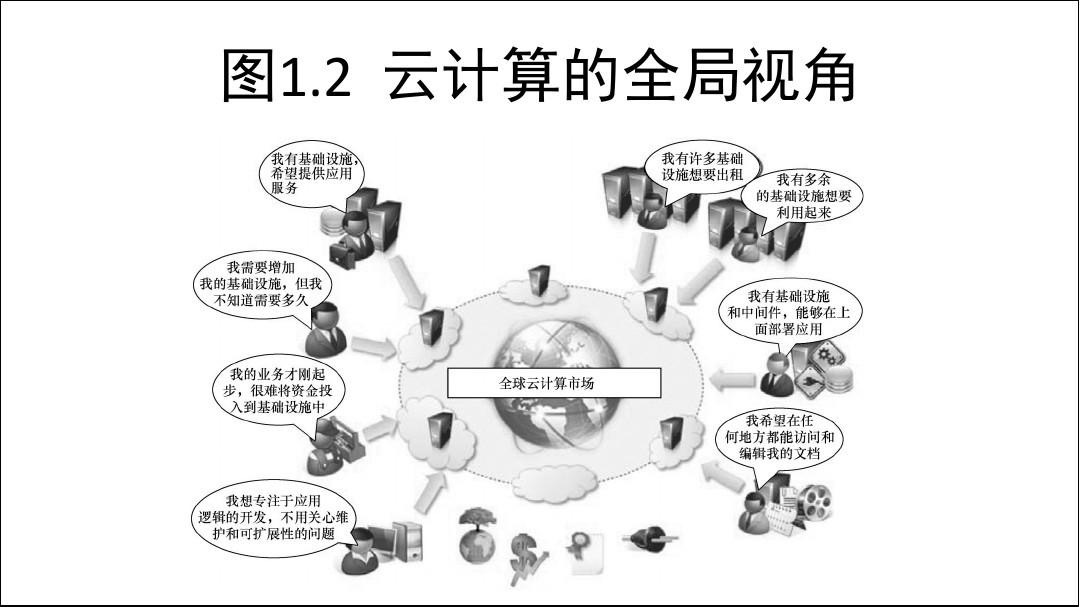
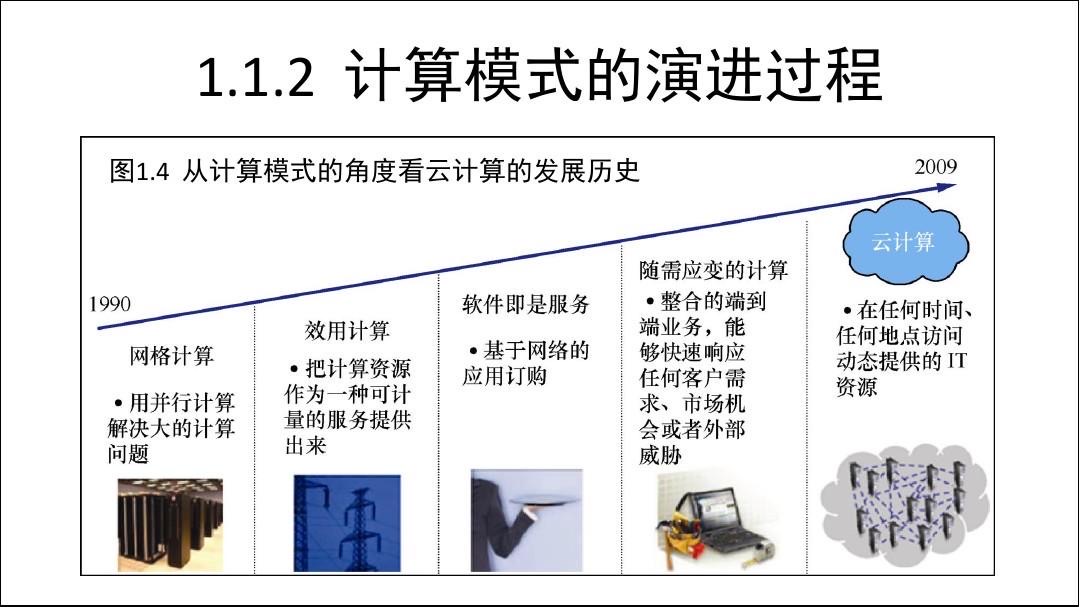
1.1 the origin of the cloud computing
With the rapid development of information and network communication technology, the computing model from the initial focus to large processor, gradually developed into more efficient distributed task processing mode based on network, since the 1980 s, the Internet rapid development, the increase of the related services based on Internet, and the change of use and delivery mode, cloud computing models,
1.2 the definition of cloud computing
Cloud computing is a kind of using the Internet to achieve anytime, anywhere, on demand, easy access to a Shared resource pool (such as computing facilities, storage devices, applications, and so on) of the calculation model, the cloud computing model is a basic characteristics: on-demand self-service, broad network access, Shared resource pool, the ability of rapid elasticity, measurable service, cloud computing deployment there are four ways: private cloud, the cloud, community public clouds, a hybrid cloud,
1.3 the classification of cloud computing
IaaS: IaaS is the foundation of cloud computing, for the upper computing services to provide the necessary hardware resources, under the support of virtualization technology at the same time, the IaaS layer can achieve on-demand configuration of hardware resources, create a virtual computing, storage center, so it can put the cell, memory, I/O devices, such as bandwidth computer infrastructure together, become a virtual pool of resources to provide services, virtualization is the key technology of IaaS PaaS: PaaS should not only provide reliable distributed programming framework for SaaS layer, and to provide resource scheduling for IaaS layer, data management, shielding the complexity of the underlying system and other support, at the same time the PaaS and his open software development platform as a service to the user, such as personalization of software development, SaaS: cloud computing requirements of hardware and software resources can be better sharing, has good scalability, any users can customize according to their demand and does not affect the use of other users, multi-tenant technique is a cloud computing environment can satisfy the demand of key technologies, and software resource sharing is a SaaS service purposes, the user can use the on-demand customized software services, through the browser to access the services required,
2. The key technology of cloud computing
2.1 architecture
Core services layer: the cloud computing core services are usually divided into three sub layers: IaaS, PaaS, SaaS, IaaS provide hardware infrastructure deployment services, to users as needed to provide physical or virtual computing, storage and network resources, such as PaaS is cloud computing applications running environment, provide application deployment and management service, SaaS is based on the cloud computing platform application development, service management, service management as the core service layer of availability, reliability and safety guarantee, user access interface layer: the user to access the interface layer for cloud computing services in access, data storage, data storage in cloud computing environment, often referred to as mass data storage, or large data storage,
2.2 data store
Cloud computing environment of data storage, often referred to as mass data storage, or big data storage,
数据中心: 实现云计算环境下数据存储的基础是由数以万计的廉价存储设备所构成的庞大的存 储中心,这些异构的存储设备通过各自的分布式文件系统将分散的,低可靠的资源 聚合为一个具有高可靠性,高可扩展性的整体,在此基础上构建面向用户的云存储服务, 分布式文件系统:分布式文件系统是云存储的核心,作为云计算的数据存储系统,对DFS的设计既要 考虑系统的I/O性能,又要保证文件系统的可靠性与可用性,计算模式:云计算的计算模型是一种可编程的并行计算框架,需要高扩展性和容错性支持, PaaS平台不仅要实现海量数据的存储,而且要提供面向海量数据的分析处理功能, MapReduce是Google提出的并行程序编程模型,运行于GFS之上,MapReduce的设 计思想在于将问题分而治之,首选将用户的原始数据源进行分块,然后分别交给不同的Map任务去处理,Map任务从输入中解析出键-值对(key/value)集合,然后 对这些集合执行用户自行定义的Map函数得到中间结果,并将该结果写入本地硬盘,Reduce任务从硬盘上读取数据之后会根据皱键值进行排序,将具有相同键值的数据 组织在一直起, 资源调度:海量数据处理平台的大规模性给资源管理与调度带来挑战,云计算平台的资源调度包括 异构资源管理,资源合理调度与分配等,虚拟化:云计算的发展离不开虚拟化技术,虚拟化技术可以将物理上的单台服务器虚拟成逻辑上的多台服务器环境,可以个性单台虚拟机的物理配置,每台虚拟机逻辑上可以被单独作为服务器使用,通过这种分割行为,将闲置或处于低峰的服务器使用起来,使数据中心为云计算提供大规模资源,通过虚拟化技术实现基础设施服务的按需分配,虚拟化是IaaS层的重要组成部分,也是云计算的重要特点,
Features: resource sharing, resource customization, fine-grained resource management,
2.3 Google cloud computing principle
GFS: web search business needs vast amounts of data storage, at the same time also need to satisfy the high availability, high reliability and economy requirements, to that end, Google has developed a distributed File System -- Google File System (GFS), graphs, to solve the large-scale parallel computing programming, data distribution and fault tolerance and Google's engineers to design a new abstract model graphs, simply execute simple calculation, at the same time can be hidden parallelism, fault tolerance, data distribution, load balancing and other details of clutter, BigTable: since Google many applications need to manage a lot of formatting and formatting data, the common characteristics of the above application is needed to support mass data storage and read after the master's analysis, data read operation frequency is greater than the update frequency of the data and so on, therefore Google developed a large-scale database System that could satisfy the requirement of weak consistency, BigTable, in view of the data read operation is optimized, the distributed data management model based on column storage to improve the efficiency of data read,
Some problems of cloud computing is:
1, data loss, this is due to the safety control of the data in cloud computing, API access control or key generation, storage and inadequate management, in addition, may also lack of necessary data destruction policy,
2, sharing technologies: due to the severe impact of the misallocation,
3, the use of certificates and certification system, the data reveal that often the source of security attacks such as simple identity authentication system, weak passwords and simple key or certificate system, and the working content change or leave the department often forget to remove the corresponding user rights,
4, mole: cloud computing service provider's internal personnel assessment is insufficient,
5, accounts, service and communication: a lot of data, applications and resources are concentrated in cloud computing, cloud computing authentication mechanism is weak, prone to invasion threat,
6, unsafe application interface: in terms of application development, the lack of strict enterprise audit process,
We do not have the right to use of cloud computing: 7, in terms of use, the operation of the technical personnel than hacking techniques,
The transparency of 8, unknown risks: long-term problems, has been plagued by cloud service providers, account user use only the front interface, they don't know what kind of platform or repair their suppliers use level,
9, account hijacking, phishing, fraud and software vulnerabilities in a cloud environment is still valid, using cloud services for an attacker to steal activities, business operation and modify the data thereby increasing attack, an attacker can also use other foreign attack by cloud services,
10, the APT parasite: CSA image analogy senior attack (APT) is a "parasitic" sustainable forms of attack, attack hidden into the system occupy a "points", slowly, for a long time the content of the small batch to steal data and other intellectual property rights,
11, the client issues: for clients, network cloud security concerns, there are some antivirus software after the broken network, performance is greatly reduced, and the actual application of thering is no lack of such a situation, due to a virus, such as network environment factors, once appear problem, in the network cloud instead became white elephants, help the pour,
According to various cloud security problem, and how should we solve? One of the most important is to properly identify security threats, research and development the right to eliminate the threat of solution, to keep pace with The Times, adapt to changing "cloud security threat,"
The solution:
1, a secret file is encrypted, effectively protect the data;
2, encrypted E-mail, effectively ensure the security of E-mail, let the intruder could not steal personal data by email;
3, use reputable providers of cloud services, effectively ensure the safety of cloud;
4, the use of automatic organization of sensitive data filter;
5, for the enterprise, should fully understand the internal private cloud environment and safety systems and procedures, and learn from experience;
6, for a variety of needs IT to support business process and importance of risk assessment;
7, fully understand the different cloud model (public cloud, private cloud and mixed cloud) and different cloud types (SaaS, PaaS, IaaS), because of the differences between them will directly impact on the safety control and safety responsibility, all enterprises should have corresponding views or strategy for the cloud;
8, strictly enforce the network security standard, fully protect the safety of cloud services,